In an increasingly globalised and interconnected world it has become simple for people and goods to cross borders and so for terrorists. America’s borders and ports are busy places, with tens of millions of cargo containers and hundreds of millions of lawful travelers entering the country each year, while tens of thousands of illegal cargo entries and hundreds of thousands of unauthorized migrants are seized, arrested, or turned away.
At the same time, hundreds of thousands of unauthorized migrants evade detection to enter the United States illegally; thousands of kilograms of illegal drugs and other contraband are smuggled into the country; and tens of thousands of migrants may be victims of human trafficking. Ensuring effective border security is an integral part of any comprehensive and integrated national counter-terrorism strategy and requires collective action by States and relevant international and regional organizations. The threat stemming from foreign terrorist fighters (FTFs) has increased the pressure on Member States and the international community to strengthen border security and prevent FTF travel.
The United States confronts a wide array of threats at U.S. borders, ranging from terrorists who may have weapons of mass destruction, to transnational criminals smuggling drugs or counterfeit goods, to unauthorized migrants intending to live and work in the United States. In India long, porous and difficult borders have created the security challenges of illegal immigration, cross border terrorism, narcotics and arms smuggling, abetment of separatists and left -wing extremism and separatist movements aided by external powers. The task of border management become even more complicated due to geographical factors. There are mountains, swamps, rivers, deserts, forests, and variety of other geographical features which pose a challenge in front of security forces. Due to vulnerable borders, India has witnessed numerous cross-border terrorist attacks.
The rapid expansion of coronavirus disease 2019 (COVID-19) has been observed in many parts of the world has added another dimension to Border Security. The origin and spread of this pandemic has been fueled by travel. In December 2019, a novel coronavirus outbreak, COVID-19, caused by the severe acute respiratory syndrome coronavirus 2 (SARS-CoV-2), emerged in Wuhan, China, as a cluster of cases exhibiting pneumonia-like symptoms. Within a few weeks, the outbreak spread to 24 other countries around the world, including the United States, Canada, the United Kingdom, France, Australia, and Japan.
Many newly reported cases of COVID-19 during early outbreak phases have been associated with travel history from an epidemic region (identified as imported cases). During the outbreak emergence, one of the most urgent public health tasks is to prevent the spread of the virus from an epidemic source region to other regions within a country or globally. Because a person who was infected can travel to another region and spread the virus, COVID-19 continued to pose a severe threat to other regions through transportation services. Many newly reported cases of this new coronavirus infection in other cities or countries before community spread have been associated with travel history from an epidemic source region or contact history to people from the region, referred as the imported cases and the secondary cases transmitted from the imported cases respectively. Once the secondary cases continue to transmit to more local cases, infection chain is established in the community, community spread begins subsequently
To contain the global spread of the 2019 novel coronavirus epidemic (COVID-19), border control measures, such as airport screening and travel restrictions, have been implemented in several countries. Many countries and regions have imposed quarantines, entry bans, or other restrictions for citizens of or recent travelers to the most affected areas. Other countries and regions have imposed global restrictions that apply to all foreign countries and territories, or prevent their own citizens from travelling overseas. A study in Science found that travel restrictions had only modest effects, delaying the initial spread of COVID-19, unless combined with infection prevention and control measures to considerably reduce transmissions. Researchers came to the conclusion that “travel restrictions are most useful in the early and late phase of an epidemic” and “restrictions of travel from Wuhan unfortunately came too late”
Effective border security is the first line of defence against the movement of terrorists across borders and the illegal cross-border movement of goods and cargo. Maintaining secure maritime, land, and air borders is challenging for many Member States. Spaces between official border crossings are difficult to control because they are often lengthy and consist of open spaces or difficult terrain. They therefore present risks and vulnerabilities for potential crossing by terrorists. . Other challenges derive from the lack of financial and human resources, equipment and specialist skills, or the lack of intra-State and interState cooperation also continues to increase States’ vulnerabilities.
Coordinated border management (CBM) strategies, which require close coordination among the competent authorities at border locations, have proven to be a highly effective tool for efficiently and effectively managing national borders. CBM strategies provide for coordination of policies, programmes, and delivery among cross-border regulatory agencies with the aim of strengthening the management of trade and travel flows, while also addressing security concerns.
Mr G Kishan Reddy, Minister of State for Home Affairs, Govt of India, called for integrating new technology and infrastructure to ensure a safe and smart border management system. Speaking at ‘Smart Border Management – 2019’ organized by FICCI, Mr Reddy said that the government has, for the first time, initiated a Comprehensive Integrated Border Management System (CIBMS) to cover areas where physical fencing is not feasible. “The recorded date and information can be shared with all intelligence and security forces,” said Mr Reddy. “CIBMS includes integration of manpower, sensors, networks, intelligence, and command and control solutions to improve situational awareness at different levels of hierarchy to facilitate prompt and informed decisions and a quick response to emerging situations,” added Mr Reddy.
US DHS Risk Management
Department of Homeland Security’s (DHS’s) complex border security mission, calls on the agency to “prevent the illegal flow of people and goods across U.S. air, land, and sea borders while expediting the safe flow of lawful travel and commerce; ensure security and resilience of global movement systems; [and] disrupt and dismantle transnational organizations that engage in smuggling and trafficking across the U.S. border.
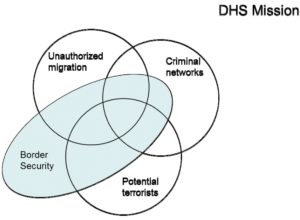
Source: CRS Analysis.
Thus, DHS’s border security responsibilities were defined by the Homeland Security Act (HSA, P.L. 107-296) to include, among other responsibilities, preventing the entry of terrorists and terrorist weapons; securing U.S. borders, territorial waters, ports, and transportation systems; immigration enforcement; and customs enforcement (including preventing the entry of illegal drugs). While DHS combats illegal migration, criminal networks, and potential terrorists at U.S. borders, its work on all three of these issues also extends beyond the border, both within the United States and through international partnerships.
In general, border threats may be divided into actors and goods. Threat actors include potential terrorists, transnational criminals, and unauthorized migrants , among other types of people whose entry into the United States may produce harmful consequences.
Threatening goods include weapons of mass destruction (WMD) and certain other weapons, illegal drugs and other contraband, counterfeit products, and products brought into the United States illegally and/or with potentially harmful effect.
A defining feature of terrorists, is that terrorists are motivated by particular grievances about aspects of the societies that surround them, and adopt extremist ideologies or narratives. Specific terrorist activities, include the hijacking or sabotage of any conveyance, the seizure or threatened violence against another individual in order to compel a third person or governmental organization to do or abstain from an activity, violence against an internationally protected person, assassination, and the use of a weapon of mass destruction or other dangerous device other than for personal monetary gain. In contrast with terrorists, criminals generally are non-ideological, and fundamentally motivated by the pursuit of profit. Unauthorized migrants—like legal migrants—may be motivated by some combination of employment opportunities, a general desire to improve their economic circumstances, family connections, and dangerous or difficult conditions in their home countries, among other factors.
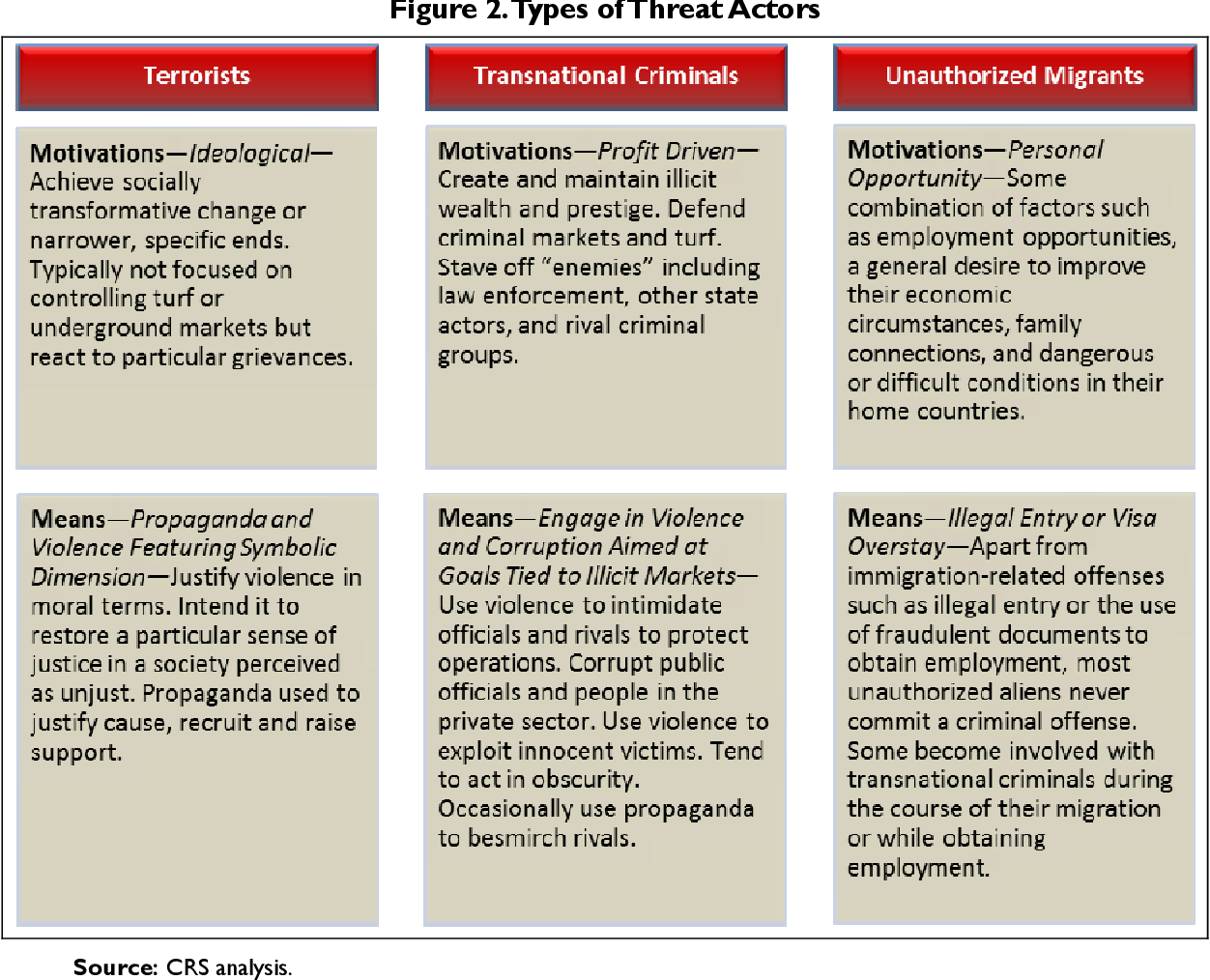
Any good that is smuggled into or out of the United States is illegal and may pose security risks. Illegal goods fall into two broad categories distinguished by their inherent illegitimacy: certain weapons, illegal drugs, and counterfeit goods are always illegal and categorically prohibited, while other goods are generally legal, but become illegitimate because they are smuggled to avoid the enforcement of specific laws, taxes, or regulations.
U.S. law enforcement seeks to prevent a variety of illegal goods from entering the United States. WMD may come in many forms, and the term often covers chemical, biological, radiological, nuclear, and explosive (CBRNE) weapons.
In addition to the smuggling of weapons into the United States, there are also border security and national security concerns over the smuggling of weapons out of the United States. One such concern involves Mexican drug trafficking organizations purchasing firearms in the United States and smuggling these weapons to Mexico, where their possession by civilians is largely prohibited. Firearms smuggled from the United States into Mexico have been cited as helping to fuel the drug trafficking-related violence in Mexico.
The smuggling of counterfeit and pirated goods into the United States—particularly by transnational criminal organizations—has also been identified as a threat to border security. This smuggling violates intellectual property rights (IPR) and “threaten[s] America’s economic vitality and national security, and the American people’s health and safety.
In general, DHS’s border enforcement strategy, like its overall approach to homeland security, is based on risk management, which DHS defines as “the process for identifying, analyzing, and communicating risk and accepting, avoiding, transferring, or controlling it to an acceptable level considering associated costs and benefits of any actions taken.” In short, the goal of risk management is to target enforcement resources to specific threats in proportion (1) to the gravity of the associated risk, and (2) to the cost-effectiveness of the enforcement response.
Risk management—like almost any process for responding to external threats—involves developing a model of risk assessment. The
standard components of many risk models include estimates of the likelihood of a threat (or other adverse event) and the potential
consequence of the threat. Risk models based on likelihood and consequences describe risk as a positive function of these two
components, so that risk increases with the likelihood and potential consequences associated with a given threat. Put another way, this model of risk may be understood as “the statistical expect[ed] value of an unwanted event that may or may not occur.
Any given border threat may result in a range of potential consequences, DHS identifies six broad categories of potential consequences: loss of life, injuries and illness, direct economic costs, social displacement, psychological distress, and environmental impact.
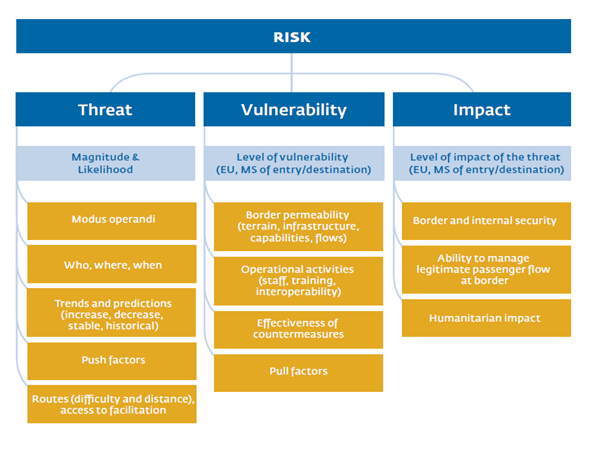
Common Integrated Risk Analysis Model (CIRAM)
According to the model, a ‘threat’ is a force or pressure acting upon the external borders that is characterised by both its magnitude and likelihood; ‘vulnerability’ is defined as the capacity of a system to mitigate the threat; and ‘impact’ is determined as the potential consequences of the threat. In this way, a structured and systematic breakdown of risk provides for an assessment of the relative overall risks posed by different threats as a function of the relevant vulnerabilities and impacts, and therefore will be of much use to decision-makers in setting priorities, in formulating counter-measures and in designating operational targets.
Measures and Technology
States had taken steps to strengthen border security and prevent FTF travel. Those steps include passport confiscation, the introduction of a requirement for transit visas, and more effective use of the databases of the International Criminal Police Organization (INTERPOL) to screen for potential FTFs. Some States, for example, have connected their immigration-screening processes at the frontline to the INTERPOL database on stolen and lost travel documents, and more States are populating the INTERPOL list of FTFs, says UN Counter-Terrorism Committee .
Important tools in enhancing border security are Advance Passenger Information (API) and Passenger Name Records (PNR). In its simplest form, API is an electronic communications system that collects biographical passenger data and basic flight details from airline carriers and transmits the data to border-security authorities in the destination country prior to the flight’s arrival. Tis gives border-security authorities additional time to perform enough checks of all in-bound passengers against relevant sanctions and watch lists while minimizing delays in the processing of inbound passengers.
PNR are generated through the information provided by passengers as they book their airline tickets and check into their flights. This
Information is held in the carrier’s reservation and departure control systems, and may include a broad range of information,
including the passenger’s name, his/her travel dates, ticket information, contact details, name of travel agent, means of payment, seat number, and baggage information. Many States already use PNR for law enforcement and border control purposes, whether on the basis of specific legislation or general legal and administrative powers, including to combat crossborder crime.
Further ways to prevent the movement of terrorists or terrorist groups include strengthening control of the issuance of identity papers and travel documents and the introduction of measures to prevent counterfeiting, forgery, or fraudulent use of identity papers and travel documents. However, many States lack clear policies and measures to ensure the security and integrity of the identity and travel-document issuance process, and many have not yet put in place security measures at airports and other border crossings designed to ensure the effective screening of travellers, says Counter-Terrorism Committee.
Biometric identification is an effective tool for countering the threat posed by suspected terrorists including FTFs who attempt to travel internationally and use falsified travel documents. In the context of a terrorism-related investigation, forensic science can assist investigators and prosecutors by linking an individual to a specific activity, event, place, or material, or to another individual.
UK Government’s 2025 border vision realized through technology
UK government’s ambition is to have a “world-leading” border by 2025. The 2025 border vision centres on the transformation of processes, systems and infrastructure – using new technologies to empower these changes and deliver enhanced border security and efficiency, alongside economic prosperity and an improved user experience.
“Technology-enabled automation and data analytics,” notes Emma Churchill, director-general of the Border and Protocol Delivery Group at the Cabinet Office, “have the potential to revolutionise how the UK border operates.” The goal, she suggests, is to create a frictionless, smart and intelligence-driven border. “We have established the Border Operations Centre, which uses state of the art technology to monitor the UK border in real time. This new asset will give us access to more intelligence in one place than ever before, enabling us to quickly tackle any issues that arise.”
The Trade Bill, introduced into parliament as a key element of the UK’s future trade policy, supports the change needed to enable this. The planned £705m overhaul of UK border systems will undoubtedly generate even more data. As government departments and industry bodies are able to collect, collate and interpret data in unprecedented ways, greater value can be harnessed from previously siloed data sets.
The creation of a single technological ecosystem where data seamlessly flows between trusted stakeholders will transform the way we identify security and public health risks, dangerous and contraband cargo, and supply chain integrity and availability. Technology can remove the need for people to input the same information more than once. As Dr Peter William Walsh, a researcher at the Migration Observatory at the University of Oxford, explains, technology may be used “to improve the effectiveness of the immigration system with faster processing of applications and a lower burden of administrative work for applicants, whose digital lives can be tapped into more easily to provide proof of their work, health, family and study histories”. The same benefits can be realised for traders.
At present, the UK’s border management systems operate almost independently, on legacy software. Using innovative approaches to modernise systems and create an open and secure, integrated, digital architecture will enable information sources to be pulled together, and data used to deliver reliable, intelligence-led targeting and data visibility. This reduces duplication and improves security through risk-based profiling – enabling proactive action rather than waiting for problems to occur.
This includes, for instance, maturing processes and methods for collecting and collating advanced passenger information to reduce pressure on border agencies; real-time transport information, such as news about traffic or road closures to help to manage the flow of trade; while automation can help to free up resources. This enables an understanding of greater volumes of data. So, in practical terms, what does that really mean? Making sure the right data is collected and processed in a timely manner means that resources can be in the right place at the right time, ensuring goods and people flow, and bad actors arrested.
Leidos, equipped with over 50 years of experience in defence, security and engineering, has developed a range of technologies to assist with the UK’s border needs, from prediction through to resolution. Leidos has developed cargo scanners, operational systems that blend data from multiple sensory inputs, surveillance technology, and biometric devices.
It is important to note that no single product is a panacea for the challenges of UK border management. A collaborative approach between government and industry, recognising what can be leveraged from current infrastructure and what approaches can deliver transformation and end-user benefits without the need for massive refactoring, is critical.
Ultimately, digital transformation can help the UK border to enjoy the benefits of internationalism while mitigating the risk factors it needs to operate more diligently. In the future, the UK border needs to be more mobile and responsive, especially in the event of another crisis. An effective border, enabled and empowered by a technological ecosystem, can form the basis of a thriving and progressive economy, writes Al Potter, managing director and vice-president for national security and defence at Leidos UK.
References and Resources also include
https://www.newstatesman.com/2021/01/future-borders
https://fas.org/sgp/crs/homesec/R42969.pdf
 International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis
