Early evidence suggests that there are trillions of dollars’ worth of minerals and metals buried in asteroids that come close to the Earth. These include phosphorus, antimony, zinc, tin, lead, indium, silver, gold and copper. The mining of resources contained in asteroids, for use as propellant, building materials or in …
Read More »Monthly Archives: February 2021
DARPA CHARIOT developing Quantum proof cryptography for Military Mobile and IoT security
The exponential price/performance improvements in semiconductor technology stemming from Moore’s Law are enabling even the smallest and most application-specific devices, such as sensors and actuators, to include networking capabilities. The overwhelming majority of such devices will be cheap and power-constrained. Low device costs permit deployment in unprecedented numbers, with some …
Read More »Solar fiber optic lighting for daylighting of high-rise intensive buildings and military shelters
Conventional daylighting scheme employing windows and skylights are no longer so useful especially for daylighting of high-rise and intensive buildings. Residential buildings with limited natural lighting are generally lit by fuel-based electricity which contributes to increase of CO2 concentration in the atmosphere. Alternatively, the concentrated solar energy can be transmitted …
Read More »Miniaturized RF passive components like filters, inductors and capacitors required for future 5G and IoT requirements
The RF design consists of passive as well as active components. The inductors, capacitors, and resistors are one of the three passive elements that are the foundations of all electronics. The discrete and passive components are an integral part of the design; from front-end antenna matching to tight-tolerance mixers, oscillators, …
Read More »Cyber Security Situational Awareness tools on Defense Platform Networks are critical for Cyber Warfare
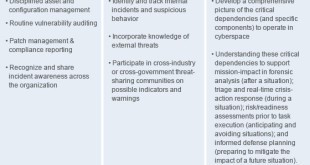
Cyberspace is understood as the fifth domain of warfare equally critical to military operations as land, sea, air, and space. Success of military operations in the physical domains is increasingly dependent on the availability of, and access to, cyberspace. The armed forces are reliant on cyberspace both as a user …
Read More »DARPA HACCS employing AI for cybersecurity by developing autonomous software agents, that will infiltrate adversary’s networks, detect botnets and neutralize them
As the complexity of software is growing software vulnerabilites are also increasing. According to two US based organizations that track vulnerability disclosure, the number of software vulnerabilities has gradually grown year-over-year achieving its highest peak in 2017. Computers are not patched reliably, configured properly, or used safely, allowing widespread exploitation. …
Read More »DARPA DeMi developing technologies for space based telescope on it’s military CubeSat satellite for Space Surveillance Awareness
The volume of space between the Earth’s surface out to geosynchronous orbit is enormous—equivalent to 240,000 times all the Earth’s oceans. Yet the number of objects calling that volume home is growing all the time—not just with satellites but with debris of all kinds, natural and manmade. And keeping track …
Read More »DARPA operationalizes Space Surveillance Telescope in Australia, earlier handed over to Air Force Space Command to protect satellites from orbiting junk and space weapons
A U.S.-developed space surveillance telescope has been assembled at a new facility in Western Australia and is expected to start operating in 2022, the U.S. Space Force Space and Missile Systems Center announced April 2020. The telescope, designed to track and identify debris and satellites more than 22,000 miles above Earth, …
Read More »Phased array antennas for phased array radars to satellite constellations to SATCOM On-The-Move (SOTM) on warships
Wireless electronic systems have been relying on dish antennas to send and receive signals. These systems have been widely used where directivity is important and many of those systems work well at a relatively low cost after years of optimization. These dish antennas having a mechanical arm to rotate the …
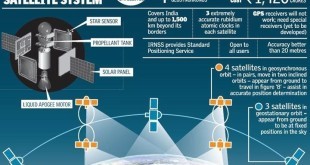
Read More »The denial of GPS services during Kargil War has driven ISRO to develop Indian Regional Navigation Satellite System (IRNSS), superior to GPS
The Global Positioning System (GPS), is a global navigation satellite system (GNSS) that provides location and time information in all weather conditions, anywhere on or near the Earth where there is an unobstructed line of sight to four or more GPS satellites. Each one transmits information about its position and …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis