Nerve agents, a class of synthetic phosphorous-containing compounds, are among the most toxic substances known. Brief exposure to the most potent variants can lead to death within minutes. Once nerve agents enter the body, they irreversibly inhibit a vitally important enzyme called acetylcholinesterase. Its normal job within the nervous system …
Read More »New technologies to aid Ocean search and rescue operations
Search and rescue (SAR) is the search for and provision of aid to people who are in distress or imminent danger. The general field of search and rescue includes many specialty sub-fields, typically determined by the type of terrain the search is conducted over. These include mountain rescue; ground search …
Read More »Covid-19 is accelerating the transition to smart and safe cities with technology to build resilience
Cities are powerful engines of economic growth, , more than half of the world’s population lives in an urban area or city and it is estimated 70 per cent of the world’s population will live in cities by 2050. Urbanization’s advantages are however mirrored by significant sustainability challenges, with cities …
Read More »Changing nature Of Irregular Warfare require new capabilites and technologies
Traditional warfare is characterized as “a violent struggle for domination between nation-states or coalitions and alliances of nation-states. ” This confrontation typically involves force-on-force military operations in which adversaries employ a variety of conventional military capabilities against each other in the air, land, maritime, space, and cyberspace domains. The objective …
Read More »DARPA SIGMA deployed city wide Internet of Things (IoT) network to provide real time situational awareness of CBRNE threats
Since the invention of nuclear power, there have been numerous “accidents.” From Three Mile Island and Chernobyl to the more recent problems in Fukushima, it would seem nuclear power is not fully under our control. Recently a Chinese scientist has warned that the single mountain under which North Korea most …
Read More »Unmanned Aerial Systems emerging promising alternative for IEDs and Landmine detection and Disruptionr
Several countries suffer from the existence of millions of buried landmines in their territories. These landmines have indefinite life, and may still cause horrific personal injuries and economic dislocation for decades after a war has finished. Landmines, improvised explosive devices (IEDs), and other homemade bombs struck 6,461 people worldwide …
Read More »Maritime terrorism require Unattended Sensor Technologies for Monitoring Riverine and Littoral Zone Vessel Traffic
Terrorist groups and transnational criminal organizations continue to illegally cross porous land borders to traffic small arms and light weapons (SALW), ammunition and explosives, drugs, contraband, other illicit goods, and human beings, as well as deploy terrorist operatives to conduct attacks. Such activities undermine States’ efforts to counter terrorism and …
Read More »Global threat of landmines and IED require new IED neutralization technologies
IED’s have become an extremely significant and dangerous force protection issue in the wake of Operation Iraqi Freedom (OIF) and the Global War on Terror (GWOT). Insurgents and terrorists are using a variety of asymmetric techniques to attack militarily superior coalition forces with military ordnance components combined with commercial off …
Read More »New detection technologies tracking terrorists through thick concrete, underground tunnels, and caves
In April 2017, the U.S. military dropped the most powerful non-nuclear bomb ever used in combat on a tunnel complex in Afghanistan’s Nangarhar province. The airstrike targeted the Islamic State’s Khorasan branch. The use of the GBU-43/B Massive Ordnance Air Blast weapon, the so-called “Mother of All Bombs,” highlighted the …
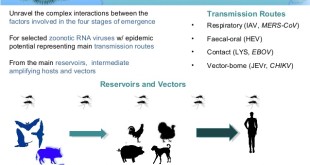
Read More »DARPA’s PREEMPT to predict next pandemic due to Zoonotic Viruses like COVID-19 and plan proactive interventions
In recent weeks, concern over the emergence of a novel coronavirus in China has grown exponentially as media, experts and government officials around the world have openly worried that this new disease has the potential to develop into a global pandemic. As the ongoing coronavirus outbreak centered in China has spread …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis