“Oceans cover more than 70 percent of the earth’s surface, but we know very little …
Read More »Masonry Layout
DARPA call for innovative mission system concepts and Breakthrough Technologies for peer adversaries
The Defense Advanced Research Projects Agency’s (DARPA) Strategic Technology Office (STO) DARPA has released a …
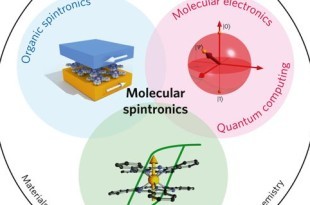
Read More »Molecular spintronics is emerging field of nanoscale electronics that uses molecules to build ultrafast, low power electronics devices
The age of electrically-based devices has been with us for more than six decades. With …
Read More »Co-operative Perception (CP) for Intelligent Transportation Systems (ITS)
Autonomous vehicles (AVs) have received extensive attention in recent years as a rapidly emerging and …
Read More »Urban Warfare and urban terrorism are the greatest future security threat, require new tactics and technologies being developed and tested
Cities have become the new battleground and Hybrid or Urban Warfare the greatest threat being …
Read More »Software modem
Conventional modem designs can be termed as ‘fixed-function’ modems ‘ because almost all modem functionality …
Read More »Metamaterial based Antennas for wireless and space communications, GPS, satellites, airplanes and missile seekers
Wireless electronic systems have been relying on dish antennas to send and receive signals. These …
Read More »DARPA EXTREME devloped engineered optical materials or metamaterials now transitioning from NGA to AFRL UAS and Unmanned combat aerial vehicles (UCAV)
Optics & Electro-Optics areas through areas like Day vision, Night Vision, Thermal Imaging are playing …
Read More »Satellite Network Management systems (NMS) are evolving to meet commercial and military requirements
Satellite communications represent a cost effective and reliable means of transporting voice, video and data …
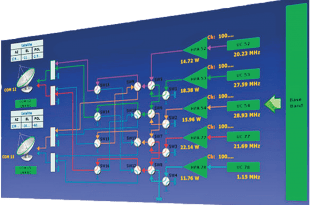
Read More »FAST , TIA 5041 OSDI for all digital SATCOM terminal for Miltary
Historically, the evolution of the modem technology has been exclusively focused on purpose-built solutions with …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis