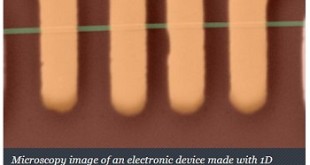
Nanomaterials are often categorized based on number of dimensions of a material, which are outside the nanoscale (<100 nm) range. Accordingly, in one-dimensional nanomaterials (1D), one dimension is outside the nanoscale. This class includes nanofibers, nanotubes, nanorods, and nanowires. 1D materials are generally considered to be high‐capacity and stable electrode materials, due …
Read More »Yearly Archives: 2018
Researchers developing Vanishing or self destructing electronics to avoid being leaked or reverse engineered
In April 2001, a US Navy surveillance plane was intercepted by two Chinese F-8 fighter planes during a routine patrol flight over the Chinese South Sea. The US plane was forced to make an emergency landing in China, after what officials described as a “minor” midair collision, occurred with one of the Chinese planes. The US …
Read More »DARPA’s SD2 developing tools to design complex systems like synthetic biology, neuro-computation and polymer chemistry
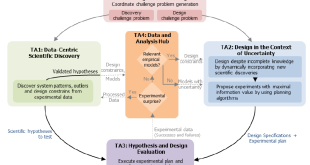
Engineers regularly use high-fidelity simulations to create robust designs in complex domains such as aeronautics, automobiles, and integrated circuits. In contrast, robust design remains elusive in domains such as synthetic biology, neuro-computation, and polymer chemistry due to the lack of high-fidelity models. DARPA’s Synergistic Discovery and Design (SD2) program aims …
Read More »DARPA’s Transparent Computing programme for defeating complex, sophisticated and stealthy long-term Advanced Persistent Threats ( APTs)
Modern computing systems are essentially black boxes that accept inputs and generate outputs, but provide little-to-no visibility of their inner workings, according to DARPA. It can therefore be extremely challenging to detect an intruder, particularly an ‘Advanced Persistent Threat’: a form of attack in which the adversary slowly and deliberately …
Read More »Artificial Intelligence Race among tech gaints like Google and Baidu from facial recognition into AR and autonomous driving
As the world itself becomes more complex, AI will become the defining technology of the twenty-first century, just as the microprocessor was in the twentieth century, wrote Albert Einstein. In an article for the World Economic Forum, Marc Benioff, chairman and CEO of Salesforce, explains that the convergence of big data, machine …
Read More »Researchers employing Simulation and Integrated Computational Materials Engineering (ICME) to accelerate the development of new materials
Finding new materials has traditionally been guided by intuition and trial and error,” said Turab Lookman, a physicist and materials scientist in the Physics of Condensed Matter and Complex Systems group at Los Alamos National Laboratory. “But with increasing chemical complexity, the combination possibilities become too large for trial-and-error approaches …
Read More »DARPA developing milimmter wave wireless communications to connect dismounted warfighters using UAVs and provide 100 Gb/s RF Backbone (100G)using High-altitude, long-endurance platforms.
Modern expeditionary military missions generate and exchange massive amounts of data that are used to produce situational awareness and guide decision-making. Much of the data must travel long distances along backbone communications networks composed of high-capacity links that connect command centers. Fiber optic cables provide the core backbone for …
Read More »NATO Conducts Locked Shields 2018: World’s Largest International Live-fire Cyber Defense Exercise to train security experts in Cyberwarfare
The urgency behind NATO’s deepening interest in cyber defense is driven by the increasing sophistication of cyberthreats against member states, according to Brig. Gen. Christos Athanasiadis, assistant chief of staff cyber at SHAPE. NATO reported earlier this year that its infrastructure came under threat from 500 cyberattacks monthly in 2016.The …
Read More »RAND envision the world in 2040, analyze security challenges that will shape it and offer guidance to policymakers
In coming decades, emerging technologies such as artificial intelligence and 3D printing will pose new risks to people, nations, and global security. At the same time, accelerating change will challenge policymakers’ capacity to adapt. Some of the questions that Michael Rich and his team are exploring in RAND under a …
Read More »Airborne or Spaceborne Synthetic aperture ladar (SAL) for centimeter-class resolution battlefield awareness
Conventional optical imagers are limited in spatial resolution by the diffraction limit of the telescope aperture, as well as by the practical difficulties in increasing the telescope aperture. Synthetic aperture (SA) techniques can increase resolution beyond the diffraction limit of the receiving aperture. Just as synthetic aperture radar(SAR) working …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis