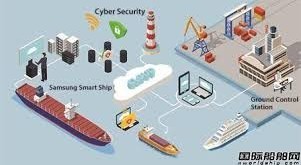
Broadly speaking, cloud computing refers to the practice of remotely storing and accessing information and software programs on demand, instead of storing data on a computer’s hard drive or accessing it through an organization’s intranet. This practice relies on a cloud infrastructure, a collection of hardware and software that may …
Read More »“Smart” technologies transforming shipping industry and ports by improving quality, increasing productivity and lowering costs
Shipping is the lynchpin of a global economy between exporters and importers. Today, about 90% of the world’s goods are transported by water connecting with various land transfer systems, such as rail, truck, and air.” Globalization has fueled huge growth in the shipping industry. Low-cost shipping is the means that …
Read More »Militaries designing Next Generation Urban Assault Combat Vehicles effective in megacities for urban warfare
Current Ground combat vehicles, especially main battle tanks (MBT) and infantry fighting vehicles (IFV), are the mainstay of technologically superior armies. The combination of firepower, mobility and survivability allows such vehicles to dominate ground military operations. Military planners expect GCVs to fight in relatively open terrain, where threats come from …
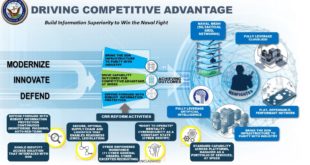
Read More »US Navy’s Information Superiority Vision is to modernize, innovate, defend platforms and developing a culture of information readiness
The Department of the Navy Chief Information Officer Aaron Weis has released the DON Information Superiority Vision in Feb 2020 which conveyed the DON’s vision for information superiority through our information, modernized network design, and our workforce; and defines our way forward. As stated by General David H. Berger, …
Read More »Multistatic Sonar Technology has become key to Anti Submarine Warfare (ASW) operations
Three decades ago, only a handful of major powers had effective submarine capabilities but, today, fleets in operation around the world are growing rapidly. Emerging superpowers, like China, can add naval capacity equivalent to a European country’s in the space of a few years. The threat from submarines is serious …
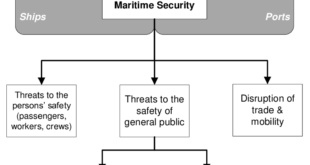
Read More »Rising Maritime threats require Smart Ports, Ship security and safety technologies to improve security and stability of maritime domain
The oceans are vital to the overall growth of the world economy and population, and to the continued economic integration of nations. The oceans are a primary source of food, energy, and transportation, all key requirements of human activity in an interconnected world. They are also essential to meet the …
Read More »Psychological warfare becoming sophisticated with development of new tools and technologies
Psychological warfare involves the planned use of propaganda and other psychological operations to influence the opinions, emotions, attitudes, and behavior of opposition groups. The targets of such propaganda campaigns can include governments, political organizations, advocacy groups, military personnel, and civilian individuals. While all nations employ it, the U.S. Central …
Read More »Navies require Automated AUV Launch and Recovery System for a variety of Ships , USVs or submarine platforms
UUVs—submersible unmanned vehicles—are divided into two categories: remotely operated underwater vehicles (ROVs) and autonomous underwater vehicles (AUVs). ROVs are controlled and powered by a person or crew on either land or neighboring craft via an umbilical or using remote control. The truly autonomous AUV systems are typically deployed from a …
Read More »India and Russian Defence cooperation advancing to joint research, development and production of advanced defence technologies and systems
Indo-Russian relationship have stood the test of time established since Indian independence . Soviet Union had a cardinal role in setting the foundations of Indian industrial base. Eight of India’s 16 heavy industry in the period 1956-61 were built with Soviet help.In 1971 the two countries signed the Treaty of …
Read More »Lawfare, or legal warfare as means of realizing a military objective
Legal warfare, at its most basic, involves “arguing that one’s own side is obeying the law, criticizing the other side for violating the law [weifa], and making arguments for one’s own side in cases where there are also violations of the law.” Lawfare, or legal warfare, exploits “all aspects of the …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis