Artificial Intelligence (AI) is revolutionizing industries and transforming the way we work, communicate, and live. However, its immense potential is also being exploited by cybercriminals and nation-state adversaries. The combination of AI and cybersecurity poses one of the greatest modern challenges, where sophisticated algorithms are weaponized for malicious purposes. AI-powered …
Read More »The Technical Landscape of Deepfakes: Creation, Detection Challenges, and Cutting-Edge Solutions
The rapid evolution of artificial intelligence has brought with it remarkable advancements in media generation. One of the most controversial developments in this space is deepfake technology—AI-generated content that manipulates images, videos, and audio with near-perfect realism. Deepfakes have found applications in entertainment, media, and even assistive technologies, but their …
Read More »A New Era of Malware: Large Language Models (LLMs) Unleashed
The landscape of cyber threats is rapidly evolving, with the emergence of sophisticated malware leveraging cutting-edge technologies. One particularly alarming trend is the increasing use of Large Language Models (LLMs) to enhance the capabilities of malicious software. In recent years, the rapid evolution of artificial intelligence (AI), particularly Large Language …
Read More »A Vulnerable Lifeline: Protecting Water Infrastructure from Cyberattacks
In an era where the digital landscape is intricately woven into the fabric of daily life, critical infrastructure sectors such as drinking water and wastewater systems have become increasingly attractive targets for cyberattacks. Water infrastructure, encompassing drinking water and wastewater systems, serves as a critical lifeline for communities globally. Unfortunately, these …
Read More »DARPA SemaFor to tackle ‘deepfakes’ with semantic forensics and create automatic disinformation campaigns for US DOD
The rise of digital media has brought unparalleled opportunities for information sharing, but it has also created fertile ground for large-scale disinformation attacks. As the ability to generate falsified media—whether through altered images, deepfake videos, or fabricated text—has advanced rapidly, so too has the threat of automated disinformation at an …
Read More »DARPA Tackles Deepfakes: New Initiatives to Combat AI-Generated Media
The Defense Advanced Research Projects Agency (DARPA) has unveiled two major initiatives to strengthen defenses against deepfakes—AI-generated media designed to deceive by manipulating or synthesizing content. With the rapid advancement of artificial intelligence, deepfakes are becoming increasingly sophisticated and pose a significant threat to national security, public trust, and the …
Read More »DARPA CARCOSA Program: Enhancing Cyber Capabilities on the Battlefield
The Defense Advanced Research Projects Agency (DARPA) has long been at the forefront of groundbreaking technological innovations, particularly in the realm of national security. One of its latest and most ambitious initiatives, the CARCOSA program, seeks to revolutionize cyber warfare capabilities for U.S. warfighters. This program aims to provide cyber …
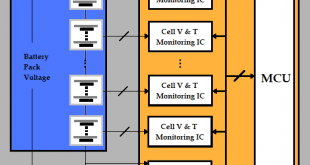
Read More »Powering the Future Soldier: Fault-Tolerant and Cyber-Secure Battery Management Systems (BMS) for Military Applications
In modern warfare, the reliance on advanced electronics and portable devices has made power management a critical factor in ensuring mission success. From communications equipment and surveillance tools to wearable technology and autonomous systems, the demand for reliable, long-lasting, and secure power sources has never been greater. At the heart …
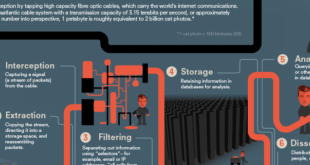
Read More »A Global Analysis of Advanced Mass Surveillance Practices and Technologies
In the wake of recent global threats and terrorism, governments around the world have ramped up their surveillance efforts, often crossing into areas previously deemed private. What once seemed the stuff of spy movies is now a stark reality, as intelligence agencies have developed incredibly sophisticated, invisible, and persistent surveillance …
Read More »Bolstering National Security: Addressing Vulnerabilities in the U.S. Defense Industrial Base
As global tensions rise, the U.S. Defense Industrial Base (DIB) finds itself grappling with a range of escalating supply chain risks, particularly those emanating from China. These risks are not confined to the availability of raw materials and components but extend into the digital realm, where cyber threats pose an …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis