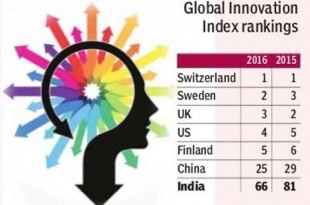
The Global Competitiveness Index is released by the World Economic Forum(WEF). It was launched in …
Read More »Masonry Layout
Researchers employ biomimetics for design of perfect Drones for delivery services, Search and rescue to counter drone missions
Unmanned aerial vehicle technology is advancing rapidly, and drones are getting smaller by the day. …
Read More »Militaries test Stand-off smart anti-airfield weapon (SAAW) to destroy enemy runways
Anti-runway penetration bombs are systems involving bombs or bomblets designed to disrupt the surface of …
Read More »Thermotronics aims to process information with Thermal networks and heat flows
The control of electric currents in solids is at the origin of modern electronics which …
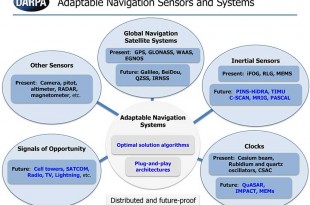
Read More »DARPA developing GPS backup and beyond Technologies for GPS denied and degraded environments
The GPS system provides critical positioning capabilities to military, civil, and commercial users around the …
Read More »DARPA’s WiSPER program developing next generation spread spectrum based military tactical radio to enable secure high-bandwidth RF communications
U.S. military researchers are asking industry to develop secure radio frequency (RF) transmitter and receiver …
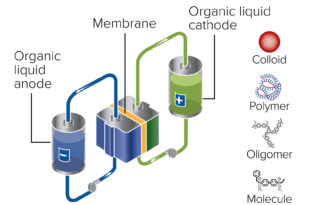
Read More »Green Battery Cells or Organic Batteries promises sustainable electrical energy storage future
The amount of electricity consumed worldwide grows by the year, and so does the demand …
Read More »India launches emerging technologies strategy
The Digital India programme, launched in July 2015, is a flagship programme of the Government …
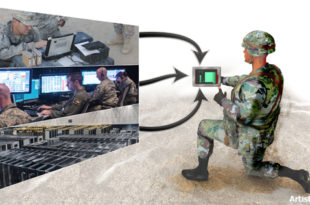
Read More »DARPA’s WARP developing wideband adaptive RF circuit technology to Protect Ultra-Wideband Military radios, radars and EW systems from Jamming
The military uses the electromagnetic spectrum — essential, yet invisible — to detect, deceive and …
Read More »DARPA Ditto developing artificial intelligence (AI) and machine learning based surrogate models to speed design of military systems
DoD is exploring opportunities to incorporate autonomy, AI, and human-machine teaming into its weapons and …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis