Cyber-attacks are continuously growing in size and breadth, targeting organizations of all sizes across sectors, and telecom sector is no exception. According to PwC’s Global State of Information Security, 2016, IT security incidents in the telecoms sector increased 45% in 2015 compared to the year before. The rising danger posed by cyberattacks on critical national infrastructure was evident again in May 2021, when a small group of hackers launched a ransomware attack on Colonial Pipeline, the United States’ largest pipeline network for delivery of refined petroleum products. Colonial shut down its main lines for five days, disrupting nearly half the fuel supply for the eastern part of the country. Worried drivers drained supplies in gas stations in the Southeast, airlines rerouted flights to airports with available fuel, traders were rocked by unexpected price volatility, and logistics companies scrambled to locate new sources of fuels.
Telecoms providers need to arm themselves against this growing risk. The telecommunications industry keeps the world connected. Telecoms providers build, operate and manage the complex network infrastructures used for voice and data transmission – and they communicate and store vast amounts of sensitive data. This makes them a top target for cyber-attack.
Telecoms companies, their core infrastructure and the large volumes of personal data they hold on subscribers, all represent an obvious target for malicious actors. Compared to other industries, telecoms companies are expected to be tech-savvy and often have a large consumer-facing footprint. This creates heightened reputational risks.
Telecommunications is a critical infrastructure and needs to be protected accordingly. The threat landscape shows that vulnerabilities exist on many levels: hardware, software and human, and that attacks can come from many directions. Telecoms providers need to start regarding security as a process – one that encompasses threat prediction, prevention, detection, response and investigation.
The chances of cyber attacks trained at telecommunications satellite is also increasing with cyber criminals now becoming bolder and more equipped. A successful attack on telecommunications satellites can lead to unthinkable scenarios such as a massive disruption in communications, espionage, jamming and even commandeering satellites to collisions – to name a few. According to the Union of Concerned Scientists (UCS), there are 1,459 operating satellites orbiting the space, more than half of which are communications satellites. Of this number, around 38% operate for commercial communications and another 16% for government communications.
In recent years, the industry has experienced a fundamental transformation with the developments of network technologies, most recently 5G network technology. This has also given rise to new vulnerabilites and cyber attacks. Telecom providers will also have to deal with threats surfacing from IoT-enabled devices as they roll out 5G which will lead to a surge in usage of data. Cloud too is vulnerable to threats. While cloud has been in existence for more than a decade, not many enterprises have given much thought on how to ensure that they are secure.
Cyber Threats Directed at Telecoms Companies
Telecommunications providers are under fire from two sides: they face direct attacks from cybercriminals intent on breaching their organization and network operations, and indirect attacks from those in pursuit of their subscribers.
Catastrophic attacks on a major mobile network operator by targeting its core. These include DDoS attacks, targeted attacks (APT campaigns), network device vulnerabilities and human-related threats like insider access, social engineering and the risk of allowing third parties to access information. Mobile network operators are not properly prepared for such attacks, and the core of 3G and 4G networks is generally not protected.
There are also supply chain risks. In August 2018 Australia made the call to block the Chinese telecom giants from supplying equipment to the nascent Australian 5G network. Mike Burgess, the director-general of the Australian Signals Directorate, said that the ban on Chinese telecom firms like Huawei Technologies and ZTE was in Australia’s national interest and would protect the country’s critical infrastructure.
DNS Attacks
DNS (Domain Name Security) attacks still remain a major sore point for telcos. What’s worse, the cost of such attacks is increasing year-over-year. In 2017, one attack cost a telecom company $622,100 on average. In 2018, the figure rose by 42% and reached $886,560 on average. To a large extent, this drastic increase can be attributed to slow response time: on average 3 employees need 17+ hours to mitigate such cybersecurity threats.
Another report from 2018 indicates that telecom providers had the highest volume (30%) of sensitive customer information stolen through DNS attacks when compared to healthcare, banking, education, and public services sectors. In general, 43% of telecom companies were victims of DNS-based malware and 81% needed 3+ days to apply a critical security patch.
DDoS Attacks
Telecom companies have also faced a number of distributed denial-of-service (DDoS) attacks against the internet providers that caused outages across Twitter, Netflix, Paypal and other services. It also disabled some subscribers’ routers permanently, which meant they had to replace them physically. DDoS (distributed denial of service) attacks remain a serious threat to telecoms providers around the world as attackers discover ever more ways of boosting the power and scale of attacks.
Telcos are the prime target for DDoS attacks. As much as 65% of the global DDoS attacks in 2018 were aimed at communication services providers and the figure still remains high in 2020. Kaspersky Lab’s DDoS intelligence report for Q2, 2016 notes that websites in 70 countries were targeted with attacks. By far the most affected country was China, with South Korea and the US also among the leaders. 70.2% of all detected attacks were launched from Linux botnets, with cybercriminals paying close attention to financial institutions working with cryptocurrency. Another trend observed in Q2 was the use of vulnerable IoT devices in botnets to launch DDoS attacks.
Direct attacks can reduce network capacity, degrade performance, increase traffic exchange costs, disrupt service availability and even bring down Internet access if ISPs are affected. With a growing number of connected devices and systems supporting mission-critical applications in areas such as healthcare and transport, unexpected downtime could be life threatening. Further, DDoS attacks can be a cover for a deeper, more damaging secondary attack, or a route into a key enterprise subscriber or large-scale ransomware attack.
Another recent report reveals that the following DNS attacks are on the rise too:
Multivector attacks – targeting several protocols at once – increased by 65% in the fourth quarter of last year.
DNS amplification is the most popular current cyber threat for DDoS attackers. In 2019, it has been present in one-third of all attacks.
The average bandwidth attack increased to 5 Gbps in 2019 – up from 2 Gbps in 2016.
Corrupt cloud servers are under fire too. The volume of DDoS attacks involving these increased to 51%.
Advanced APT
Advanced, international APT groups and nation-state attackers, have a powerful interest in obtaining access to the inner networks of telecommunication companies. This is because compromised network devices are harder to detect by security systems and they offer more ways to control internal operations than can be achieved through simple server/workstation infiltration.
The Regin APT campaign, discovered in 2014, remains one of the most sophisticated ever seen and has the ability to infiltrate GSM networks, while the Turla group, has developed the ability to hijack satellite-based Internet links as part of it’s Command & Control process, successfully obscuring its actual location. In many cases, attackers are exploiting new or under-protected vulnerabilities.
A Chinese advanced persistent threat (APT) actor is targeting major telecommunications companies in the US, Europe, and Southeast Asia in a cyber-espionage campaign that appears designed to steal data pertaining to 5G technology.
The campaign — dubbed Operation Diànxùn — is likely motivated by the ban on the use of Chinese technology in 5G rollouts in several countries, McAfee says in a new report of march 2021. According to the security vendor, the threat actor behind the campaign is using methods associated with Mustang Panda, a group that several security vendors previously have identified as working for the Chinese government.
Data related to Operation Diànxùn shows that victims were lured to a website purporting to be a career page for Huawei — widely regarded as the leader in the 5G space. Several governments, including the US, have barred the use of Huawei’s 5G technology out of fears that it might contain backdoors that enable widespread spying. There’s nothing to indicate that Huawei is in any way connected to the current threat campaign, however, McAfee says.
According to the security vendor, it’s unclear how the attackers initially lured victims to the phishing site. But once victims got there, they were greeted with a webpage that looked very similar to Huawei’s career site. The attackers used the fake website to download malware that masqueraded as a Flash application. The site from which the Flash application was downloaded also was carefully designed to appear like the official webpage in China for the Flash download site. The malware, among other things, downloaded the Cobalt Strike attack kit on compromised systems.
Thomas Roccia, senior security researcher with McAfee’s Advanced Threat Research group, says that available telemetry suggests that Mustang Panda is the group behind the ongoing Operation Diànxùn threat campaign. “The targets are mainly in the telecommunications sector,” he says. “Most of the organizations where we have observed telemetry hits, were expressing concerns regarding the rollout of 5G technology from China,” suggesting the campaign is tied to the global race to deploy next-gen communications technology, he says.
Network hardware
Another common targets of cyber-attacks include the Internet routers – both routers used in the backbone of the Internet and end user (consumer) routers . Backbone routers process the data of multiple organisations simultaneously; in targeting these routers the hackers hope to compromise many organisations at once.
SYNful knock is a modified device firmware image with backdoor access that can replace the original operating system if the attacker has managed to obtain privileged access to the device or can physically connect to it.
Configuration
In many cases, the hardware used by the telecommunications industry carries configuration interfaces that can be accessed openly via HTTP, SSH, FTP or telnet. This means that if the firewall is not configured correctly, the hardware in question becomes an easy target for unauthorized access. The risk presented by publicly exposed GTP/GRX (GPRS Tunneling Protocol/GPRS Roaming Exchange) ports on devices provides a good example of this.
Customer’s personal data stolen as Optus suffers massive cyber-attack
The telco suffered the data breach when hackers, believed to be working for a criminal or state-sponsored organisation, accessed the sensitive information by breaking through the company’s firewall.
Optus has 9.7 million subscribers, according to publicly available data, but the company said it was still assessing the size of the data breach. The company confirmed information which may have been exposed included Optus customers’ names, dates of birth, phone numbers, email addresses and, for a cohort of customers, physical addresses and identification document numbers such as driving licence or passport numbers. Optus said payment details and account passwords have not been compromised, and that services, including mobile phones and home internet, were not affected.
Home affairs minister Clare O’Neil said the Australian Cyber Security Centre was providing cyber security advice and technical assistance to Optus, and that Australian companies and organisations were being consistently targeted for cyber-attacks by cybercriminals and hostile nations.
“The Australian Signals Directorate’s (ASD) Australian Cyber Security Centre (ACSC) has seen broad targeting of Australians and Australian organisations, through rapid exploitation of technical vulnerabilities by state actors and cybercriminals seeking to exploit weaknesses and steal sensitive data.”
International signaling standards
Telecoms companies face particular cyber security concerns as a result of their interconnected nature and the reliance upon international standards in their operations. For example, mobile telecommunications providers rely upon the Signalling System 7 (SS7) protocol, the standard by which telecoms companies interoperate globally to facilitate roaming and delivery of calls and texts. SS7 protocol, in particular, has become one of the central cyber threats to the banking industry since hackers can easily intercept 2FA authentication codes and drain users’ accounts.
Many of these attacks present a unique challenge as protocols such as SS7 and BGP are defined by international standards and so require international cooperation to resolve the vulnerabilities. SS7 dates back to the 1970s and has been found to contain vulnerabilities that allow calls, texts and location information on handsets to be spied upon knowing only a subscriber’s phone number. It also allows calls, texts and other content to be diverted away from a legitimate subscriber’s handset to that of an attacker. For example, these vulnerabilities have recently been exploited in Germany by hackers to drain bank accounts by intercepting two factor-authentication SMS messages.
Known issues with the BGP (Border Gateway Protocol), which is used by those routers to control routing of traffic on the internet, have been exploited to redirect traffic to bad actors. Acceptance and propagation of routing information coming from other peers can allow an attacker to implement man-in-the-middle (MITM) attacks or cause denial of service. Kaspersky recommends that companies provide network filtering, allowing only a limited number of authorized peers to connect to BGP services.
Newer protocols such as SIP (Session Initiation Protocol) can also be extremely vulnerable to cyber threats without proper controls in place. For instance, in 2018 a group of attackers managed to stage a denial of service (DoS) attack on Cisco equipment through leveraging malformed SIP traffic.
However, implementing better signaling controls is proving to be a challenge for most telecoms due to the following: Overall complexity, Privacy concerns, Global title leasing, Supply chain issues, Network misconfigurations, and Traffic integrity.
SIP Hacking
Session Initiation Protocol (SIP), used in most voice-over-IP (VoIP) communications, is another prime target for malicious parties. Without proper security measures, hackers can easily tap into encrypter calls, distribute SIP malware and otherwise tamper with the VoIP services you are provisioning.
Here’s a list of cybersecurity threats that were common in 2019:
- SIP trunk hacking
- SIP toll fraud
- Eavesdropping
- Caller ID spoofing
- DDoS attacks on PBX systems
Utility suppliers in the US faced a series of VoIP attacks last year. An attacker was initially targeting 1,500 unique gateways tied to some 600 businesses, but later focused on a single company and, using a command-injection technique over HTTP, injected a malicious web shell into the company’s server outgoing directory.
Insider attacks
Sometimes insiders to the companies in the telecom industry are also lured or blackmailed into perpetrating cybercrime. Insiders from cellular service providers are recruited mainly to provide access to data, while staff working for Internet service providers are chosen to support network mapping and man-in-the-middle attacks.
Compromising subscribers with social engineering, phishing or malware.
Telecom companies have made huge leaps in security to protect their networks and their customers, but their own employees and executives remain extremely vulnerable to having their own accounts compromised, according to research from cybersecurity firm SpyCloud. In fact, the 11 telecom companies in the Fortune 1000 comprise the most vulnerable industry in the study – at greater risk than retail, banking, healthcare and other industries.
SpyCloud examined more than 100 billion account assets from previous data breaches and connected them to Fortune 1000 companies to see how exposed they are to account takeover (ATO) attacks, where hackers use someone’s login credentials to gain access to their accounts, potentially unlocking corporate data, sensitive personal information, finances and more. SpyCloud found 74% of employees, including C-level executives, working for Fortune 1000 telecom companies are reusing passwords across multiple work and personal accounts. Some of those sites will eventually be breached if they haven’t already.
Besides passwords, another common asset criminals use to takeover accounts is mobile phone numbers. With a simple phone call to a mobile carrier and some light social engineering, criminals can divert a victim’s phone service to their own device. Once the attacker has control of the victim’s phone number, they will receive the texts for multi-factor authentication, now commonly used as a more secure way to log into sensitive accounts.
Obtaining subscribers’ credentials has become attractive for hackers as consumers and businesses undertake ever more activity online and particularly on mobile. Further, Lower security levels on mobile devices make attacks even more attractive to criminals. Some of the these include malware for mobile devices, subscriber data harvesting, end-user device vulnerabilities, and more.
The number of mobile malware infections is on the rise, as is the sophistication and functionality of the malware. Social engineering and phishing remain popular activities and they continues to evolve and improve, targeting unaware or poorly aware subscribers and telecoms employees. Recent research shows that the cryptography of 3G/4G USIM cards is no longer unbreakable. Successful attacks allow SIM card cloning, call spoofing and the interception of SMS.
USBs, modems and portable Wi-Fi routers may contain multiple vulnerabilities in their firmware and user interfaces. These include: Vulnerabilities in web interfaces designed to help consumers configure their devices. Vulnerabilities that result from insufficient authentication. RCE (Remote Code Execution) vulnerabilities based on different variants of embedded Linux that can enable firmware modification and even a complete remote compromise.
IoT Network Security threats
By 2021, Gartner estimates that some 25 billion IoT devices will be connected to telecom networks. Accommodating such an increased volume of data is just one part of the challenge though. Preventing unauthorized access, securing data transmissions and ensuring smooth monitoring of a much larger attack surface are the key security challenges for telcos.
Despite low adoption, IoT devices have already proven to present both internal and external threats to cybersecurity. First of all, the device itself can be exposed to various cyber threats and vulnerabilities due to manufacturing issues. Secondly, misconfiguration and lack of proper security measures make an IoT device an easy entry-point to the entire network of devices, or worse – the supporting architecture. In short, most attackers will have an easier way of finding a leeway as the surface of attack increases.
Some of the common types of cybersecurity threats happening at network level are as follows: Network congestion, RFIDs interference and spoofing, Node jamming in WSN, Eavesdropping attacks, Sybil attacks, DDoS attacks, and Routing attacks.
Offering solid protection against these is a joint responsibility between network operators and IoT users.
Cyber Security
Telecom companies need to ensure that proactive defence and cyber incident response plans that address the risks to such incidents. It is important to have the right people on board, otherwise the cyber-crime rate will keep increasing. Thus, it is critical to address the ever-evolving and growing sophisticated cyber crime incidents with the right cyber security measures in place.
As a risk based approach, telecommunication companies protect their systems by assessing threats and also by developing and implementing appropriate risk-management practices. A comprehensive, multi-layered security solution is a key component of this, but it is not enough on its own. It needs to be complemented by collaboration, employee education and shared intelligence. Mobile network operators today defend their networks using Gi firewalls and DDoS protection appliances. Further, telecom companies should religiously embrace cloud-enabled cyber security services, conduct real-time monitoring and extensively use threat intelligence tools.
To protect the organization from misconfiguration and network device vulnerability, Kaspersky Lab recommends that companies pay close attention to vulnerabilities in the network services of telecommunication equipment, establish effective vulnerability and configuration management processes, and regularly perform security assessments, including penetration testing for different types of attackers (a remote intruder, a subscriber, a contractor, etc.).
Granted, according to a report by the European Union for Cybersecurity, most telecoms have implemented the basic security measures for SS7 attacks:
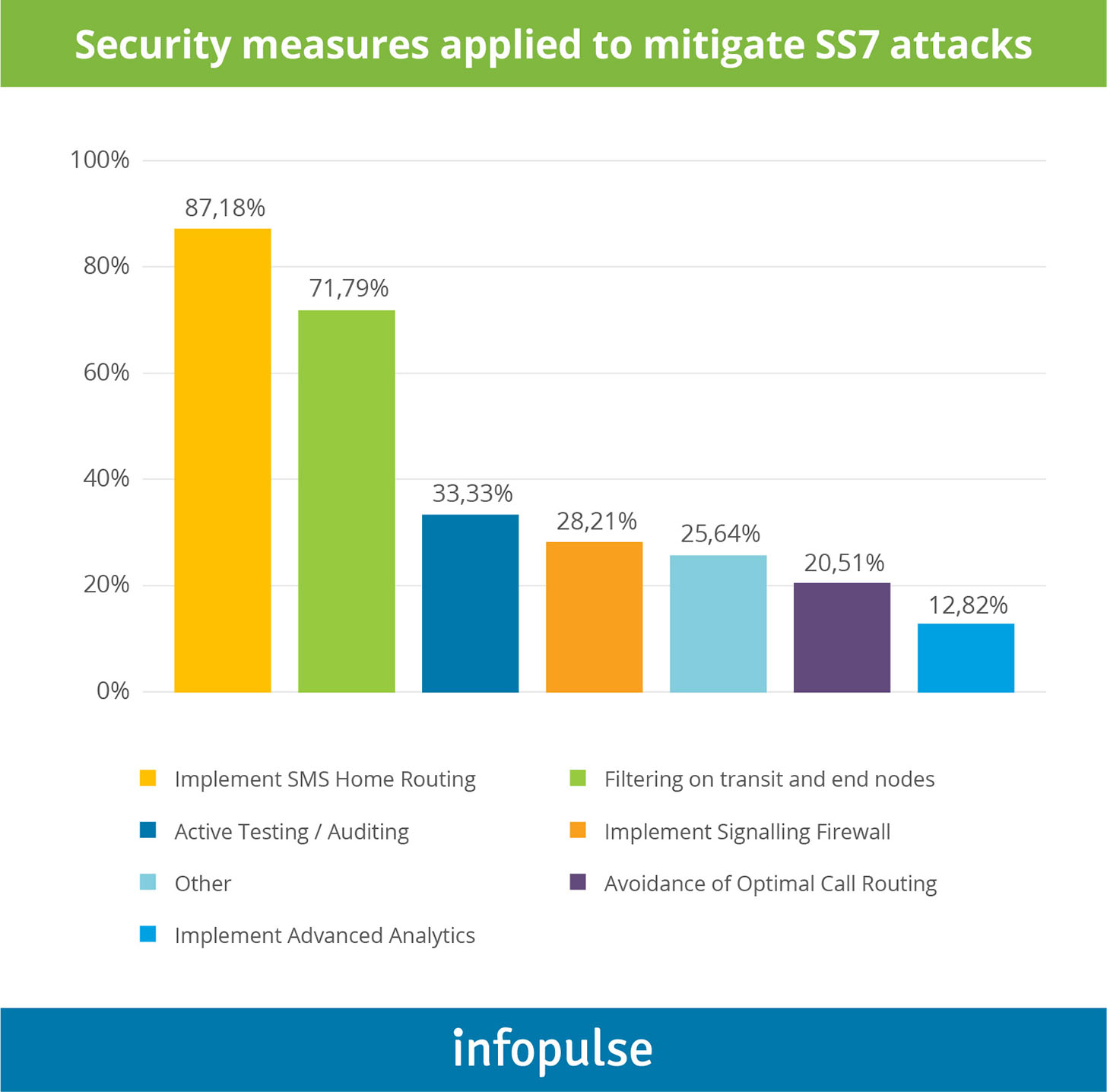
Cybersecurity Best Practices
To deal with common telco cyber-attacks such as SS7 threats, DDoS and DNS, telecom companies can employ anomaly detection tools to monitor traffic across a given telecom network. Such tools carry out continuous behavioural monitoring of digitised networks and detect security errors and unusual network activity using machine learning-powered pattern recognition. Telecom networks are often vast in size and spread across several regions. To maintain high data security standards in such networks, telecom companies need to have third-party evaluators conduct security audits. The data security audit report created after an evaluation will enable telecom companies and governments to identify weaknesses in their networks and plug them promptly. Telecom users must be informed about cyber-hygiene measures that will protect their devices and data from malicious attacks.
-
- Exhaustive monitoring that covers all interconnect and outgoing traffic, as well as core network elements.
- Harden network nodes by implementing better firewall configuration rules.
- Conduct regular external network security assessments and penetration tests.
- Implement real-time anomaly detecion systems to identify more advanced attacks and their prequels.
Also, keep an eye on updates from the Fraud and Security Group (FASG) work group organized by GSMA that is working on new end-to-end interconnect security solutions for LTE and 5G networks.
Best Practices for Protecting SIP Signalling
- Enforce strong encryption over your Transport Layer Security (TLS) and Real-Time Protocol (RTP) to protect all data transmissions.
- Implement anti-spoofing for SIP messages. Ensure that you have proper in-built mechanisms for challenging messages and authenticating SIP clients.
- Maintain strong Session Border Controller (SBC) controls that perform deep packet inspection of all SIP messages and prevent unauthorized SIP traffic.
DNS Attack Prevention Best Practices
- Switch from a reactive to a proactive approach to cybersecurity. Start applying adaptive countermeasures.
- Implement real-time analytics for DNS transactions and gradually build up a behavioral threat detection suite, capable of detecting both known and emerging cyber threats and protect against data theft/leaks.
- Enhance your firewalls with ML-driven response policies on traffic to suspicious hostnames.
- Implement query monitoring and logging for all suspicious endpoints.
How Telcos Can Protect Against DDoS Attacks
- Set up robust Access control lists (ACL) – your first line of defense. Note, however, that ACL has a scaling issue. A rapid increase of temporary ACLs, built to resist a large-scale attack, can have a major performance impact on different router hardware and software, making the overall management rather challenging. Thus, it’s best to write several scripts for automatic router configuration and ACL management.
- Implement black hole scrubbing – a variation of the block hole filtering technique. In this case, the traffic is redirected to a different physical interface – a scrubbing center – that can weed out the good traffic from the malicious one. A number of software vendors offer such solutions.
- Real-time DDoS monitoring is a must. The best-of-breed tools are now powered with machine learning functionality, meaning their detection accuracy progressively increases over time.
Social engineering, phishing or malware.
- Use Multi-Factor Authentication everywhere
- Use a password manager for all of your logins (not just for work)
- 3. Stop rotating passwords every 90 days: This provides a false sense of security and frustrates people, so they may end up recycling passwords (simply adding a character at the end of a well-worn password, thinking that is safe). Instead, educate users on password hygiene and provide guidelines for creating strong passwords.
- Don’t click on links or open attachments from unknown senders: Phishing attempts containing credential-stealing malware have grown much more sophisticated and difficult to detect. Remain vigilant and keep employees apprised of the latest fraud attempts on the rise.
- Monitor your credentials and PII – both work and personal: There are free services available that will continuously check whether your credentials show up on breached lists, so you can secure your accounts quickly. There are also systems available for ongoing monitoring of exposed passwords for all your employees, allowing you to take swift action to prevent criminals from monetizing those credentials at the cost of your business and customers.
IoT Cybersecurity Best Practices
GSMA has already developed a comprehensive IoT security assessment checklist for telcos, along with several supporting documents with security guidelines. Below are some of the key best practices the association proposes against common cybersecurity threats:
- Network operators should use UICC based mechanisms for the secure identification of IoT devices. You can also provide single sign-on services for devices but mind the security trade-offs.
- Enable secure authentication for all devices, networks and service platforms associated with an IoT Service.
- Offer data encryption services to IoT service providers to ensure high communication integrity and increase network resilience.
- Deploy private networks to support various IoT networks. These can be developed using Layer Two Tunnelling Protocol (L2TP) and secured with Internet Protocol Security (IPsec) as illustrated below:
New Regulations
In 2018 the Network and Information Security Directive (NISD) as well as the General Data Protection Regulation (GDPR) will be implemented in the EU. The NISD, which is due to be implemented by May, will require operators of core “digital infrastructure” and certain “digital service providers” to ensure that their network and information systems meet minimum standards of cyber security.
The National Cyber Security Centre in the UK (which is part of GCHQ) has issued guidance2 for digital infrastructure providers that is expected to be enforced by Ofcom (the nominated sectoral regulator). NCSC has adopted a principles-based approach to cyber risk. The guidance requires a focus on four high level objectives, including managing risk, protecting against cyber-attacks, detecting attacks and minimising the impact of incidents. It sets 14 lower level principles to allow operators achieve these objectives. Much emphasis is placed on managing supply chain risk.
While much of the guidance is drawn from pre-existing industry best practice and existing NCSC advice, digital infrastructure providers will need to ensure and demonstrate that their cyber security practices are compliant by May 2018 or face substantial fines.
References and Resources also include:
https://www.expresscomputer.in/news/telecom-industry-needs-to-be-paranoid-about-security/20406/
https://www.infopulse.com/blog/security-telecom-threats-and-solutions/
 International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis