Quantum key distribution (QKD), establishes highly secure keys between distant parties by using single photons to transmit each bit of the key. A unique aspect of quantum cryptography is that Heisenberg’s uncertainty principle ensures that any attempts to intercept and measure quantum transmissions, will introduce an anomalously high error rate …
Read More »Military Sensor Fusion technology enhances situational awareness of Air, Sea and Space-based platforms and Remote Intelligence
The military typically operates in demanding, dynamic, semi-structured and large-scale environments. This reality makes it difficult to detect, track, recognize/classify, and response to all entities within the volume of interest, thus increasing the risk of late (or non-) response to the ones that pose actual threat. A key challenge facing …
Read More »Quantum Entanglement advances enables Quantum Computers, high-speed ultra secure communications, high precision Quantum Sensors and Imaging
The extraordinary promise of quantum technology—depend on quantum “entanglement,” in which the physical states of two or more objects such as atoms, photons or ions become so inextricably connected that the state of one particle can instantly influence the state of the other—no matter how far apart they are. Entanglement links …
Read More »Electro-optical Circuit Board (EOCB) enable photonic integrated circuits, autonomous cars and even quantum computers based on light
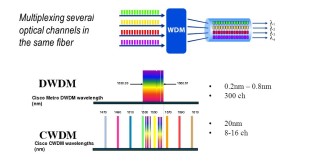
As copper reaches its speed limit, engineers look at optics to replace copper for very high speed signals. The electronic transmission of information requires energy – the faster the interface, the more electrical power is required. At very high data transfer rates, optical interfaces can be significantly more efficient than …
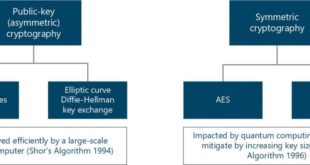
Read More »Industry preparing for Post Quantum or Quantum proof cryptography as Quantum computers threaten global communication digital infrastructure
Cryptography is a vital part of cybersecurity. Security properties like confidentiality, integrity, authentication, non-repudiation rely on strong cryptographic mechanisms, especially in an always connected, always online world. In addition, cryptography’s applications open up new opportunities and markets: digital signatures or online transactions would not be possible without it. Quantum …
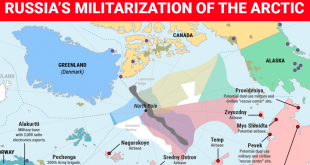
Read More »As melting ice bringing Arctic into geostrategic prominence, Russia quickly establishes its military dominance over it
The Arctic is currently a staggering 36 degrees warmer than normal at this time of year, according to information from the Danish Meteorological Institute. NASA report also shows that a vast region in the Arctic Ocean has gone missing and people from NASA think that the polar ice caps are …
Read More »US Army Optionally Manned Fighting Vehicle (OMFV) programme to replace its M-2 Bradley Infantry Fighting Vehicle (IFV)
The M-2 Bradley is an Infantry Fighting Vehicle (IFV) used to transport infantry on the battlefield and provide fire support to dismounted troops and suppress or destroy enemy fighting vehicles. The M-2 has a crew of three—commander, gunner, and driver—and carries seven fully equipped infantry soldiers. M-2 Bradley IFVs are …
Read More »Militaries adopting rugged 5G enabled Notebooks, tablets and smart phones into tactical operations, however their vulnerability requires secure solutions
Military is increasingly looking to commercial ICT devices like Smartphones and tablets and they are rapidly making their way into military operations. Mobility continues to transform how the Department of Defense (DoD) operates, connects, and supports its stakeholders – most significantly, through the use of commercial mobile solutions to provide …
Read More »Countries racing to develop Digital apps for giving military the warfighting edge
Recent growth and advances in mobile computing and communication have revolutionized the way we live and access information. Today we are able to receive and process a vast amount of real-time data and situational information on mobile devices in a manner that has not been witnessed previously. US Department …
Read More »Next generation Military Communications technologies enabling high-throughput mobile, secure, survivable, seamless, in congested and contested environments
Communications is vital for War fighters to exchange voice and data, command and control and situational awareness data and video. The vision of Communications area is to provide reliable communication from anywhere to everywhere from war fighters to supreme commander with demanded rate and least latency by exploiting complete electromagnetic …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis