The nation’s critical infrastructure is increasingly dependent on the Internet, while cybersecurity attacks are on the rise. Cybersecurity threats are becoming more frequent, more sophisticated, and more destructive—gradually eroding society’s trust in digital infrastructure. As technology continues to advance and every facet of daily life becomes increasingly interconnected, both the …
Read More »Challenge of Attribution of Malicious Cyber Actors amidst growing Cyber attacks and Cyberwarfare
Cyber warfare refers to the use of technology to launch attacks on nations, governments and citizens, causing comparable harm to actual warfare using weaponry. Cyberwarfare has developed into a more sophisticated type of combat between countries, where you can destroy critical infrastructure such as power, telecommunications or banking by damaging …
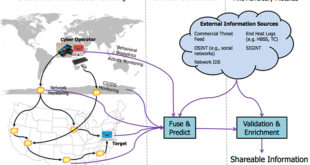
Read More »DARPA EA developed tools for timely, accurate threat information and Attribution of Malicious Cyber Actors like Russia and China
Malicious actors in cyberspace currently operate with little fear of being caught due to the fact that it is extremely difficult, in some cases perhaps even impossible, to reliably and confidently attribute actions in cyberspace to individuals. The reason cyber attribution is difficult stems at least in part from a …
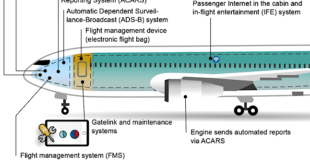
Read More »Cyber Security of Aircraft avionics on commercial and military aircrafts
Avionics are the electronic systems used on aircraft. Aircraft avionics is the most crucial component of aircraft systems and helps in providing various operational and virtual information in-flight and on the ground. The avionics system receives data from the air traffic management system and feeds this information to the pilot …
Read More »Growing cyber attacks require Organization Incident response plan
The accelerating pace of digitalisation, fuelled by the COVID-19 pandemic, has led to a record-breaking year for cybercrime with ransomware attacks rising 151 per cent in 2021, and an average of 270 cyberattacks per organisation being faced, a new study showed in Jan 2022. The World Economic Forum’s ‘Global …
Read More »Critical Infrastructure Protection Market
Networked technologies touch every corner of the globe and every facet of human life. They have driven innovation, nurtured freedoms, and spurred economic prosperity. Even so, the very technologies that enable these benefits offer new opportunities for malicious and unwanted cyber activities. Cyber-attacks are continuously growing in size and breadth, targeting …
Read More »DARPA HACMS employed Formal Verification Methods to develop hack proof unmanned vehicles , weapons , satellites, and command and control systems
In 2011, Iran claimed to have downed a sophisticated American stealth drone, and unveiled what it alleged was a reverse-engineered copy of the futuristic looking RQ-170 Sentinel UAV, produced by defense giant Lockheed Martin. The drone was brought down by the Iranian Armed Forces’ electronic warfare unit which commandeered the …
Read More »UK Cyber Security Strategy emphasizes Defence , Deterrence and Cyber technology development
The rapid development of digitalized services and online shopping in the UK has been paralleled with significant growth in cybercrime, leading to greater spending on security in public and private sectors. Organizations’ IT footprints have also become increasingly complex, driving demand for more sophisticated and bespoke cyber solutions. There …
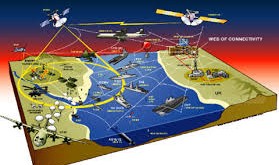
Read More »US DOD establishing Cyber Ranges and testbeds with Live-Virtual-Constructive (LVC) simulation under CyberWarfare Threat
As World is becoming more digitized, its National Critical Information Infrastructure assets in critical sectors like energy, banking, defence, telecom, transportation etc. have becoming more vulnerable to cyber attacks like the use of ransomware to hold assets at risk, disabling of CII threatening domestic public safety. In the Future, IOT will …
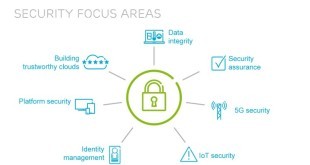
Read More »5G Mobile Networks deployments have many security and privacy threats, Require New policies and technologies including quantum cryptography
Countries are now racing to deploy 5G, short for 5th generation mobile networking or 5th generation wireless systems. The Fifth Generation (5G) mobile networks promise fast Internet for everyone, smart cities, driverless cars, critical health care, “internet of things” revolution, and reliable and secure communications for critical infrastructures and services. The …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis