Space is increasing becoming another domain of conflict due to enhanced militarisation i.e. utilisation of space systems by defence forces to support military operations as well as space weaponization with the proliferation of counter-space weapons. There are a variety of threats to space systems, from Direct ascent and co‐orbital anti-satellite weapons, Directed energy attacks, Electronic warfare such as jamming of communications, command and control systems / links.
The most recent threat to space systems is Cybernetic attack on space systems. Like any other increasingly digitized critical infrastructure, satellites and other space-based assets are vulnerable to cyberattacks. These cyber vulnerabilities pose serious risks not just for space-based assets themselves but also for ground-based critical infrastructure. If not contained, these threats could interfere with global economic development and, by extension, international security.
Adversaries that could include very sophisticated criminal groups, nations, or at times, even high-end amateurs could take action that deny services that business, academia, and the public depend on,” says Bob Gourley, founder of Ooda.com . “Since our systems are so interconnected there is also a huge threat that automated malicious code will one day make its way from corporate IT systems into ground stations and from there to space components.”
Rising Cyberattacks
Just as space services are central to modern-day life, they also support essential services such as military, utilities, aviation, and emergency communications. This makes them particularly attractive, especially at times of geopolitical unrest, for cyberattacks, the impact of which is unpredictable.
In 2022, we saw that cyberattacks on satellites servicing one country could disrupt critical national infrastructure in another. In February 2022, just as the Russian invasion of Ukraine started, a large number of satellite modems in Ukraine and elsewhere in Europe were subject to a cyberattack and disabled, requiring global operator Viasat to do a hard-reset following which it could continue to deliver vital communication, including to Ukrainian refugees in neighboring Slovakia. In March 2022, SpaceX sent thousands of Starlink satellite internet terminals to Ukraine to provide Ukrainian citizens access to communication.
The conflict in Ukraine has nonetheless demonstrated that space has been and will continue to be extremely relevant at times of geopolitical conflict. As these trends are likely to continue, we will see new threat actors, targeting space systems to impact the critical services enabled by satellites.
In the 2011 report by the US-China Economic and Security Review Commission, it revealed several attempts to breach into a US-Geological Survey Earth-imaging satellite, Landsat-7, and NASA climate change sensors, Terra AM-1. Although no damage was inflicted into both satellites, the cyber criminals were able to achieve all steps necessary to command the satellites. In a 2014 paper by IOActive, a US-based cyber-security firm, it has reported several vulnerabilities in existing satellite communication terminals used by commercial, government and military operations. The forensic study has found multiple potential hacker entry points.
The report further said that China’s People’s Liberation Army(PLA) continues to develop technologies to “blind and deafen the enemy”. The report asserted that China has the capability to conduct cyberattacks at ground stations with the intention to corrupt or hijack systems to control satellites including spacecrafts. The report comes at a time ( Sep 2020) when India and China have been engaged in a standoff at the Line of Actual Control(LAC). In fact, newswire ANI had earlier quoted defence sources saying that Indian security officials want four to six “dedicated satellites” to keep a close eye on Chinese activities along the LAC.
According to the US-based China Aerospace Studies Institute (CASI), China carried out several cyber-attacks between 2007 to 2018, including computer attacks against Indian satellite communication in 2017. However, ISRO has maintained that none of the systems have been comprised while acknowledging the cyber attacks. The report said China has several counter-space technologies to threaten space systems from geosynchronous orbit (GEO). India had earlier demonstrated anti-satellite missile technology capabilities in 2019 which allows the country to “kill” rogue or enemy satellites.
In 2020, the UK followed the US’s 2019 Space Force example, announcing a Royal Air Force Space Command capable of launching Britain’s first rocket in 2022. And when, in November, the US Marine Corps activated a Marine Corps Forces Space Command, we had visions of an Aliens-style expedition eliminating adversarial xenomorphs.
“We recognize that as cyber warfare and hybrid threats become the weapon of choice for state and non-state actors, and the global economy and daily life grow increasingly dependent on space systems […]” said Maj. Gen. Kimberly Crider, Space Force chief technology and innovation officer. These space systems, she said, could well become the “next front of the cyber conflict.”
Space system Vulnerabilities
Once effectively isolated, and so protected, from outside intrusions, SATCOM networks today have largely completed the transition from circuit- to Internet Protocol based technology, as integral parts of broader networks operated by the Department of Defense and industry. With that shift have come not only improvements in efficiency and interoperability, but also greater potential vulnerability to the advanced, persistent and apparently state-supported cyber-attacks that have become increasingly pervasive, writes MIT Editor Harrison Donnelly.
Satellite communications networks consist of user terminals, satellites and a ground network that provides control and interface functions. All three elements are vulnerable to cyber-attacks. Ground systems are the most vulnerable weak points in a hierarchy that starts with the TT&Cs/Satellite Operations Centers (SOCs) and flows down through the Network Operation Centers (NOCs) and gateways, teleports, and earth terminals. Furthermore, adoption of large satellite constellations is driving the number and complexity of ground control and service support infrastructures, thereby increasing the potential attack surface.
All the four main segments of space infrastructure are vulnerable to cyber attack. Spacecraft could be vulnerable to command intrusions (giving bad instructions to destroy or manipulate basic controls), payload control and denial of service (sending too much traffic to overload systems). Malware could be used to infect systems on the ground (like satellite control centers) and for users, and links between the two and spacecraft could be spoofed (disguising communication from an untrusted source as a trusted one) or suffer from replay (interrupting or delaying communication by malicious actors).
Formerly, satellite systems used to be very stand-alone and isolated, relying on the ‘air gap’ as their security mechanism, however air gap mechanisms now have been shown to be breached. The then commander of Air Force Space Command, General John E. Hyten, told Congress in 2016 that “adversaries are developing . . . cyber tools to deny, degrade, and destroy” U.S. space capabilities that support war fighting, critical infrastructure, and economic activity.
Ouroboros, one of the world’s most sophisticated hacking groups with close ties to the Russian government, has been accused of hijacking unencrypted commercial satellite communications. They use hidden receiving stations in Africa and the Middle East to hide their Control & Command servers and mask attacks on Western military and governmental networks.
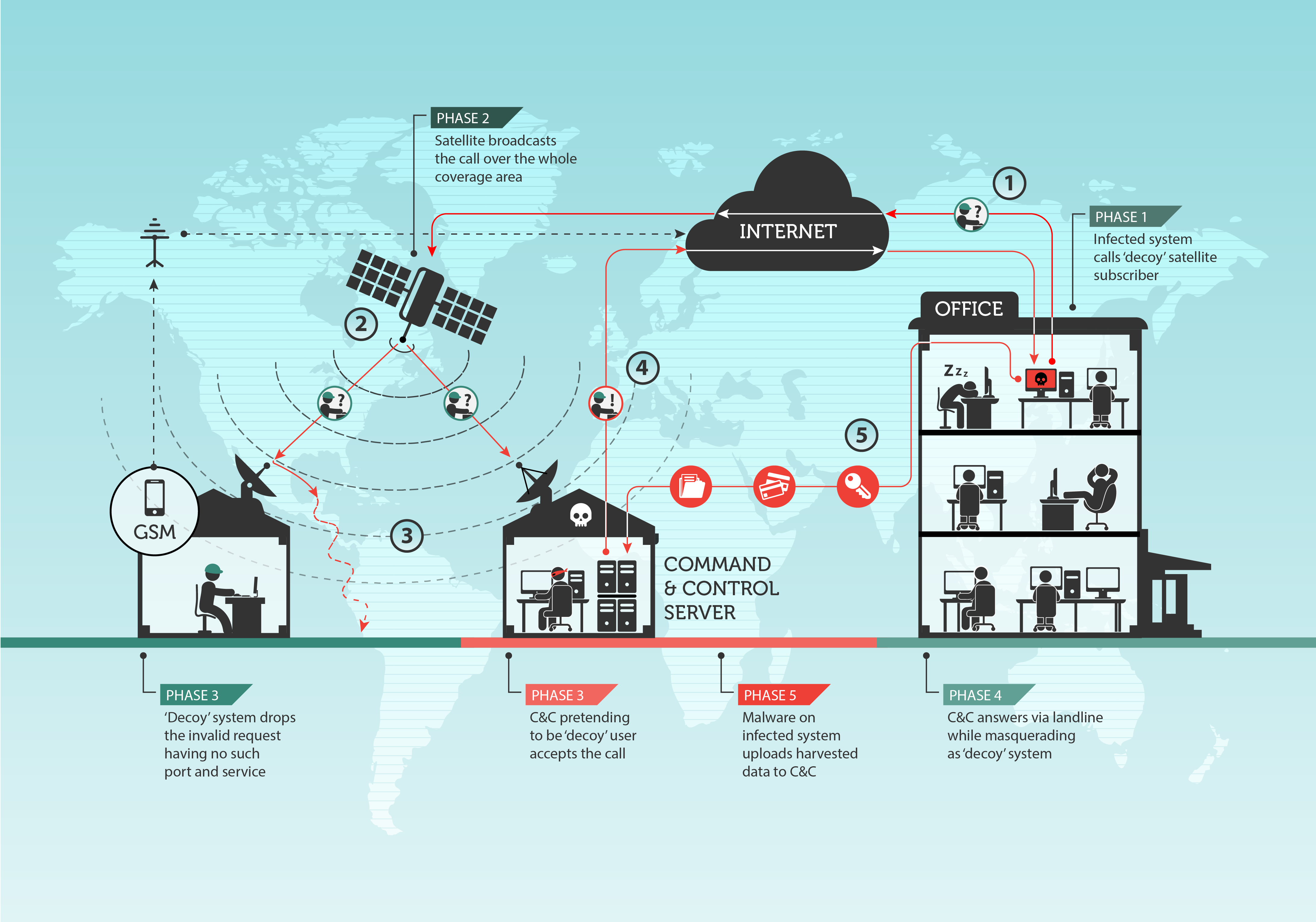
In a report by Kaspersky released in Sep 2020, they said they had identified a new “exquisite” attack channel being used by the group that was virtually untraceable. The need for hackers to communicate regularly with machines they have compromised allows security researchers to trace back the hackers’ Command & Control servers. “This method makes it almost impossible to discover the physical location of these C&C servers,” said Stefan Tanase, senior security researcher at Kaspersky. “Safe to say this is the ultimate level of anonymity that any cyber espionage group has reached in terms of hiding its origins.”
The Ouroboros satellite hack exploits the fact that most satellite communications being sent from satellites back to earth are unencrypted, and so can be spoofed. The process is laid out by Kaspersky in a large illustration and follows a number of steps. The request from Ouroboros is then automatically routed via a commercial satellite and beamed to earth towards the location of the decoy. Once the decoy server receives the request for instructions, it discards it, because the request is meaningless to it.
But the satellite will have beamed the request over a large geographical area. A hidden receiver anywhere in the area, planted by Ouroboros’ operators, can then pick up the unencrypted request. The receiver then issues a reply to Ouroboros, disguised as a communication returning from the decoy. This way, any defender looking to trace communications from Ouroboros back to its controllers will lose the trace from the point at which the data becomes a signal beamed from a satellite, effectively breaking any direct digital link. Ouroboros’ handlers are using satellite operators in the Middle East and Africa. Finding the receivers depends on the size of the dish, but it’s a needle in a haystack because the area could be tens of thousands of square kilometers.
“The receivers do not necessarily cost much themselves but finding a physical location for these indicates that there is some kind of extensive logistical support network,” Kaspersky said. Such operations point to a state intelligence service, he added. For the moment, satellite operators are powerless to prevent the hackers from routing requests through their networks until they encrypt all of their downstream communications, which would cost hundreds of millions in new satellite arrays. Western security officials have previously stated that Ouroboros is a Russian operation, a fact supported by the group’s targets and reverse engineering of the malware itself. What else is new for “once-a-spook-always-a-spook” Vladimir Putin.
Although technically possible, the resources required to attack the telemetry, tracking, and control (TT&C) communications links or the satellites themselves from the ground, are likely to be significant. This type of attack is most likely to be restricted to nation state actors. However, it is much easier to trick the people with legitimate access to the control infrastructure (via social engineering or phishing attacks) into unwittingly providing systems level access to hackers attacking over the internet.
James Turgal, managing director, sees the main areas of concern as the human factor and the supply chain. He said there is no question that cyber vulnerabilities exist and are exploited because of the human factor. “Cyber risk and cybersecurity is more about people behind keyboards than it is about technology. The human factor; either someone engaging in an activity (witting or unwitting) on behalf of a cyber threat actor. Or, the omission of action (intentional or unintentional) such as patching, misconfiguration of systems; all of these factors can allow a gap to form which can be exploited by a threat actor,” he says. When talking about supply chain vulnerabilities, Turgal says that because satellites and systems are made from thousands of parts manufactured in places both inside and outside the U.S., vulnerabilities can be built in by threat actors — which can cause greater levels of access to the satellite system as a whole.
Added to this is the complexity introduced by third-party relationships. As satellite-based service infrastructures become more complex and evolve into full end-to-end services, they involve more stakeholders operating different parts of the infrastructure. The supply chain for hardware and software is dependent on multiple component parts, making it difficult to identify responsibility and liability for the ultimate security and resilience of the services supplied. Where do the roles and responsibilities of hardware manufacturers, software developers, satellite manufacturers, operators and commercial users begin and end?
NASA’s chief information security officer, Jeanette Hanna-Ruiz, had warned that “it’s a matter of time before someone hacks into something in space.” Chatham House’s David Livingstone asserted that “people are just shuffling . . . paper around” and suggested that only “a disaster” might catalyze serious action. Josh Hartman, a former senior Pentagon official and Air Force officer, argued before the satellite industry’s first cybersecurity summit held in 2017 that, on cybersecurity, “most of the space community . . . has their heads in the sand.” The “attack surface” of space activities is expanding, but governments and industry are not taking adequate action.
Hacking of Satellite Antenna to carry EW and Electronic attacks
Ruben Santamarta, a researcher for the information security firm IOActive, presented one scenario at the Black Hat information security conference in Las Vegas, wherein hackers could take control of satellite communication systems that ships, planes and the military use to connect to the internet. They could leak information and in the worst-case scenario, could carry out “cyber-physical attacks”, turning satellite antennas into weapons that operate, essentially, like microwave ovens.
“We’re basically turning Satcom devices into radio frequency weapons,” Santamarta said. “It’s pretty much the same principle behind the microwave oven.” Even if the antenna can’t be used to physically injure soldiers, passengers or crew, a HIRF attack can also cause physical damage to electrical systems.
Both military and maritime users are also at the risk of what Santamarta described as “cyber-physical attacks”: repositioning the antenna and setting its output as high as it will go, to launch a “high intensity radio frequency (HIRF) attack”. The attack works by connecting to the satellite antenna from the ground, through the internet, and then using security weaknesses in the software that operates the antenna to seize control.
From there, the potential damage varies. At the very least, the attack offers the ability to disrupt, intercept or modify all communications passed through the antenna, allowing an attacker to, for instance, eavesdrop on emails sent through an in-flight wifi system, or attempt to launch further hacking attacks against devices connected to the satellite network.
And in some situations, the safety risk is higher still. In the case of the military, for instance, the attack also exposes the location of the satellite antenna, since they usually need an attached GPS device to function. “If you can pinpoint the location of a military base, that’s a safety risk,” Santamarta noted, “but not for a plane or a ship”, whose locations are generally public.
The safety risk is not as high for the aviation sector, Santamarta said, because planes tend to be built with a significant amount of HIRF shielding in place. “The industry has done a good job of putting strong design and testing standards in place that would protect critical flight systems from HIRF attacks using airborne Satcom equipment,” Santamarta writes in his report, adding that it “should be commended for identifying an emerging threat”.
Smallsats Threats and Vulnerabilities
The threat has also increased due to increasing use of military of LEO commercial space constellations which may not be adequately protected against cyber attacks.
Advances in miniaturisation and the proliferation of space technologies have created opportunities to enter space with small, lightweight, inexpensive and highly capable miniaturised satellites. Microsatellite or “microsat” is usually applied to the name of an artificial satellite with a wet mass between 10 and 100 kg. The term “nanosatellite” or “nanosat” is applied to an artificial satellite with a wet mass between 1 and 10 kg. LEO satellites provide agencies with additional advantages because they move at a quicker rate and have lower latency due to their location in orbit, which helps agencies communicate more quickly to citizens and warfighters.
Nevertheless, all satellites have a complex structure and the various systems and programs required for operation—navigation, communications channels, onboard sensors, power generators—create a vast attack surface. And because these systems and components must work in harmony, it’s often nearly impossible to isolate or combat a threat without compromising the entire ecosystem. The world has already seen several instances of satellite interference by governments executing cyberattacks and blocking communications including jamming and spoofing capabilities in the ongoing conflicts in Syria and Ukraine by Russia.
“Certainly, an increasing number of satellites in orbit creates an increased likelihood of an attack, as there are more targets of opportunity, more ground facilities that need to be secured from what I consider as the new threat which is the convergence of the cyber and the physical security worlds, ” James Turgal, managing director, Cyber Risk Services at Deloitte .
Crystal Lister, senior director of insider and cyber threats, GPSG, believes the number of satellites going up does not necessarily increase the likelihood of a major attack. But, rather, it increases the size of the attack surface that security teams must defend. She says, “Inconsistent software patching, weak encryption, and old IT equipment are key vulnerabilities to satellite networks. Legacy satellite communications platforms are not easily updated and must undergo significant testing to ensure that upgrades for communications, encryption, or improved operability with next-generation platforms will not interfere with other, possibly critical, system functions.”
Bob Gourley, founder of Ooda.com, says that because the software on satellites is designed by humans, this will mean it will have flaws that are not discovered till the systems are on orbit. “It is hard to keep Earth-based systems patched, just think of how hard it is to safely keep on-orbit systems patched! This means space-based systems will always have vulnerabilities that need to be mitigated,” he says. “Most all our satellites are designed to send and receive data. That is how they are controlled and how they pass value back to the earth. By their very nature they must be connected. This means we will always need to be on the lookout for vulnerabilities to mitigate.”
Andy Davis, transport assurance practice director, the NCC Group, highlights vulnerabilities in the small satellite sector, which is expanding quickly. He highlighted the fact that because the investment required is reducing due to cheaper Commercial Off The Shelf (COTS) hardware, open source software and new initiatives such as Ground Stations-as-a-Service, this increases the likelihood of a cyber-attack significantly. “The attack surface of the assets based in orbit and their associated ground-based support infrastructure has increased and will continue to increase significantly,” he says. “The two main threats are to ground station infrastructure and to the open source software and COTS hardware, installed on-board satellites. By far the easiest of these to attack is the ground-based infrastructure, which will be internet-connected and operated by humans (who are much easier to ‘hack’ than computers, via social engineering and phishing attacks).”
Kurzrok and colleagues at Stanford University and the University of Colorado modeled several different propulsion systems on a notional 10-kilogram nanosatellite, assuming the spacecraft was in a 300-kilometer orbit and that the propulsion systems accounted for half the spacecraft’s mass. The results ranged from the satellite reaching medium Earth orbit altitudes within two hours when using chemical propulsion to passing geostationary orbit in about a year with an electric propulsion system.
The scenario in the first case is troubling. This is because hackers can easily take control of a satellite and redirect it quickly. Government satellites and many commercial ones have security that makes it difficult to get hacked. But, many lack this security. This could have serious implications. “What are the abilities within two hours to track that something isn’t where it’s supposed to be and then warn or take some sort of secondary action?” he said, concluding that the satellite reaching GEO in a year is a much less plausible threat.
There’s been no known case where a smallsat with propulsion has been hacked, but Kurzrok suggested it may be only a matter of time. “If something can be hacked, eventually it will be hacked,” he said, based on cybersecurity experiences in other industries. That has serious implications, even in the scenario where the hacking event does no damage to the satellite or other space objects. “The reputational costs to the industry could be significant.”
That recommendation comes as cubesat developers, who once had few, if any, options for onboard propulsion, are now looking to make use of more advanced chemical and electric propulsion systems. Some of those technologies can provide smallsats with large changes in velocity, which can enable major orbital changes. That led to his recommendation that small satellites with propulsion be required to have encrypted command systems. That could be done through industry self-regulation, with launch providers ensuring that the satellites they launch comply with this rule, or provisions in contracts by satellite propulsion providers requiring their systems only be used on satellites with encrypted communications systems.
Ron Clifton, founder of Clifton Associates and satellite industry veteran, says the low orbit of the Low-Earth Orbit (LEO) satellites will mean they are more accessible than the Geostationary Orbit (GEO) satellite, from an RF power perspective. The satellites may have their own kind of denial of service vulnerabilities, but Clifton believes the kind of modulation and encryption technologies available today should help mitigate this significantly.
He adds, “It is also worth thinking about these new LEO constellations as a form of internet backbone — essentially an interconnected set of routers flying around the earth at high speed and exchanging broadband data with each other and with ground assets. Although all the lessons learned from protecting terrestrial IP networks will apply, there are some challenges unique to this emerging ‘Internet in the sky.’ Like terrestrial IP networks, the LEO networks will experience maintenance outages and require occasional maintenance windows for updates with backdoor access for ongoing support and development of enhancements.”
In the future, consumer services will move across terrestrial and space systems as technical standards for integration of NTNs with terrestrial networks are implemented. As an example, mobile phone signals may switch seamlessly from ground-based tower signals to satellites without citizens noticing the transition. These technological changes will increase interdependencies between satellites and technologies on Earth.
Air Commodore Julian Ball OBE, head of defence space capability at the UK Ministry of Defence, said: “A major barrier today is when people look to deliver digital transformation, they still default to thinking about the hardware first. In the space context, everyone will straight away start talking about how we can optimise the satellite. But it’s not about the hardware, it’s about the data that runs behind it.
“What I’m interested in is how we can get the information from the satellite to the ground and the end-user safely and securely. We therefore need to optimise the data-management layer first before we start thinking about developing sensors or getting the ship into space. Satellites are useless if the data isn’t doing its job. It’s the ability to use and understand the data in a meaningful way that will deliver digital advantage.”
Cyber attack impact
Much of the world’s critical infrastructure is heavily dependent on space, specifically space-based assets, for its daily functioning. Essential systems — such as communications, air transport, maritime trade, financial services, weather monitoring and defense — all rely heavily on space infrastructure, including satellites, ground stations and data links at the national, regional and international level. This dependence poses a serious, and yet frequently underrecognized, security dilemma for critical infrastructure providers and policymakers alike.
Foe example, a successful attack on telecommunications satellites can lead to unthinkable scenarios such as a massive disruption in communications, espionage, jamming and even commandeering satellites to collisions. It may not seem obvious but life in this planet has become so reliant on satellites that any major breach can cause havoc.
The shift in focus towards a more comprehensive cybersecurity network follows a government report released in April outlining the increasing need for personnel amid a heavier reliance on IT networks and services. Attacks such as the denial of service (DDoS) could be as devastating to a satellite constellation as a direct kinetic attack, Thompson said: “Loss of control of these constellations really could be catastrophic from a mission perspective or from a satellite tumbling out of lower earth orbit perspective.”
Cybersecurity measures
US government has released Space Policy Directive 5 to offer the US Government’s comprehensive cybersecurity policy principles for space. Militaries have started setting up Space commands for effective offensive and defensive operations in Space domain. “The US Space Force was established in December 2019 and is exploring AI-enabled cyber defence solutions for its 180 space mission systems. Space-based assets are vulnerable to distributed denial of service attacks or hijacking via cyberspace. Space and cyberspace are intrinsically intertwined.
Risk Assessment
The SATCOM industry is responding by ramping up efforts to comply with security standards, such as those developed by the National Institute of Standards (NIST), and introducing new products and services, such as a recently announced satellite cybersecurity assessment service.
Risk in this sector is colliding at the nexus of an increasing amount of satellites being launched in parallel with society’s increasing reliance on satellite-dependent technologies. Both large and small satellite companies alike should make a concentrated effort to determine their risk tolerance. Lister says, “You cannot prevent targeting of your systems or attempted attacks. You can seek to prevent, detect, and respond to incidents. Acknowledge the threats to your unique critical assets, evaluate your security posture, identify any vulnerabilities, and pursue risk mitigation strategies to enhance your defenses. It will be critical that IT and OT teams in the satellite sector work from the same business continuity or disaster recovery playbook when an incident does occur to contain the event efficiently and minimize negative impacts.”
There are a number of space cybersecurity standards and a few regulations that already exist, including the Committee on National Security Systems’ information assurance standards for commercial satellites that carry classified or otherwise sensitive data and the National Oceanic and Atmospheric Administration manages licensing for commercial remote sensing satellite systems, which includes information assurance requirements.
One of the first things required is risk assessment. Clifton has some advice for new comers to the industry. He says, “For the newcomers, again I strongly suggest they adopt the NIST Cybersecurity Framework and put an active set of physical and cyber controls in place if they have not already done so — either the full set defined in ISO 27001 or, for less demanding applications, a more tailored set such as the top 20 controls defined by the Center for Internet Security (CIS). Bottom line, there is no substitute for experience, rigorous attention to established protocols, and vigilance.”
The key thing is to do a deep dive on where you stand relative to your risk posture across the spectrum, from end to end,” said Christopher Fountain, senior vice president of Kratos’ SecureInfo. “We advocate a robust assessment of risk, leveraging the control frameworks that are being required by systems used by the government and Department of Defense,” he said.
Cybersecurity Solutions
Historically, the majority of satellites can be thought of as bent pipes in space (meaning that the uplink signal is received, amplified, translated to a downlink frequency, amplified again, and directed toward the earth using a high-gain antenna). They received data from Earth, such as TV signals, amplified them and mirrored them back down to Earth. They are now becoming more complex with the advent of software-defined satellites. Satellites are built to be resilient and robust and can function in isolation from each other. They are connected to private networks which are not per se accessible from the Internet. The arrival of software-defined satellites means that satellites can be reconfigured in space, allowing space-based services to be adjusted in response to changing demand and respond dynamically to threats as they emerge.
“Space-based assets like satellites rely on cyberspace links for the flow of data to and from them linking command, control, communications, computers and intelligence, surveillance, reconnaissance systems. They not only provide crucial cyber ISR but are also capable of delivering offensive cyber effects. Cybersecurity solutions for space are first and foremost software-driven as air-gapped solutions or bringing down a satellite for upgrades is not an option. “As military powers are standing up space forces and commands, tailored cybersecurity solutions, perhaps AI-enabled, for use in space that take into account the specific nature of this domain (for example, high radiation levels) will increasingly be sought after in 2021.”
To address the increasing threats and unique requirements of the satellite industry, Kratos recently introduced the SATCOM Cybersecurity Assessment service. With cybersecurity legislation expected soon to require the application of NIST information assurance standards for all U.S. critical infrastructure, including satellite communications, company executives note, the assessment will help ensure compliance readiness for these forthcoming security regulations.
As part of the response, technologies will include GPS anti-jamming solutions and Protected Anti-Jam Tactical Satcom (PATS). Meanwhile, military procurement events and programs will be introduced to enable personnel to acquire capabilities from non-traditional vendors. That includes methodologies like DevSecOps in software development, said Crider, where software testing is integrated as a continuous process throughout development code as it’s deployed into production.
In addition, RT Logic, a Kratos company, offers CyberC4, its family of products for the SATCOM environment that deliver situational awareness, system hardening, insider and external threat protection, and active defenses. Components include CyberC4:Alert,which it bills as the first Security Information Event Management system specifically for satellite networks; CyberC4: Armor, which provides anti-tamper protection for mission-critical devices used in satellite ground networks; CyberC4:Capture, which counters insider threats; and CyberC4:Guard, a cross-domain solution for controlling the transfer of information between different security levels.
Securing satellite systems is a priority that must not be limited only to military-grade satellites. With cyber criminals now becoming more aggressive, proper countermeasures must be put in place. Useful countermeasures to safeguard satellite architectures are the encryption of data and the hardening of the satellite’s every single component, including ground stations. Data encryption protects the signals from spoofing attacks as well as attempts to eavesdrop.
Turgal said even though the satellite industry is moving fast, building cyber and human focused security measures into the systems from their inception, good cyber hygiene, limited privileged access, clean supply chain and third-party governance and an understanding and appreciation of the cyber-physical security convergence that needs to take place to protect these systems and assets will be key.
In addition, key government programs such as the Defense Information Systems Agency/General Services Administration’s Future COMSATCOM Services Acquisition program are featuring enhanced information assurance requirements.
Satellite operators also are moving to address cyber- and related security concerns. Intelsat General, for example, offers round the-clock monitoring and proactive security in the Intelsat Secure Operations Center, defense-in-depth design and delivery from IA experts, operations support at each teleport, and emergency response teams.
“IP-based networks raise the risk level for cyber-threats, so we take a number of precautions to make sure that our network and customer services stay safe. The risk applies across the board, possibly affecting network operations, network infrastructure, IT infrastructure, and flight operations. So it is an area that Intelsat takes very seriously, with a world-class cyber-protection program in place,” said Mark Daniels, vice president of engineering and operations for Intelsat General.
“Intelsat has taken all of the information assurance standards that are out in the market for both commercial and government networks and applied the most stringent parts of those across the Intelsat network to make sure it’s been hardened against cyber threats.We’ve been very successful with this approach. It includes third-party penetration testing, where we hire someone to try to break into our network, to certify that we don’t have any holes,” Daniels said.
Part of the information assurance process that the company goes through on government contracts involves certifying that it is adhering to the required levels of security, including encryption of the command signals sent to satellites. Most of Intelsat’s satellites are designed with that capability, which gets turned on when a government task order requires it.
“Security is absolutely important to our business and customers,” Daniels said. “In protecting ourselves from cyber-threats, we use a defense-in-depth approach to protecting the network. It’s a multi-layer approach that protects the IT infrastructure through a hardening of our systems, as well as physical security at our teleports and offices.”
Building Resilience
Once an adversary has gained access to a satellite’s system, it’s easier for the bad actor to follow the communications path between a satellite and its “home base,” gain entry and infiltrate networks and systems up the chain. To ensure that an attack is prevented or mitigated, agencies should emphasize resilience and implement forward-looking technology solutions. Resilience is the best bet to ensure mission continuity and support rapid reconstruction of existing capabilities—or deployment of an alternative. Resilience uses cyber threat intelligence to guide decisions, support agility and evaluate acceptable risk. Most agencies can achieve resilience simply by following current federal standards (including National Institute of Standards and Technology guidelines) and analyzing the data they are collecting from adversaries. Additionally, agencies can train their workforce to respond to attacks and test satcom systems for vulnerabilities.
In addition to building resilience, the emergence of a virtualized architecture is poised to fundamentally change the satcom industry in 2020. Transport virtualization allows users to seamlessly switch between waveforms and operate across networks, bands, satellites, orbits and constellations with commercial-off-the-shelf hardware. This capability will simultaneously address readiness, resilience, agility, logistics and operations while allowing satellites and their communications to hide in plain sight.
Transport virtualization will strengthen cybersecurity in satcom by increasing user visibility—allowing threats to be identified and isolated quicker so that an affected program can be frozen, and attackers won’t be able to spread. In addition, virtualization will solve major connectivity challenges, allowing agencies to connect to satellites at different bands and orbits, effectively changing connection without having to switch between proprietary hardware and software.
The Catalyst Accelerator Unveils Next Cohort: Cyber for Space Applications
The Catalyst Accelerator (CA) announced its next cohort, Cyber for Space Applications, launching September 1, 2020. The goal of the CA is to increase Space Force awareness and rapid acquisition of commercial, dual-use space technology by providing relevant business development training to Accelerator companies and connecting these entrepreneurs with users, decision makers, and potential new customers in the DoD and commercial realms. Eight companies will be chosen to participate in the program held at Catalyst Campus in Colorado Springs, Colorado. “How might we apply cyber technologies to secure the next generation of space operations and increase resiliency?” the problem statement poses.
KiMar Gartman, the Catalyst Accelerator Program Director, states, “We are excited to assist the Air Force and Space Force in finding companies with unique cyber solutions that will secure the next generation of space operations and increase resiliency. We look forward to collaborating with our dynamic space community to offer the very best program possible!” Captain Keith Hudson, Government Lead for the Cyber for Space Applications cohort, stated, “As we face increasing cyber resiliency challenges in space, the upcoming Accelerator provides an opportunity for the USSF and AFRL to connect with small businesses to develop the necessary solutions to those challenges.”
References and Resources also include:
http://www.kratoscomms.com/~/media/networks/pdf/cyber%20threats%20in%20space.pdf?la=en
http://interactive.satellitetoday.com/the-growing-risk-of-a-major-satellite-cyber-attack/
https://blog.knowbe4.com/expert-russians-hackers-use-satellites-to-hide-amazing-exploits
 International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis