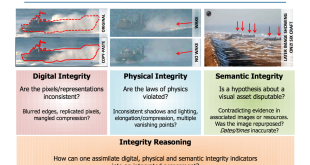
The number of threats organizations face continues to go up. Attacks grow more sophisticated and target more widely. Current security tools are very good at flagging up anomalies but not so good at defining their impact and risk potential. The result is a hailstorm of alerts, most of which need …
Read More »SpaceChain deploys Internet of blockchains , other Countries also plan Blockchain space technology,
Historically, there was a necessity for a third party that demanded a payment to perform transactions or submit information to ensure the accuracy of transactions and create a reliable history. Blockchain eradicates the need for an intermediary through creating a trustless medium of exchange and immutable public ledger. It creates …
Read More »DARPA Media forensics to detect fake photos and videos on social media to support National Security
In recent years consumer imaging technology (digital cameras, mobile phones, etc.) has become ubiquitous, allowing people the world over to take and share images and video instantaneously. Mirroring this rise in digital imagery is the associated ability for even relatively unskilled users to manipulate and distort the message of the …
Read More »Blockchain technology of decentralized digital currency to enhance security of additive manufacturing in Internet of Things to Military 3D printing
Blockchain is based on open, global infrastructure, decentralized public ledger of transactions that no one person or company owns or controls, ensures security of transfer of funds through public and private cryptology and third parties to verify that they shook, digitally, on an agreement. A blockchain is, in the simplest …
Read More »Quantum Cryptography emerging alternative to secure Military Internet of things (MIOT) from cyber attacks even in post Quantum Computer Era
The Internet of things (IoT) is the network of physical devices, vehicles, home appliances and other items embedded with electronics, software, sensors, actuators, and connectivity which enables these objects to connect and exchange data. Each thing is uniquely identifiable through its embedded computing system but is able to inter-operate within the …
Read More »Hacking of Electronic Voting Machines is a threat to Democracy, DARPA Is Building a Open Source, Secure Voting System
The introduction of the electronic voting machines in India at the turn of the century had aided in reducing instances of capturing of polling stations and stuffing of ballot boxes by mobs hired by political parties. Using data from state elections, researchers Sisir Debnath, Mudit Kapoor and Shamika Ravi studied the …
Read More »DARPA’s RACE developing Secure Messaging Platform to provide WhatsApp like communication for troops on ground
Military is integrating Smartphones and tablets into their military operations, to enhance situational awareness and as backup communication in denied situations. Marines are considering airborne operations with tablets, Air Force looks at maintenance efficiencies, they have also widely used for training and education. They are also using ruggedized cases to …
Read More »Attacking ISIS by Cyber warfare and dropping cyber bombs was new strategy implemented by US, UK & Australia
United States opened a new line of combat against the Islamic State, directing the military’s eight-year-old Cyber Command for the first time to mount computer-network attacks that are now being used alongside more traditional weapons. In 2009, US established, USCYBERCOM for more effective and coordinated efforts for conducting cyberspace operations. Cyber Command, …
Read More »Cyber criminals favouring stealthier attacks like Cryptojacking to make free money
Cyber criminals are switching away from ransomware to stealthier attacks as the main sources of generating revenue, according to analysis by British artificial intelligence (AI)-based cyber security firm Darktrace. Cryptojacking is the unauthorized use of someone else’s computer to mine cryptocurrency. Cryptocurrency is a form of digital currency that can …
Read More »Future Global Quantum internet could be brought down by Quantum terrorists
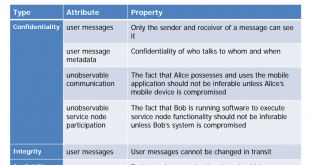
Quantum cryptography is an emerging technology in which two parties may simultaneously generate shared, secret cryptographic key material using the transmission of quantum states of light. A unique aspect of quantum cryptography is that Heisenberg’s uncertainty principle ensures that if Eve attempts to intercept and measure Alice’s quantum transmissions, her …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis