As society become increasingly digital, financial services providers are looking to offer customers the same services to which they’re accustomed, but in a more efficient, secure, and cost effective way. Blockchain’s conceptual framework and underlying code is useful for a variety of financial processes because of the potential it has …
Read More »DARPA GAPS program developing hardware and software architectures that can provide physical security like air-gaps
Today, modern computing systems are incapable of creating sufficient security protections such that they can be trusted with the most sensitive data while simultaneously being exposed to untrusted data streams.” “Therefore, for the most sensitive computing systems, [the Department of Defense] and commercial industry have in certain places adopted a …
Read More »Militaries developing Cyber Testbeds to test and validate strategies, tactics and security measures for Cyber Warfare
All over the world Cyber attacks are becoming increasing in number and sophistication. Many organizations in Europe and the US have been crippled by a ransomware attack such as “Petya” , WannaCry or WannaCrypt ransomware attack affected more than 230,000 computers in over 150 countries. Number of incidents such as …
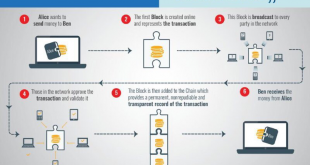
Read More »Countries race to employ Blockchain, the virtual currencies technology, for tamper-proof military systems and cybersecurity
Blockchain is a transformative technology for the two billion people in the world currently underserved by financial institutions. The technology has the potential to enhance privacy, security and freedom of conveyance of data. Blockchain is based on open, global infrastructure, decentralized public ledger of transactions that no one person or …
Read More »Supercomputers can assist in Cyber Security by Identifying threats, detecting anomalous behaviour and finding software vulnerabilities
Supercomputers have become essential for National Security, for decoding encrypted messages, simulating complex ballistics models, nuclear weapon detonations and other WMD, developing new kinds of stealth technology, and cyber defence/ attack simulation. Because of the expense, supercomputers are typically used for the most intensive calculations, like predicting climate change, or …
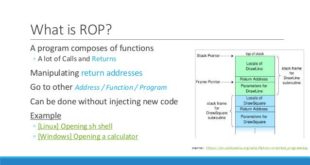
Read More »Industry developed new approach to protect against advanced ‘ROP’ Cyberattacks
Today’s cybersecurity playing field is fundamentally asymmetric. Attackers are easily able to identify weaknesses in a target system once they have access to its code and configuration. As a result, defenders are perpetually playing a game of catch-up to secure their systems post-attack. ROP attacks are particularly insidious in …
Read More »Cyber risks of Video-conferencing apps like Zoom, popular with professionals working from home globally
Video conferencing apps like Zoom have become popular with professionals working from home globally, who are using it for virtual meetings, presentations and calls. Millions of people have turned to the app as they work and study from home amid the global lockdown. In India too it had become the …
Read More »High-assurance Network encryptors secure voice, video, and data moving over public and private IP networks
Protecting network transmitted data against cyber attacks and data breaches is imperative for government agencies. Data network eavesdropping, innocent error or technical failure, data tampering and data theft have all become commonplace. The implications of a significant breach are often catastrophic. Encryption is a popular and effective method …
Read More »Global threat Intelligence and warnings shared by Cyber Agencies enables mitigating cyber threats before large scale exploitation by hackers
According to the World Economic Forum’s 2016 Global Risks Report, cyber-security is recognised as one of the greatest threats to business worldwide, and the global cost of crimes in cyberspace is estimated to be $445bn. By 2021, cybercrime damage is estimated to hit $6 trillion annually. To put that in …
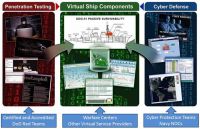
Read More »Cyber attacks as big a threat to warships as missiles and torpedoes, Navies develop cyber security policy and risk management
The maritime sector is on the verge of a digital disruption. As digital transformation of the maritime sector is gathering momentum that will have a major impact on operations and existing business models, simultaneously the threat cyber attacks is emerging. Further the sector’s infrastructure will be exposed to more and …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis