Cyberattacks are being conducted daily on any type of target, and any notion that a state of full cyber security can be reached is a mere illusion. Cybersecurity is about managing risks and to ascertain that, to a certain extent, proper procedures and adequate security measures are being taken. Exposed …
Read More »Telecommunications is a critical infrastructure and needs to be protected from ever increasing cyber threats
Cyber-attacks are continuously growing in size and breadth, targeting organizations of all sizes across sectors, and telecom sector is no exception. According to PwC’s Global State of Information Security, 2016, IT security incidents in the telecoms sector increased 45% in 2015 compared to the year before. The rising danger posed …
Read More »European Union (EU) cyber security and EDA cyber defence strategy calls for proactive and reactive cyber defence technology and Cyber Situation Awareness (CySA) operational capability.
The pandemic, which moved citizens’ lives into the digital sphere, saw a rise in security breaches within European businesses and institutions. Cyber attacks against key European sectors doubled in 2020. Significant malicious attacks against key sectors doubled in Europe – up to 304 incidents compared to 146 in 2019 – …
Read More »DARPA MICEE to monitor and detect malicious activities in 5G/mobile infrastructure devices.
The New York Times reported that the US government has defined 5G competition as a “new arms race.” According to the report, “whichever country dominates 5G will gain an economic, intelligence and military edge for much of this century.” The transition to 5G is a revolution and “this will be …
Read More »DARPA EVADE to improve the cybersecurity of Military IoT/embedded devices
By 2025, it is predicted that there can be as many as 100 billion connected IoT devices or network of everyday objects as well as sensors that will be infused with intelligence and computing capability. These devices shall comprise of personal devices such as smart watches, digital glasses and fitness …
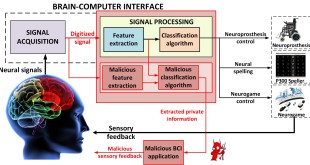
Read More »Brain-computer interfaces (BCI) are vulnerable to cyber attacks and need security and safety measures
Brain-Computer Interfaces (BCIs) are bidirectional devices that allow communication between the brain and external systems, such as computers. Every action our body performs begins with a thought, and with every thought comes an electrical signal. The electrical signals can be received by the brain-computer interface, consisting of an electroencephalograph (EEG) …
Read More »DARPA GECCO develop hackproof Military 5G communications
The New York Times reported that the US government has defined 5G competition as a “new arms race.” According to the report, “whichever country dominates 5G will gain an economic, intelligence and military edge for much of this century.” The transition to 5G is a revolution and “this will be …
Read More »Cyber Threats Targeting Food and Agriculture Sector (FA) and Cyber Security
Throughout much of the world, food and beverage safety and security is a high priority. Concomitantly, the economics, societal robustness, and security implications of agriculture, foodstuffs and beverages are massive. Extensive quality measures are in place to prevent and mitigate threats from manifesting; outbreak and contamination detection and response systems …
Read More »With Rising threat in Space domain from Electronic to Cyber Warfare, Space agencies enhancing Cyber security measures
Space is increasing becoming another domain of conflict due to enhanced militarisation i.e. utilisation of space systems by defence forces to support military operations as well as space weaponization with the proliferation of counter-space weapons. There are a variety of threats to space systems, from Direct ascent and co‐orbital anti-satellite …
Read More »Cyber Warfare threat driving Defense Cyber Security market and new security technologies
In 2019, 1,473 data breaches in the U.S. led to the exposure of 164,683,455 confidential records, as per the Identity Theft Resource Center (ITRC). Additionally, in May 2020 alone, 841,529 records were exposed in 108 data breach incidents. The records ranged from people’s financial and medical information to strongly protected …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis