NATO ministers have designated cyber as an official operational domain of warfare, along with air, sea, and land. Cyber warfare has developed into a more sophisticated type of combat between countries, where you can destroy communications infrastructure, said Marc Rogers, Head of Security for DefCon, adding that ordinary people become …
Read More »Scientists develop FontCode, that hides information by imperceptibly changing the shapes of fonts in text.
Wikipedia defines Steganography is the practice of concealing a file, message, image, or video within another file, message, image, or video. The word steganography combines the Greek words steganos (στεγανός), meaning “covered, concealed, or protected,” and graphein (γράφειν) meaning “writing”. For example, the hidden message may be in invisible ink …
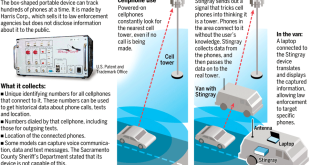
Read More »Police use stingray, a secretive phone surveillance technology to solve crimes or foil a terror attack
Smartphones carried by most people depend on cell site or cell tower for their operation. A cell site or cell tower is a cellular telephone site where antennae and electronic communications equipment are placed — typically on a radio mast, tower, or other raised structure — to create a cell …
Read More »Military developing sound endpoint management strategies to deal with rising cyber-attacks and data breaches, and increasingly mobile workforce
With the rise of cyber-attacks and data breaches, and today’s increasingly mobile workforce, securely managing data and endpoints without inhibiting employee productivity has become critical to organizations including military. Many devices including smart phones, tablets and laptops now have network access capabilities however these devices also provide an entry point …
Read More »What would be Cyber future? AI, Persistent surveillance, War of data, Internet of Emotions, and human hacking
Cyber attacks are continuously increasing in numbers, becoming more varied more sophisticated, and more impactful. What Will Cybersecurity Look Like 10 Years From Now? According to Gil Shwed, Founder and CEO of Check Point Software Technologies Ltd., the future of cybersecurity is tightly connected to the future of information technology and …
Read More »DARPA’s LADS program to secure Military Internet of things (MIOT) from cyber and other attacks from adversaries, hackers, and terrorists.
The Internet of things (IoT) is the network of physical devices, vehicles, home appliances and other items embedded with electronics, software, sensors, actuators, and connectivity which enables these objects to connect and exchange data. Each thing is uniquely identifiable through its embedded computing system but is able to inter-operate within the …
Read More »The shortages of cyber warriors are driving Militaries to recruit geek armies to complement their cyber force.
The incidents of cyberwarfare are ever increasing, targeting more and more countries and becoming legitimate. Part of the Ukrainian power grid was attacked by hackers, causing blackouts; US accused Iranians of attempting to hack into the control-system of a dam. Russia was also suspected for cyber-attack on Turkey following the …
Read More »Under High-profile global cyber attacks, Global Cybersecurity Index 2017 measures the commitment of the ITU Member States to cybersecurity
Singapore has topped a global cyber security index released by the United Nations, followed by other UN member states such as the United States, Malaysia, Oman, Estonia, Mauritius, Australia, Georgia, France and Canada, the other top 10 countries. The Index has been released by the UN telecommunications agency International Telecommunication …
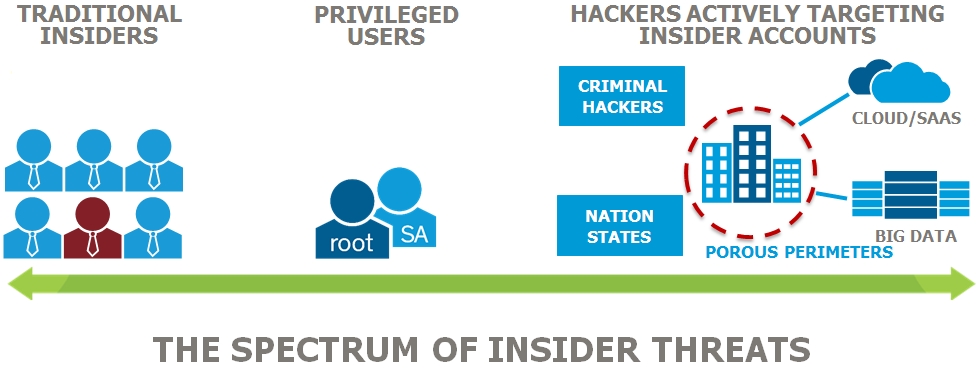
Read More »Real-time behavioral analytics, new tool for detecting advanced external and internal Cyber threats and mental health, employed by Intelligence agencies to DOD
An insider threat is a malicious threat to an organization that comes from people within the organization, such as employees, former employees, contractors or business associates, who have inside information concerning the organization’s security practices, data and computer systems. The threat may involve fraud, the theft of confidential or commercially …
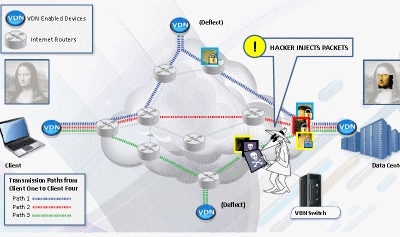
Read More »New cyber security technologies Dispersing data packets over Multiple Network Paths and Continuously Scrambling Code
“United States adversaries are launching increasingly sophisticated cyberattacks on the complicated web of networked systems upon which our military relies,” explained Robert W. Twitchell, Jr., President and CEO of Dispersive Technologies. “These attacks impair connectivity, degrade mission effectiveness and threaten lives. “While the means of cyber attacks vary, the pattern …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis