Industrial control system (ICS) is a collective term used to describe different types of control systems and associated instrumentation, which include the devices, systems, networks, and controls used to operate and/or automate industrial processes. Depending on the industry, each ICS functions differently and are built to electronically manage tasks efficiently. …
Read More »Mobile security
The future of computers and communication lies with mobile devices, such as laptops, tablets and smartphones with desktop-computer capabilities. Their size, operating systems, applications and processing power make them ideal to use from any place with an internet connection. And with the expansion of ruggedized devices, the Internet of Things …
Read More »Cyberbiosecurity threats, vulnerabilites and cyberbiosecurity technologies
The life sciences now interface broadly with information technology (IT) through its industrial applications in health care, agriculture, manufacturing, automation, artificial intelligence, and synthetic biology. The information moves between living and cyber systems in a two-way flow. Global public health crises create conditions of extreme fragility where dual-use technologies …
Read More »Cyber attacks on Power Grids and Nuclear plants will have devastate economy affecting millions of people and military operations
Energy sector has become one of the attractive targets for cyber attackers. Hackers already target the energy sector more than any other part of U.S. critical infrastructure, according to the most recent government report. There are more reported cyber incidents in the energy industry than in healthcare, finance, transportation, water …
Read More »Growing Cyber threats to commercial aviation require cyber risk management, and resilient systems
Cyber attacks are growing in number and sophistication affecting large corporations, critical infrastructures of all kinds, governments to SMEs, and increasingly the aviation industry. Commercial aviation plays a central role in our daily lives and is an essential part of the national economy. The number of passengers rose from …
Read More »Cyberwarfare among US, China and Russia driving Secure Internets cyber technologies
Cyber warfare has developed into a more sophisticated type of combat between countries, where you can destroy critical infrastructure such as power, telecommunications or banking by damaging the computer systems that control those infrastructures. It’s widely acknowledged that offensive cyberattacks will be a necessary component of any future military campaign, …
Read More »Optical Networks Vulnerabilities and Security threats
Optical networks are vulnerable to several types of security breaches or attacks, typically aimed at disrupting the service or gaining unauthorized access to carried data, i.e., eavesdropping. Depending on the aim of the attack, security breaches can induce financial losses to the clients or cause network-wide service disruption, possibly leading to huge …
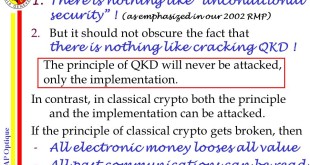
Read More »Quantum cryptography (QC) or Quantum key distribution (QKD) are assumed hackproof but its implementations have vulnerabilities
Quantum computers could undermine almost all of the encryption protocols that we use today. Though quantum computers are still quite some way from being practical, usable machines, once they become so, we could be looking at a whole new world when it comes to online privacy — one in which …
Read More »Growing Cyber threat on supply chains and Defense Industrial Base (DIB) require Supply Chain Risk Management (SCRM)
In its simplest form a supply chain is the activities required by the organisation to deliver goods or services to the consumer. A supply chain can take on the form of a product based supply chain or that of a service, where services come together to offer an overall customer …
Read More »Cyber Moonshot and Accelerating Security of Systems with Emerging Technologies (ASSET)
The nation’s critical infrastructure is increasingly dependent on the Internet, while cybersecurity attacks are on the rise. Cybersecurity threats are becoming more frequent, more sophisticated, and more destructive—gradually eroding society’s trust in digital infrastructure. As technology continues to advance and every facet of daily life becomes increasingly interconnected, both the …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis