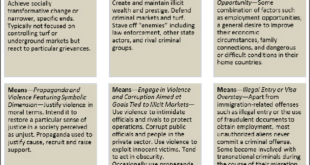
In an increasingly globalised and interconnected world it has become simple for people and goods to cross borders and so for terrorists. America’s borders and ports are busy places, with tens of millions of cargo containers and hundreds of millions of lawful travelers entering the country each year, while tens …
Read More »TimeLine Layout
July, 2021
-
10 July
Biocomposites leading material transformations in Automobile, Aeronautics, Space and Military applications
With the growing global concerns over climate change, scientists are looking for cleaner energy sources and other ways to minimize the carbon footprint in the world. A carbon footprint is the total amount of greenhouse gas emissions that come from the production, use and end-of-life of a product or service. …
Read More » -
10 July
DARPA’s Squad X revolutionising infantry squads by integrating Unmanned air and ground vehicles, new technologies for Precision engagement, Electronic Warfare, Situational Awareness and Autonomy
Modern military engagements increasingly take place in complex and uncertain battlefield conditions where attacks can come from multiple directions at once, and in the electromagnetic spectrum and cyber domains as well. U.S. Army and U.S. Marine Corps dismounted infantry squads, however, have been unable to take full advantage of some …
Read More » -
10 July
Race for faster, high performance System on Chip (SoC) for 5G, mobile computing, Smartphones, and IoT
A system on a chip or system on chip (SoC) is an integrated circuit (also known as a “chip”) that integrates all components of a computer or other electronic system on a single circuit die. Similar to how a microcontroller integrates a microprocessor with peripheral circuits and memory, an SoC …
Read More » -
8 July
Night Vision Devices integrated with cellphones and Google Glass like wearables will provide future Soldiers greater situational awareness
Night vision devices are becoming essential equipment for night driving, night flying and night surveillance, wildlife observation and search and rescue missions. According to Industry ARC’s report on Night vision devices, the market is estimated to grow to $20.5 billion in 2020 at a CAGR of 7%. Since the …
Read More » -
7 July
Threat of Radiological warfare, Radiological weapons and Dirty Bombs
The threats of chemical, biological, radiological, nuclear and explosive (CBRNE) hazards continue to advance. CBRN weapons are some of the most indiscriminate and deadly weapons in existence today, with capability to affect large population in wide geographical area and in short time. The release of Chemical, Biological, Radiological and Nuclear …
Read More » -
6 July
Militaries deploying unmanned tanks to strike drones, cruise missiles and ground targets and carry electronic warfare mission
Tank has been a mainstay of modern militaries, providing a unique capability of high lethality, protection and mobility. It’s heavy gun, can fire high explosive shells to destroy adversary’s tanks , it is heavily armored itself protecting crew from enemy fire and and it can move off roads since it …
Read More » -
5 July
Lab-on-Chip devices allow faster and cheaper DNA sequencing and biochemical detection to chemical synthesis
Lab-on-chip is an integrated miniaturized device that allows researchers to perform all the operations from sample collection to final analysis onto the same chip. Theoretically, LOC technology has the potential to carry out almost any laboratory procedure on a miniaturized scale. This could range from DNA sequencing and biochemical detection …
Read More » -
3 July
Tungsten, the wonder military material used in armor-piercers, armored tanks, to Hypervelocity projectiles is controlled by China
Tungsten is one of the hardest metals on the earth, and many scientists compare it to diamond. Tungsten is a dull silver-colored metal with the highest melting point of any pure metal. Pure tungsten melts at a whopping 6,192 degrees F (3,422 degrees C) and won’t boil until temperatures reach …
Read More » -
1 July
Fiber Optics transmission system and component technologies for Rising Internet traffic
Optical communications make use of light waves, very high frequency (100 terahertz) electromagnetic waves, for information transmission. Modern optical communications were begun in the 1960s, when lasers were invented as a coherent light source. Since then, the rapid development of photonic technologies has made possible optical communication links with a …
Read More »
 International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis