Outsourcing of integrated circuit (IC) and printed circuit board (PCB) design, fabrication, packaging, and testing have dramatically reduced the time and cost of product development. In doing so, this has enabled the widespread availability of microelectronics, which has indeed transformed modern life. However, unintended consequences include malicious design alteration (i.e., …
Read More »Threats to ICT supply chains including Counterfeit electronic components and Hardware Trojans present critical risk to military and security systems
Information and communications technology, encompassing digital services and infrastructure, cybersecurity and software, is ubiquitous throughout the economy and society. As the digital transformation gathers pace, the number and complexity of ICT services is accelerating. Information and Communications Technology (ICT) relies on a complex, globally distributed, and interconnected supply chain …
Read More »Commercialization of cybercrime leading to rising global threat of Cyber outsourcing or Cybercrime-as-a-Service
Cybercrime is the greatest threat to every company in the world, and one of the biggest problems with mankind. Beyond a nefarious hobby, cybercrime has become a way for cybercriminals to earn a living. While it remains underground, it is a business nonetheless; attackers cooperate, and work to maximize profits …
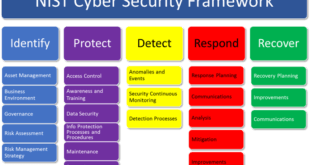
Read More »NIST Cybersecurity Framework Improving Critical Infrastructure Cybersecurity by managing it’s cyber risks
Cybersecurity Ventures predicts cybercrime will cost the world in excess of $6 trillion annually by 2021, up from $3 trillion in 2015. The NIST Framework for Improving Critical Infrastructure Cybersecurity, commonly referred to as the NIST Cybersecurity Framework (CSF), provides private sector organizations with a structure for assessing and improving …
Read More »With Cyber becoming operational domain of warfare, Militaries establish Cyber commands and develop offensive cyberwarfare capabilites
Cyber warfare has developed into a more sophisticated type of combat between countries, where you can destroy communications and other digital infrastructure of adversaries. Cyberwarfare involves digital attacks on the networks, systems and data of another state, with the aim of creating significant disruption or destruction. That might involve destroying, altering …
Read More »Industry developing security solutions like Hardware security module (HSM) for secure military unmanned platforms, sensors, and communication devices
Hardware Trojans (HT), which are malicious circuit inclusions into the design from an adversary with an intention to damage the functionality of the chip at a much later date or leaking confidential information like keys used in cryptography. Time to market demand has forced integrated circuit design, manufacturing and testing …
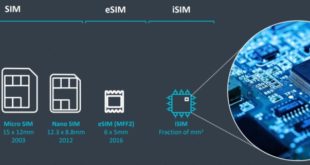
Read More »Embedded eSIM and iSIM are breakthrough IoT connectivity technologies for authenticating subscribers and devices on mobile networks
Strong IoT device authentication is required to ensure connected devices on the IoT can be trusted to be what they purport to be. Consequently, each IoT device needs a unique identity that can be authenticated when the device attempts to connect to a gateway or central server. With this unique …
Read More »Growing Threat of Biohacking or DNA Malware with development of DNA based Biocomputers and memories
Recently biocomputers are becoming feasible due to advancements in nanobiotechnology and Synthetic Biology. Biocomputers use systems of biologically derived molecules—such as DNA and proteins—to perform computational calculations. It is expected that the most significant advantage of the DNA chip will be parallel processing. Scientists are also using DNA for …
Read More »Intelligence agencies prepare for post quantum world when current public key cryptology will be easily broken by quantum Computers
Modern cryptography being used extensively for securing our internet payments, banking transactions, emails and even phone conversations use cryptographic algorithms based on public-key encryption, which is considered to be secure against attacks from modern computers. The development of quantum computers once seen as a remote theoretical possibility is now …
Read More »Blockchain & Cryptocurrency breakthroughs to transfer funds safely, quickly, anonymously and energy efficiently
As society become increasingly digital, financial services providers are looking to offer customers the same services to which they’re accustomed, but in a more efficient, secure, and cost effective way. Blockchain’s conceptual framework and underlying code is useful for a variety of financial processes because of the potential it has …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis