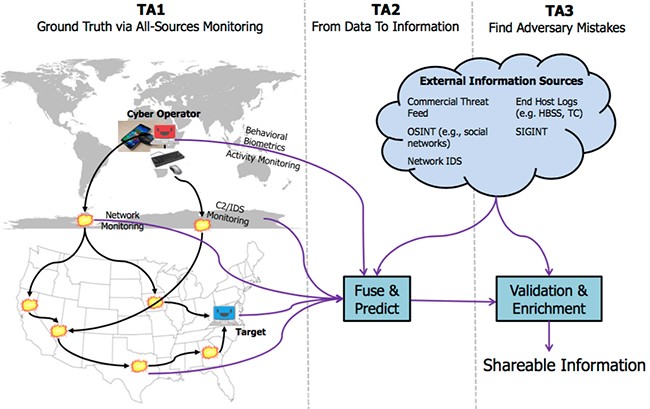
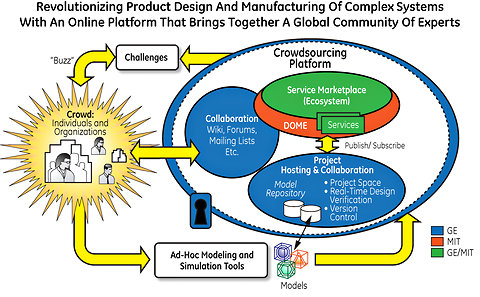
DARPA WASH built Smartphone App for continuous assessment of Warfighter readiness and predict Illness or Injury
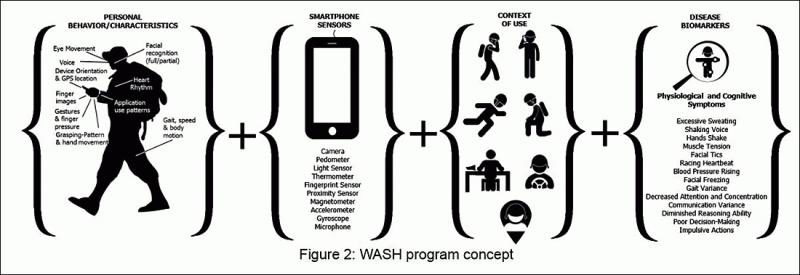
Around the world, armies are recognizing the importance of maximizing the effectiveness of Soldiers physically, perceptually, and cognitively. Militaries are therefore studying effects of frustration, mental workload, stress, fear and fatigue on both cognitive and physical performance. Early detection…...