Quantum chips perform computations using quantum bits, called “qubits,” that can represent the two states corresponding to classic binary bits — a 0 or 1 — or a “quantum superposition” of both states simultaneously. The unique superposition state can enable quantum computers to solve problems that are practically impossible for …
Read More »Yearly Archives: 2020
Plant Nanobionics or ePlants aim to turn plants into sensors detecting explosives, warn of pollutants and environmental conditions such as drought
Plant Nanobionics seeks to use designed nanoparticles to interface directly with plant cells and organelles to augment plant functions, as well as to introduce non-native functionalities. The broader vision is to create a wide array of wild-type plants, capable of imaging objects in their environment, self powering themselves as light …
Read More »Dedicated Hardware for Quantum Machine Learning to usher new era in AI by exponential speedup of applications
Quantum computing and quantum information processing is expected to have immense impact by performing tasks too hard for even the most powerful conventional supercomputer and have a host of specific applications, from code-breaking and cyber security to medical diagnostics, big data analysis and logistics. One of the areas where …
Read More »Industry developing security solutions like Hardware security module (HSM) for secure military unmanned platforms, sensors, and communication devices
Hardware Trojans (HT), which are malicious circuit inclusions into the design from an adversary with an intention to damage the functionality of the chip at a much later date or leaking confidential information like keys used in cryptography. Time to market demand has forced integrated circuit design, manufacturing and testing …
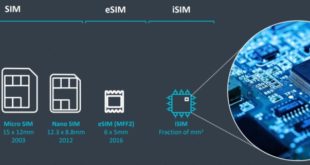
Read More »Embedded eSIM and iSIM are breakthrough IoT connectivity technologies for authenticating subscribers and devices on mobile networks
Strong IoT device authentication is required to ensure connected devices on the IoT can be trusted to be what they purport to be. Consequently, each IoT device needs a unique identity that can be authenticated when the device attempts to connect to a gateway or central server. With this unique …
Read More »Particle Robots and hybrid bio-inspired robotics are enabling shapeshifting space robots and autonomous robots for warfare
Recently scinetists are considering not only individual robots but developing of groups of robots, because a swarm of collaborative robots, each one observing the problem from a different point of view, is able to solve more difficult tasks than one robot by itself. The strength of a swarm can be …
Read More »Military Helicopters demand advanced engines with improved fuel consumption, power, durability and cost for conducting a wide range of military missions and operations.
A helicopter, or chopper, is a type of rotorcraft in which lift and thrust are supplied by rotors. This allows the helicopter to take off and land vertically, to hover, and to fly forward, backward, and laterally. These attributes allow helicopters to be used in congested or isolated areas where …
Read More »US Navy’s Autonomous surface vehicle, ACTUV developed to track quiet diesel-electric submarines, successfully navigated autonomously
China, Russia and North Korea are looking to develop their submarine fleets . Russia is seeking to further bolster its sub-surface capabilities, with new generations of conventional and nuclear propulsion submarines, which promise to be significantly more difficult to detect and track for western naval forces. This includes the Yasen, …
Read More »USS Gerald Ford, the Navy’s Most Powerful Aircraft Carrier Ever with enhanced power projection capability in anti-access/area denial (A2/AD) environment is nearing completion
In 2009, the U.S. Navy began construction of the first new type of aircraft carrier in nearly thirty-five years. The Navy refers to its newest aircraft carrier, the USS Gerald R. Ford, as “4.5 acres of sovereign U.S. territory. Gerald R. Ford is a class of supercarriers being built to …
Read More »Countries accelerating the transfer of military technology to commercial sector through accelerators and military-civilian integration
Many commercial technologies we use today can be traced to military from aircrafts to nuclear power, from semiconductors to computers. Duct tape was invented to protect ammunition cases from water during World War II. The internet grew out of a military research project. Navigation devices, such as Google Maps, rely on …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis