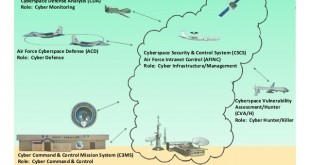
The Department of Defense (DOD) defines cyberspace as a global domain within the information environment consisting of the interdependent network of information technology infrastructures and resident data, including the internet, telecommunications networks, computer systems, and embedded processors and controllers. The DOD Information Network (DODIN) is a global infrastructure carrying DOD, …
Read More »With rising threat of mobile malware, Mobile companies are launching secure smartphones
The recent rise in mobile malware have made Mobile phones vulnerable to data leakage and tempering of sensitive information such as business documents, bank details, credit card information and make purchases. Malware client called Pegasus have been found that can jailbreak your smartphone, ultimately installing a client that can seize data, …
Read More »Rising cyber-attacks to Small and Medium Businesses( SMB or SME) and cyber security requirements
SMEs contribute to more than one third of GDP in emerging and developing economies and account for 34% and 52% of formal employment respectively. SMEs and young firms that experience rapid growth can have a considerable impact on employment creation and productivity growth, including through innovation, heavy investments in human …
Read More »DARPA plans secure Blockchain technologies to create tamper-proof military computer systems
Blockchain is a transformative technology for the two billion people in the world currently underserved by financial institutions. The technology has the potential to enhance privacy, security and freedom of conveyance of data. Blockchain is based on open, global infrastructure, decentralized public ledger of transactions that no one person or …
Read More »IARPA using Big Data Analytics to automatically discover Signals from Web Sources to Predict Cyber Attacks
Cyber crimes and attacks continue to expand exponentially and involving more and more advanced and sophisticated techniques to infiltrate corporate networks and enterprise systems. Types of attacks include advanced malware, zero day attacks and advanced persistent threats. Flawed software, the root of most program errors and security vulnerabilities, is a critical …
Read More »DARPA’s PLINY & MUSE use Big Data on open-source software to remove software vulnerabilities and enhance reliability
During the past decade information technologies have driven the productivity gains essential to U.S. economic competitiveness, and computing systems now control significant elements of critical national infrastructure. As a result, tremendous resources are devoted to ensuring that programs are correct, especially at scale. Unfortunately, in spite of developers’ best efforts, …
Read More »DARPA enhancing Military COTS system security by automatically deploying secure configurations of Components
The growth of the internet-of-things (IoT) and network-connected composed systems (e.g., aircraft, critical-infrastructure, etc.) has led to unprecedented technical diversity in deployed systems. From consumer IoT devices developed with minimal built-in security, which are often co-opted by malware to launch large distributed denial of service (DDoS) attacks on internet infrastructure, …
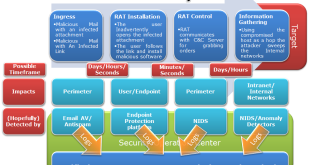
Read More »Detecting and Mitigating Advanced persistent threat (APT) major challenge for IT Firms, industrial establishments, and military organizations.
An advanced persistent threat (APT) refer to complex, sophisticated and stealthy techniques of using software, hardware or social engineering tools to continuously monitor and extract data from targets such as organizations and/or nations for business or political motives. They typically start with seemingly benign activities that do not trigger any …
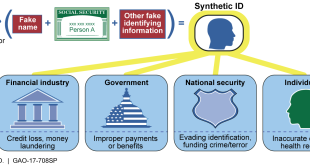
Read More »Synthetic Identity Fraud is one the fastest-growing forms of identity theft used by fraudsters and terrorists
Synthetic identity theft is a type of fraud in which a criminal combines real and fake information to create a new identity, which is used to open fraudulent accounts and make fraudulent purchases. Fraudsters use this fictitious identity for obtaining credit, opening deposit accounts and obtaining driver’s licenses and passports. …
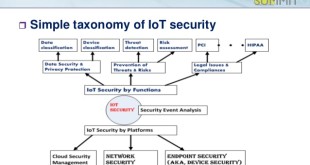
Read More »New technologies to secure future Billions of Every day and Military “Internet of Things” and enabling new industrial revolutions such as Industry 4.0
By 2025, it is predicted that there can be as many as 100 billion connected IoT devices or network of everyday objects as well as sensors that will be infused with intelligence and computing capability. These devices shall comprise of personal devices such as smart watches, digital glasses and fitness …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis