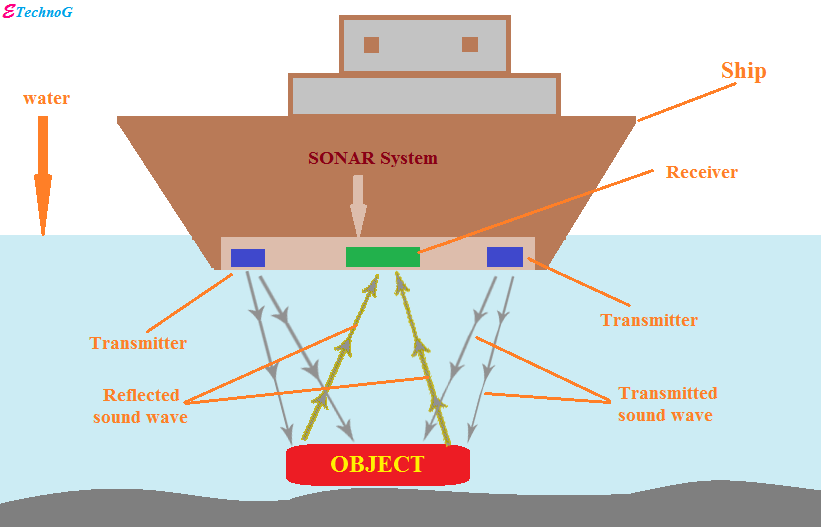
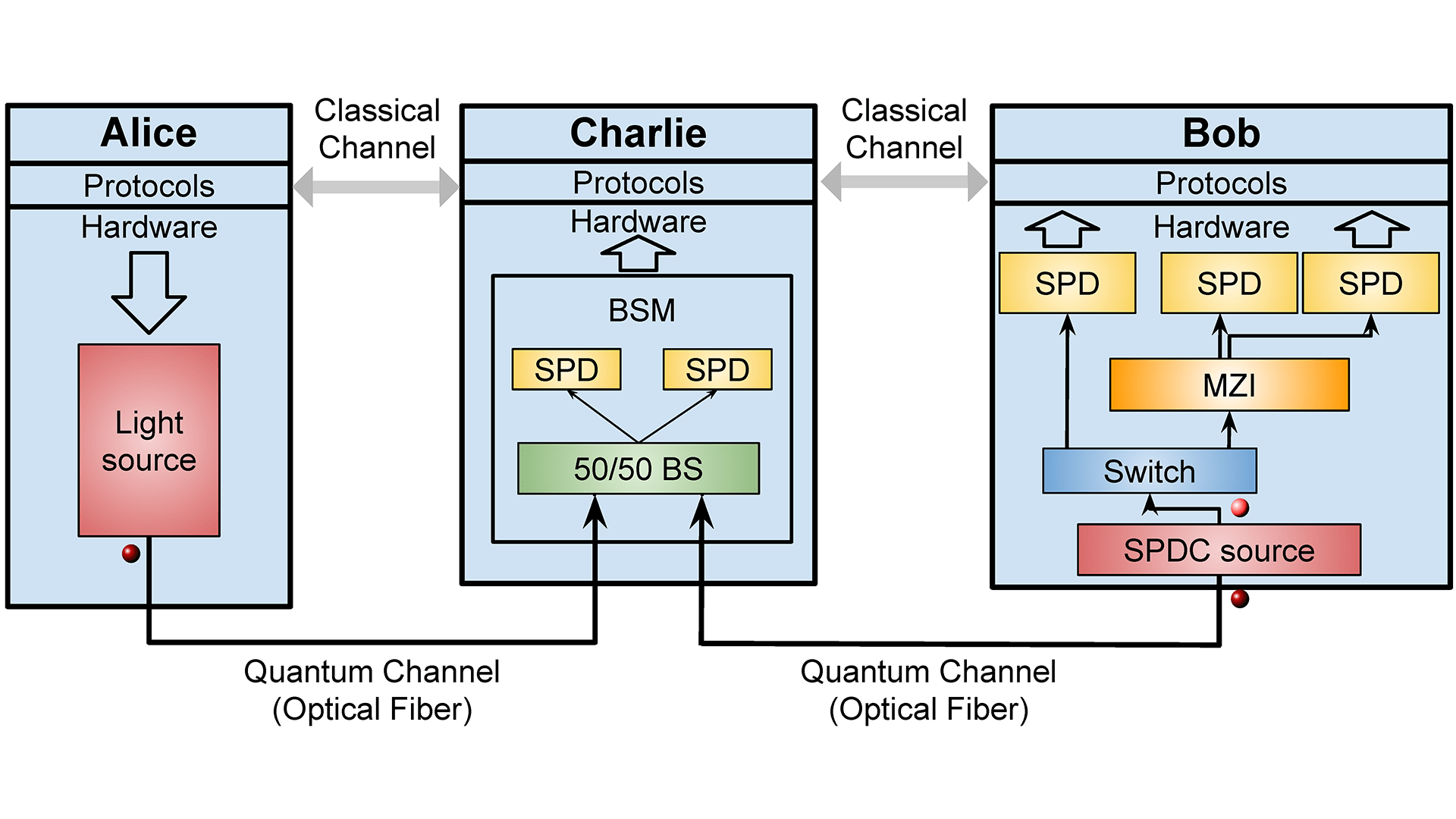
Hypergolic propellant

A rocket is defined as a technologically advanced reaction motor that can carry its oxidant to propel a launch vehicle. A reaction motor is used as a propulsion device to generate a forward push by expelling the rocket structure in…...