Material coatings on Ships and Submarine hulls reduce drag, enhance stealth and prevent marine growth, …
Read More »Masonry Layout
Military Embedded systems technologies enter large market growth driven by geopolitical rivalry and regional tensions
An “embedded system” is a word made by shortening “computer embedded system” meaning a system …
Read More »Graphene Bolometers emerging as high speed and sensitive Quantum photon detectors for quantum computation and quantum communication
Measurement connects the world of quantum phenomena to the world of classical events. It has …
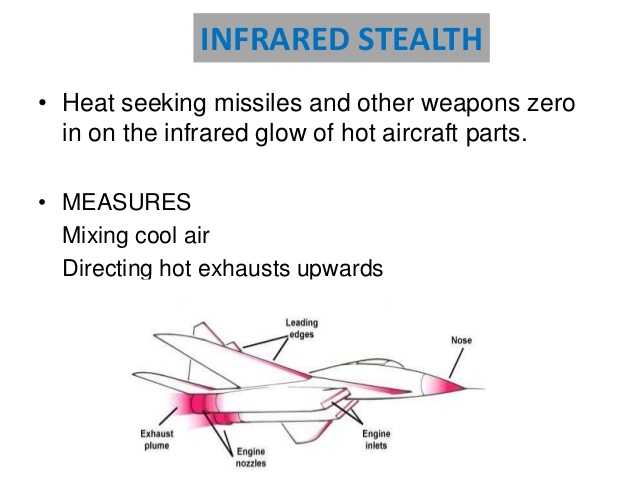
Read More »Infrared Search and Track (IRST) emerging as preferred solution for engaging stealthy aircraft and cruise missiles
Stealth has revolutionized the Air power by vastly enhancing the penetration capabilities of fifth generation …
Read More »Navy developing next generation Submarine Monitoring Network technologies for Antisubmarine warfare (ASW)
Anti-submarine warfare (ASW) has always been a game of hide and seek, with adversarial states …
Read More »Emerging field neuromodulation, or biostimulation, or electroceuticals, is emerging as an alternative to costly chemical and biologic drugs.
The human body is electric. Peripheral nerves connect all organs to the central nervous system, …
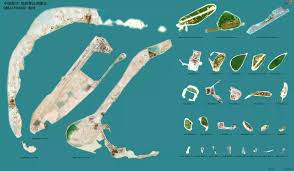
Read More »Countries building Artificial islands for economic progress, establishing industry,and exerting geopolitical and military control
An artificial island or man-made island is an island that has been constructed by people …
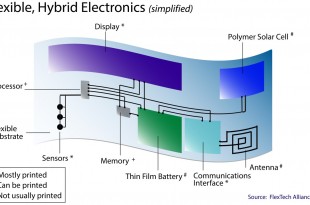
Read More »Printed and flexible electronics (PFE) revolution require Smart manufacturing concepts and printing technologies
While the conventional electronics like computers and smartphones is built around silicon integrating billions of …
Read More »Military requires Printed and flexible electronics (PFE) and Hybrid Systems enabling Internet of Things, Sensors on Aircrafts, to soft robotic exoskeletons
While the conventional electronics like computers and smartphones is built around silicon integrating billions of …
Read More »DARPA’s LUMOS to develop Photonic integrated circuits (PICs) and photonics platforms for defence applications
Photonics is a breakthrough technology as it uses photons (smallest unit of light) as the …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis