Introduction In an ever-changing world, security concerns have become paramount, with terrorism posing a significant threat to global stability and peace. To safeguard our future, we must adopt proactive measures to prevent acts of terror rather than simply reacting to their consequences. Early warning systems and advanced technologies have emerged …
Read More »Connecting When It Matters Most: Emergency Satellite Services and Disaster Relief
Introduction: In times of natural disasters and humanitarian crises, connecting with affected communities and coordinating relief efforts is critical for saving lives and minimizing damages. However, traditional communication infrastructure often fails or becomes overwhelmed during these emergencies, leaving communities isolated and responders struggling to assess the situation. In such dire …
Read More »The Next Frontier in Encryption: Homomorphic Encryption the Future of Secure Computation
Businesses, large and small, are embracing the Cloud. No matter which research company, vendor or expert you consult, everyone agrees that about four in every five enterprise workloads are either already in the Cloud or will be within the next few months. That means the best-practice security strategy you established …
Read More »Unleashing the Power of Drones: The Exponential Growth of the Global UAVs Market across Civil, Commercial, Military, and Security Sectors
Introduction Unmanned Aerial Vehicles (UAVs), commonly known as drones, have revolutionized the aerospace industry. These aircraft, without a human pilot on board, have become integral components of unmanned aircraft systems (UAS), which encompass a UAV, a ground-based controller, and a communication system between the two. Initially designed for missions deemed …
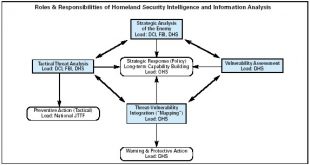
Read More »Harnessing Artificial Intelligence and Data Analytics to Combat Terrorism on Social Media: Promoting Cross-Platform and Transnational Cooperation
In today’s digital age, social media platforms have become powerful tools for communication, information sharing, and social interaction. However, they have also become breeding grounds for extremist ideologies and terrorist propaganda. To counter this alarming trend, the integration of Artificial Intelligence (AI) and data analytics is emerging as a promising …
Read More »Protecting National Security: The Growing Market for Border Security Systems
Introduction: In an era of evolving global threats, safeguarding national security has become a top priority for governments around the world. As countries face challenges such as terrorism, transnational crime, smuggling, and illegal migration, the need for robust border security systems has become increasingly critical. This blog article explores the …
Read More »India’s Smart and Comprehensive Integrated Border Management (CIBMS) to guard its long, difficult and porous borders
The long, porous and difficult borders have created the security challenges of illegal immigration, cross border terrorism, narcotics and arms smuggling, abetment of separatists and left -wing extremism and separatist movements aided by external powers. Pakistan policy of supporting cross border terrorism has led to constant border skirmishes along the …
Read More »Rising Open Source Intelligence (OSINT) importance for Military
Intelligence, in military science, information concerning an enemy or an area. The term is also used for an agency that gathers such information. Military intelligence is as old as warfare itself. Even in biblical times, Moses sent spies to live with the Canaanites in order to learn about their ways and …
Read More »Armed Crop Dusters for Security and Military Missions
A crop duster, is usually, an aircraft used for dusting or spraying large acreages with pesticides. Aerial spraying and dusting permit prompt coverage of large areas at the moment when the application of pesticide is most effective and avoid the need for wheeled vehicles that might damage crops. Agricultural …
Read More »China controls internet to curb dissent , employs widespread surveillance for ‘anti-terror’ measures and for repression of people
With President Xi Jinping at the helm, the Chinese government doubled down on repression inside and outside the country in 2021, says world report 2022 on human rights. Its “zero-tolerance” policy towards Covid-19 strengthened the authorities’ hand, as they imposed harsh policies in the name of public health. Beijing’s …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis