The World Trade Center events of September 11, 2001, focused the world’s attention on high-rise buildings. Since that time, there have been several other events that have kept the world’s attention on high-rise building fire safety, including fires in Madrid, Venezuela, and two in Chicago. The two deadliest high-rise fires …
Read More »France thrust on counter terrorism initiatives after glaring security gaps exposed by brazen attacks
France suffered a series of deadly terror attacks in November 2015. In 2015, the brazen murders of 17 innocent people, in three separate attacks in as many days, have revealed serious breaches and lapses in the French system of intelligence, surveillance and security, according to numerous counterterrorism experts. In July …
Read More »Changing role of Military Scientific and Technical Intelligence ( S&TI)
If the Militaries are to fight and win in future wars, it must thoroughly understand the challenges that it will face and how those challenges will impact the way it intends to fight. It must act now to ensure that it possesses a technological edge over its adversaries. This is …
Read More »IARPA pursues anticipatory intelligence to predict the unpredictable , Video to open source collection & analysis to Quantum amd Exascale computing
The Intelligence Advanced Research Projects Activity (IARPA) is an organization within the Office of the Director of National Intelligence that funds high-risk, high-payoff research to overcome difficult challenges relevant to the United States Intelligence Community. IARPA was given the mandate to conduct cross-community research, target new opportunities and innovations, and …
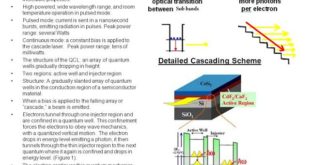
Read More »New efficient, high brightness, and tunable Quantum cascade laser (QCL)s technologes from mid-wave infrared (MWIR) to Terahertz region promise chemical warfare agents & hidden explosives detectors, to infrared countermeasure (IRCM) systems
Compact, chip-based lasers have conquered much of the electromagnetic spectrum, from ultraviolet to infrared, enabling technologies from digital communications and barcode readers to laser pointers and printers. Diode lasers depend on the process of electron-hole recombination: an electron from the conduction band recombines with a hole in the valence band, …
Read More »Indian Threat Scenario, National security threats and future military capability requirements
There are two approaches to connect Warfighting and emerging technologies. One is to consider the present and future threat environment and then through system analysis we can identify technologies required to mitigate those threats. Secondly, we can identify the emerging technologies that can offer new military capability. Coming to …
Read More »Remerging threat of Biological Weapons attack against Agricultural Targets and Agrobioterrorism, with advances in Gene editing, synthetic biology, and improved delivery systems
Food and agriculture are key elements of the critical infrastructure of every country because they provide products that are essential for life. The United States is a country with a highly developed agricultural sector. Food and agriculture constitute a sixth of the U.S. gross domestic product, totaling more than a …
Read More »Smart Home Security Threats , countermeasures and Technology solutions and their Market growth
FBI has reported recent crime data: 7.9 million property crimes were committed in the nation in 2015. Property crimes resulted in losses estimated at $14.3 billion in 2015. Property crime rates have steadily declined over the last ten years. In 2005, 10.1 million property crimes were committed. In 2015, that …
Read More »Synthetic Biology has enhanced asymmetric Bio warfare and Bio terrorism threat posed by biological weapons, in response US launches Biodefence Strategy
The COVID-19 pandemic has demonstrated that significant biological threats can and will emerge from nature without warning, demonstrating that a single viral strain can have a profound impact on modern society. It has also demonstrated that infectious diseases can rapidly spread throughout a population without human engineering making them the …
Read More »Rising security threats to Smart homes their security requirements and measures for protection
A smart home refers to a convenient home setup where appliances and devices can be automatically controlled remotely from anywhere with an internet connection using a mobile or other networked device. Devices in a smart home are interconnected through the internet, allowing the user to control functions such as security …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis