Black hat hackers are responsible for writing malware, which is a method used to gain access to these systems. They usually have extensive knowledge about breaking into computer networks and bypassing security protocols. Their primary motivation is usually for personal or financial gain, but they can also be involved in …
Read More »Vulnerabilities in 3D printing could be exploited for Cyber-Physical attacks and Cyber Warfare
3D printing or additive manufacturing is ongoing revolution in manufacturing with its potential to fabricate any complex object and is being utilized from aerospace components to human organs, textiles, metals, buildings and even food. Additive manufacturing, is defined by ASTM International as the process of joining materials together, layer by …
Read More »Future Blended Physical-Cyber Attack shall use multiple attack vectors to cause the mayhem, report anticipates 2M Fatalities
Governments, military forces and critical national infrastructure organisations typically deal with some of the most sophisticated cyber threats in use today. These cyber threats continue to grow in sophistication and automation, with attackers ranging from highly skilled and motivated organisations, including nation states, or individuals to less skilled attackers using …
Read More »Cyber Red teaming or penetration testing uncovers the vulnerabilities of an organisation, NEC develops automated tool
Cyberattacks are being conducted daily on any type of target, and any notion that a state of full cyber security can be reached is a mere illusion. Cybersecurity is about managing risks and to ascertain that, to a certain extent, proper procedures and adequate security measures are being taken. Exposed …
Read More »DARPA’s CHASE to automate cybersecurity across the large, distributed Department of Defense, Enterprise Network
Secure networks are vital to U.S. military operations at all levels and are a source of tactical, operational and strategic advantages. They provide the capability to acquire, move and process massive amounts of information, make decisions rapidly and command distributed forces on an unparalleled scale. However, Networks within the …
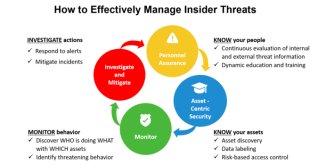
Read More »Across all companies insider Cyber threats are on the rise, New breakthrough technologies being developed to combat them
CERT Insider Threat Center, a research arm of Carnegie Mellon University’s Software Engineering Institute (SEI). They have defined an insider threat as: …the potential for individuals who have or had authorized access to an organization’s assets to use their access, either maliciously or unintentionally, to act in a way that could …
Read More »USAF develops Joint cyber operations platform for the execution of full-spectrum cyberspace operations from the operational through tactical levels of warfare
Developing and delivering air superiority for the highly contested environment in 2030 requires a multi-domain focus on capabilities and capacity, according to the unclassified version of the Air Superiority 2030 Flight Plan. “After 25 years of being the only great power out there, we’re returning to a world of great …
Read More »DARPA MRC developed resilient cloud services that would continue to operate and support military objectives despite being hit by a cyberattack
Cloud computing has burst recently into technology and business scene promising great technical and economic advantages, like offering On-demand provisioning of computer services, improved flexibility and scalability as well as reducing costs. Another attractive point of the cloud is its ability to enable a mobile workforce, which brings enhanced flexibility …
Read More »U.S., Britain blame Russia for global cyber attack targeting Network Infrastructure Devices
The United States and Britain in 2018 accused Russia of launching cyber attacks on computer routers, firewalls and other networking equipment used by government agencies, businesses and critical infrastructure operators around the globe. Network infrastructure consists of interconnected devices designed to transport communications needed for data, applications, services, and multi-media. Routers …
Read More »DARPA’s Transparent Computing programme for defeating complex, sophisticated and stealthy long-term Advanced Persistent Threats ( APTs)
Modern computing systems are essentially black boxes that accept inputs and generate outputs, but provide little-to-no visibility of their inner workings, according to DARPA. It can therefore be extremely challenging to detect an intruder, particularly an ‘Advanced Persistent Threat’: a form of attack in which the adversary slowly and deliberately …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis