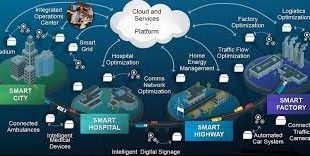
A smart home refers to a convenient home setup where appliances and devices can be automatically controlled remotely from anywhere with an internet connection using a mobile or other networked device. Devices in a smart home are interconnected through the internet, allowing the user to control functions such as security …
Read More »Smart home devices have many security risks and threats to be exploited by hackers and Intelligence agencies for mass surveillance
The rise of the digital era has brought with it many wondrous changes to our daily lives, not least of which the fact that we now carry digital assistants with us everywhere we go in the form of smartphones, tablets, and laptop computers. At the same time this has also …
Read More »Driverless cars vulnerable to hacking and could be used to carry out suicide attacks, Researchers developing new security solutions
Automotive industry is currently undergoing an electrification process. In a few years, every new vehicle sold will have some degree of autonomy built in. Carmakers from Google to Apple, Tesla to Volkswagen are trying to make drivers obsolete, handing control of the wheel to a computer that can make intelligent decisions …
Read More »After initial Hype and amid Cyber Warfare threat, Network Centric Warfare approach is now being adopted realistically in various Militaries
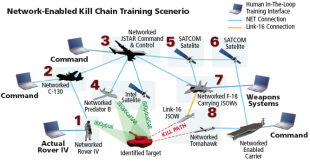
As the 21st Century battlefield becomes increasingly complex and asymmetrical, military forces are striving to harness network technology to gain an operational advantage, by transforming traditional linear command structures and linking sensors, unmanned vehicles, command posts and ground troops to achieve decision superiority for full spectrum dominance. Network Centric …
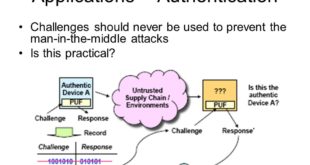
Read More »Threats of hacking of digital IDs, driving develpment of unbreakable Quantum EPUF IDs containing 1,000 trillion atoms
We live in digitised, connected societies, in an Internet of Things (IoT) world where our reliance on software, hardware, and the networks that connect us, grows exponentially. Our increasing global reliance on what we hope and assume are secure networks, is profound. The threat of large-scale cyber-attack has become a …
Read More »DARPA CHARIOT developing Quantum proof cryptography for Military Mobile and IoT security
The exponential price/performance improvements in semiconductor technology stemming from Moore’s Law are enabling even the smallest and most application-specific devices, such as sensors and actuators, to include networking capabilities. The overwhelming majority of such devices will be cheap and power-constrained. Low device costs permit deployment in unprecedented numbers, with some …
Read More »Cyber Security Situational Awareness tools on Defense Platform Networks are critical for Cyber Warfare
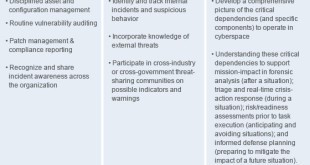
Cyberspace is understood as the fifth domain of warfare equally critical to military operations as land, sea, air, and space. Success of military operations in the physical domains is increasingly dependent on the availability of, and access to, cyberspace. The armed forces are reliant on cyberspace both as a user …
Read More »DARPA HACCS employing AI for cybersecurity by developing autonomous software agents, that will infiltrate adversary’s networks, detect botnets and neutralize them
As the complexity of software is growing software vulnerabilites are also increasing. According to two US based organizations that track vulnerability disclosure, the number of software vulnerabilities has gradually grown year-over-year achieving its highest peak in 2017. Computers are not patched reliably, configured properly, or used safely, allowing widespread exploitation. …
Read More »COVID-19 is enhancing Terrorism, Cyberattacks, and Bioterrorism threats in the world
The head of the World Health Organization is warning that the COVID-19 pandemic is speeding up, and he criticized governments that have failed to establish reliable contact tracing to stop the spread of the coronavirus. According to the latest tally from Johns Hopkins University, there have been more than 10 …
Read More »Under Cyber Warfare threat from China and Pakistan, India steps up cyber security measures and operationalising its Cyber Command
Cyber warfare has developed into a more sophisticated type of combat between countries, where you can destroy critical infrastructure such as power, telecommunications or banking by damaging the computer systems that control those infrastructures. It’s widely acknowledged that offensive cyberattacks will be a necessary component of any future military campaign, …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis