Software is everywhere and is in almost everything that the Department operates and uses. Software drives our weapon systems; command, control, and communications systems; intelligence systems; logistics; and infrastructure, and it drives much of the backroom enterprise processes that make the Department function. If cyber is the new domain in …
Read More »Monthly Archives: April 2021
Future Smart Soliders require Man-portable military electronic systems
The vision for the future soldier is to be combat effective and also highly mobile, adaptive, networked, sustainable with total battle space situation awareness and information assurance. Therefore, he is equipped with night- vision goggles, radios, smartphones, GPS, infrared sights, a laptop as well as batteries to power them. …
Read More »France thrust on counter terrorism initiatives after glaring security gaps exposed by brazen attacks
France suffered a series of deadly terror attacks in November 2015. In 2015, the brazen murders of 17 innocent people, in three separate attacks in as many days, have revealed serious breaches and lapses in the French system of intelligence, surveillance and security, according to numerous counterterrorism experts. In July …
Read More »DARPA CONCERTO developing single reconfigurable UAV payload for communications, radar and electronic warfare functions to enhance UAS adaptability and mission efficiency
Unmanned Aerial Systems are gaining more importance every single day. Unmanned Aircraft Systems (UAS) are used for both defensive and offensive purposes. Different sizes and capabilities of UAS support a variety of different applications. Improved networking capabilities have enlarged the boundaries of UAS operations. Nations are working on more complex and …
Read More »Changing role of Military Scientific and Technical Intelligence ( S&TI)
If the Militaries are to fight and win in future wars, it must thoroughly understand the challenges that it will face and how those challenges will impact the way it intends to fight. It must act now to ensure that it possesses a technological edge over its adversaries. This is …
Read More »DARPA OPS-5G to mitigate security threats facing 5G and future wireless networks in military appliations
5G is the latest in a series of evolutions in public mobile networking, with widespread coverage and access on a subscription basis. 5G networks are characterized by improved capabilities across a variety of measures, including throughputs, latencies, numbers of devices, and battery life. 5G is used to attach small special …
Read More »Militaries developing wide range of aircrafts for electronic-warfare capable of tactical jamming to ectronic attack
All modern forces depend on unimpeded access to, and use of, the EM spectrum in conducting military operations. Therefore, there is a requirement to gain and maintain an advantage in the electromagnetic spectrum by countering adversary’s systems and protecting one’s own systems. Thus the EM spectrum can no longer be …
Read More »IARPA pursues anticipatory intelligence to predict the unpredictable , Video to open source collection & analysis to Quantum amd Exascale computing
The Intelligence Advanced Research Projects Activity (IARPA) is an organization within the Office of the Director of National Intelligence that funds high-risk, high-payoff research to overcome difficult challenges relevant to the United States Intelligence Community. IARPA was given the mandate to conduct cross-community research, target new opportunities and innovations, and …
Read More »Quantum cryptography vulnerable to hacking too, Researchers developing hackerproof MDI QKD schemes to enhance network encryption
With the age of quantum computing drawing ever-closer, traditional encryption methods are at risk. While brute force attacks can take months to break through security, quantum attacks can use more advanced techniques to break standard public key cryptography in a much shorter timeframe. Quantum cryptography is an emerging technology …
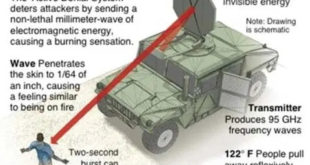
Read More »Electomagnetic Weapons can cause Havana syndrome, manipulate Nervous System to erase memories and cause extreme pain
Non-lethal weapons have been used by security forces to deter hostile crowds. They fill gaps between verbal warnings and lethal force. They have been found useful in disaster management like in the aftermath of the 2010 Haiti earthquake, where non-lethal weapons were used when riots occurred at food distribution sites. …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis