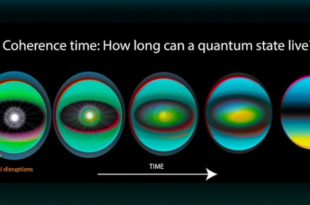
‘The development of a “quantum computer” is one of the outstanding technological challenges of the …
Read More »Masonry Layout
Rising importance of Non- Acoustic detection technologies of Stealthy submarines in Anti Submarine Warfare
Ship detection for offshore production operations, military activities, transportation and other marine applications is very …
Read More »DARPA A-Teams, CAML & ADAPT programs developing efficient Agile Human-Machine Teams to execute battlefield, cyber and electronic warfare missions
The prime aim of US third offset strategy, announced in November 2014, was to develop …
Read More »Indian Ocean maritime security threats and Indian Navy’s Maritime Domain Awareness (MDA) technology requirements and solutions
Indian Ocean has always been vulnerable to criminals and anti-national activities. The Indian Ocean is …
Read More »Countries developing Asteroid mining technologies
Early evidence suggests that there are trillions of dollars’ worth of minerals and metals buried …
Read More »DARPA CHARIOT developing Quantum proof cryptography for Military Mobile and IoT security
The exponential price/performance improvements in semiconductor technology stemming from Moore’s Law are enabling even the …
Read More »Solar fiber optic lighting for daylighting of high-rise intensive buildings and military shelters
Conventional daylighting scheme employing windows and skylights are no longer so useful especially for daylighting …
Read More »Miniaturized RF passive components like filters, inductors and capacitors required for future 5G and IoT requirements
The RF design consists of passive as well as active components. The inductors, capacitors, and …
Read More »Cyber Security Situational Awareness tools on Defense Platform Networks are critical for Cyber Warfare
Cyberspace is understood as the fifth domain of warfare equally critical to military operations as …
Read More »DARPA HACCS employing AI for cybersecurity by developing autonomous software agents, that will infiltrate adversary’s networks, detect botnets and neutralize them
As the complexity of software is growing software vulnerabilites are also increasing. According to two …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis