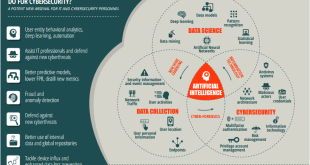
In recent years, the integration of artificial intelligence (AI), machine learning (ML), and deep learning (DL) technologies has revolutionized various sectors, and the military is no exception. These advanced technologies offer unprecedented opportunities to enhance operational capabilities, improve decision-making processes, and transform traditional warfare strategies. However, their adoption also presents …
Read More »Vulnerability Management: A Guide for Organizations
Imagine your organization as a digital fortress. No matter how strong the walls, even the most secure castle can be breached if there’s a weak point. That’s where vulnerability management comes in – it’s the process of identifying, prioritizing, and addressing weaknesses in your IT systems and software. All systems …
Read More »Autonomous Cyber AI for defence from AI-enabled cyber crime and AI enabled cyber Warfare by adversaries
Artificial intelligence (AI) and machine learning (ML) are advancing at an unprecedented pace, ushering in a new era of technological capabilities with widespread applications across various industries. From enhancing medical diagnostics to enabling autonomous vehicles, the benefits of AI are evident. However, alongside these advancements, AI also presents a potent …
Read More »Shielding the Arsenal: US Air Force Invests in Anti-Tamper Tech
The US Air Force is taking a crucial step to safeguard its technological edge by investing nearly half a billion dollars in anti-tamper technologies. This initiative, spearheaded by the Air Force Life Cycle Management Center, aims to equip military electronics with robust defenses against adversaries seeking to steal sensitive information …
Read More »Understanding QR Code Technology and Cyber Threats: Staying Safe in a Digital World
QR codes, those ubiquitous black and white squares, have become an ingrained part of our daily lives. From restaurant menus to train tickets, they offer a quick and easy way to access information on our smartphones. But with this convenience comes a potential security risk – malicious QR codes. QR …
Read More »Nation-Backed Cyber Attacks: The Global Threat Posed by Russia, China, North Korea, and Iran
In today’s interconnected world, cyberspace has become the new battleground for global dominance. Nation-states are increasingly leveraging cyber capabilities to conduct espionage, steal intellectual property, and destabilize geopolitical rivals. Among the most notorious actors in this domain are Russia, China, North Korea, and Iran. These countries have been implicated in …
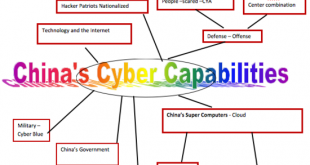
Read More »China’s Cyber Warfare Threat: A Looming Danger to US Infrastructure
The United States faces a complex and ever-evolving threat landscape, and one of the most concerning aspects comes from cyberspace. China’s cyberwarfare capabilities have been steadily growing, posing a significant risk to US critical infrastructure, national security, and economic well-being. In a stark warning to lawmakers, FBI Director Christopher Wray …
Read More »Outsmarting the Honey Trap: Technology’s Role in Counterintelligence
The world of espionage is filled with intrigue and deception, and one method that’s been around for centuries is honey trapping. This tactic involves using romantic or sexual relationships to gain access to sensitive information. But in today’s tech-driven world, even spies are facing a new challenge: counterintelligence powered by …
Read More »Global Cybersecurity Outlook 2024: Bridging the Cyber Resilience Divide
In today’s digital age, cybersecurity has become a paramount concern for organizations of all sizes. As technology continues to advance, so do the threats posed by cyberattacks. A recent cybersecurity report sheds light on the progress made in organizational cyber resilience while also highlighting areas of concern and avenues for …
Read More »NCSC Assessment: Evaluating the Impact of Artificial Intelligence on Cyber Threats
As the digital landscape continues to evolve, the intersection of artificial intelligence (AI) and cybersecurity emerges as a focal point for policymakers and security experts alike. The National Cyber Security Centre (NCSC) Assessment (NCSC-A) provides invaluable insights into the evolving cyber threat landscape, particularly concerning the potential impact of AI …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis