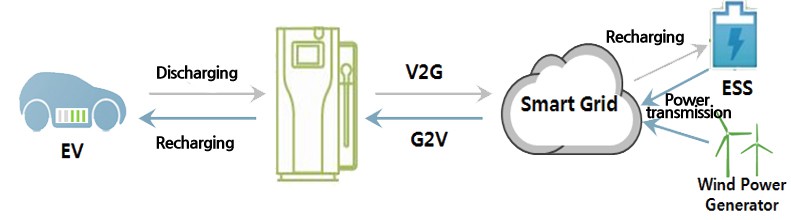
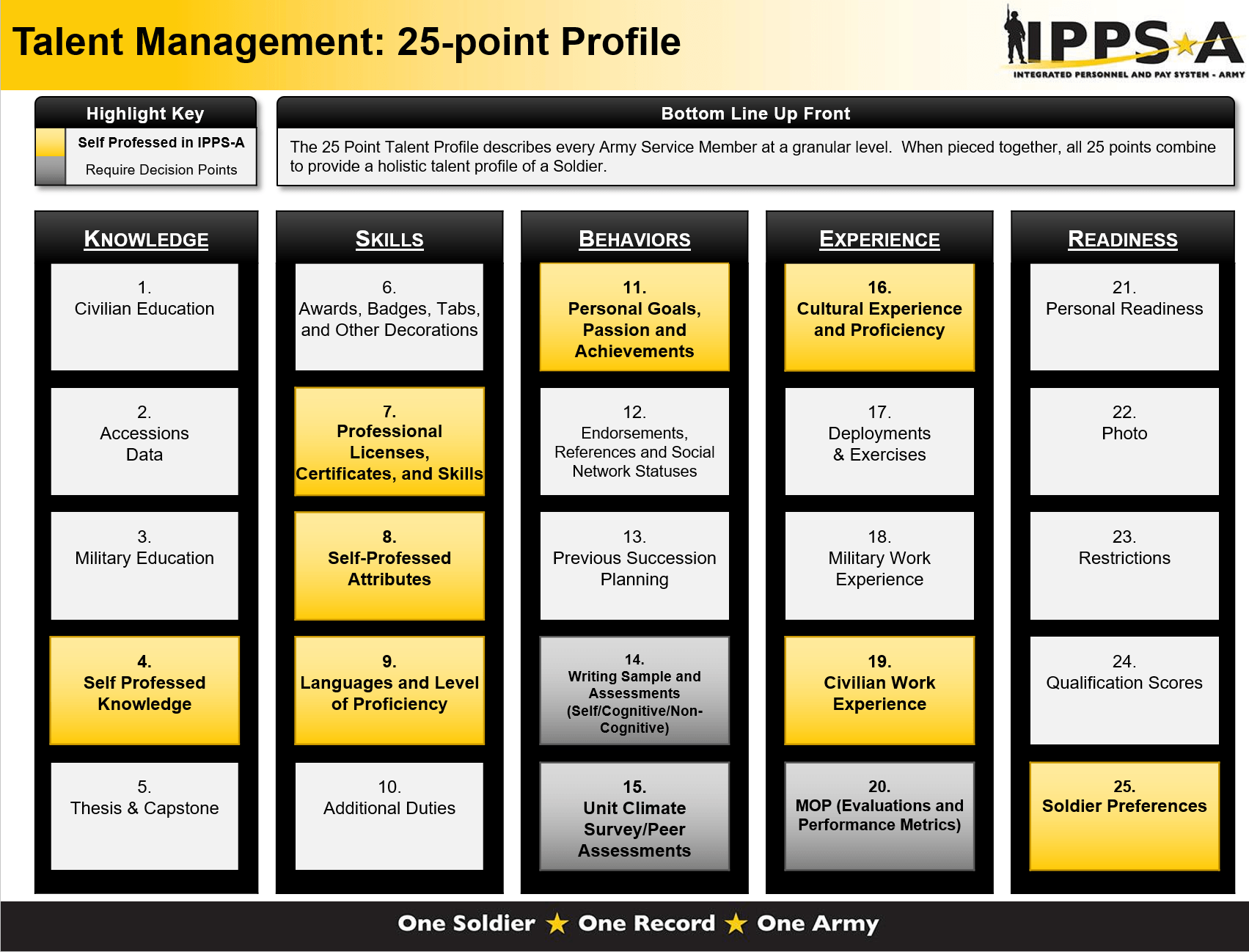
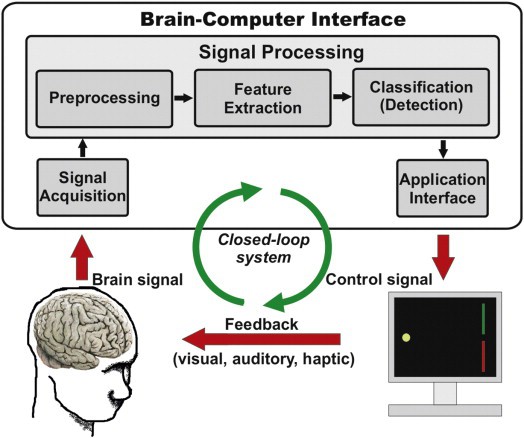
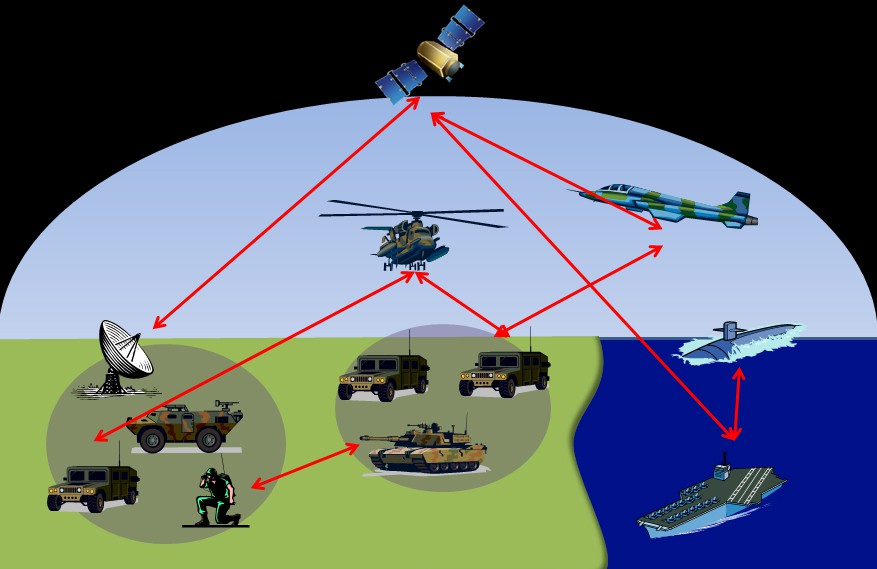
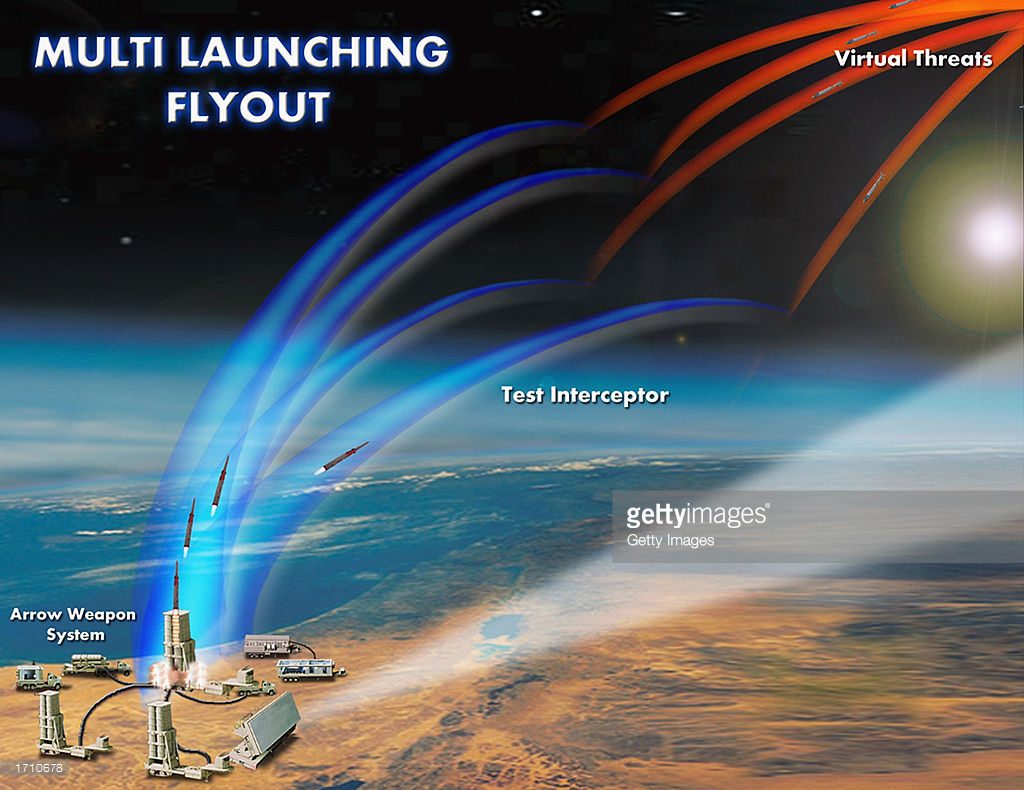
India and Russian Defence cooperation advancing to joint research, development and production of advanced defence technologies and systems

Indo-Russian relationship have stood the test of time established since Indian independence . Soviet Union had a cardinal role in setting the foundations of Indian industrial base. Eight of India’s 16 heavy industry in the period 1956-61 were built with…...