One of the major objectives of the military is to achieve high reliability and operational availability of their assets. Significant operational benefits are to be gained by employing highly reliable military assets. The major reasons why achieving high reliability is so important are: (1) maintaining weapons systems consumes a significant …
Read More »TimeLine Layout
February, 2021
-
24 February
Cellulose nanopaper promising for green electronics, green vehicles, energy harvesting and optical sensing
In recent years, nanomaterials have displayed potential in effective detection and removal of greenhouse gases, chemical contaminants, organic pollutants, and biological agents. These materials come in various morphologies and have various functions (e.g., adsorbents, catalysts, or membranes). The high reactivity and high surface area of nanomaterials are some of the …
Read More » -
21 February
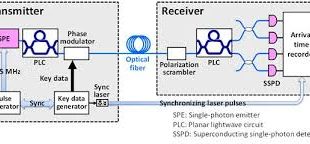
Graphene enables room temperature single photon emitter and detector for unhackable Quantum Key Cryptography (QKD)
Quantum Key Distribution, or QKD, enables two remote parties, “Alice” and “Bob”, who are connected by a passive optical link to securely generate secret key material. Single-photon sources (SPSs) and single-photon detectors (SPDs) are key devices for enabling practical quantum key distributions (QKDs). Single photon generation is necessary for secure quantum transmission; …
Read More » -
21 February
US, Israel and India require new Tunnel Detection and neutralization technologies to stop drug and weapon smuggling, human trafficking, and cross border terrorism
Criminals, terrorists and military have been using tunnels since long time to evade detection as surface based detection methods are ineffective underground . Indian Border Security Force (BSF) troopers in Nov 2020 discovered an underground tunnel on the international border at Regal area in J&K`s Samba district, officials said. As …
Read More » -
21 February
Airborne wind energy (AWE) is future emerging technology in the wind power sector
Renewable energy is at the centre of the transition to a less carbon-intensive and more sustainable energy system. Renewables have grown rapidly in recent years, accompanied by sharp cost reductions for solar photovoltaics and wind power in particular. The future development of wind power presents a significant opportunity in terms …
Read More » -
20 February
Optical Circulators are building blocks for chips for optical communication networks and quantum computers
Fiber optical circulators are used to separate optical signals that travel in opposite directions in an optic fiber in order to complete bidirectional transmission. Optical circulators are also known as non-reciprocal optics, which means when the light travels in the opposite direction, changes in the light properties are not reversed. …
Read More » -
18 February
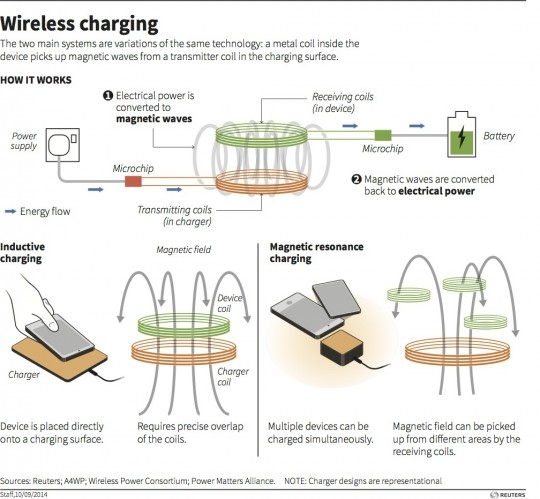
Wireless Power Transfer(WPT) set to complete the transition to Wireless life for Consumers and Military, Countries trialling WPT for electric vehicles
Electronics has revolutionized our society by providing many devices e.g. laptops, palm pilots, digital cameras, household robots, etc. Every electronic system or device needs electric power to operate, whether it is from walled AC supply or a battery. This electric power cannot be stored infinitely in any rechargeable device like …
Read More » -
18 February
DSO’s Make-It program on Synthetic chemistry enables end-to-end automated production of pharmaceuticals and other chemicals
Chemists who are trained in synthesis use their skills to create new forms of matter. They synthesize compounds not just because they are new: the design and preparation of these new compounds leads to numerous applications in pharmaceuticals, materials, detection, energy utilization and storage, and insights into biological systems. Synthesis …
Read More » -
17 February
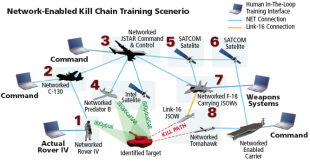
After initial Hype and amid Cyber Warfare threat, Network Centric Warfare approach is now being adopted realistically in various Militaries
As the 21st Century battlefield becomes increasingly complex and asymmetrical, military forces are striving to harness network technology to gain an operational advantage, by transforming traditional linear command structures and linking sensors, unmanned vehicles, command posts and ground troops to achieve decision superiority for full spectrum dominance. Network Centric …
Read More » -
16 February
DARPA DSO’s Disruptioneering accelerating innovation of most radical and potentially highest-payoff ideas for currently fielded platforms and building new capabilities for future systems.
DARPA’s Defense Sciences Office (DSO)—whose mission is to identify and pursue high-risk, high-payoff research initiatives across a broad spectrum of science and engineering disciplines—launched Disruptioneering in Spring 2017 which pushes for faster identification and exploration of bold and risky ideas with the goal of accelerating scientific discovery. The goal of …
Read More »
 International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis