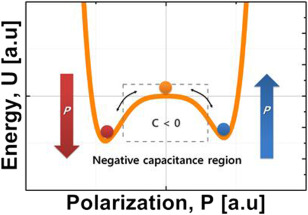
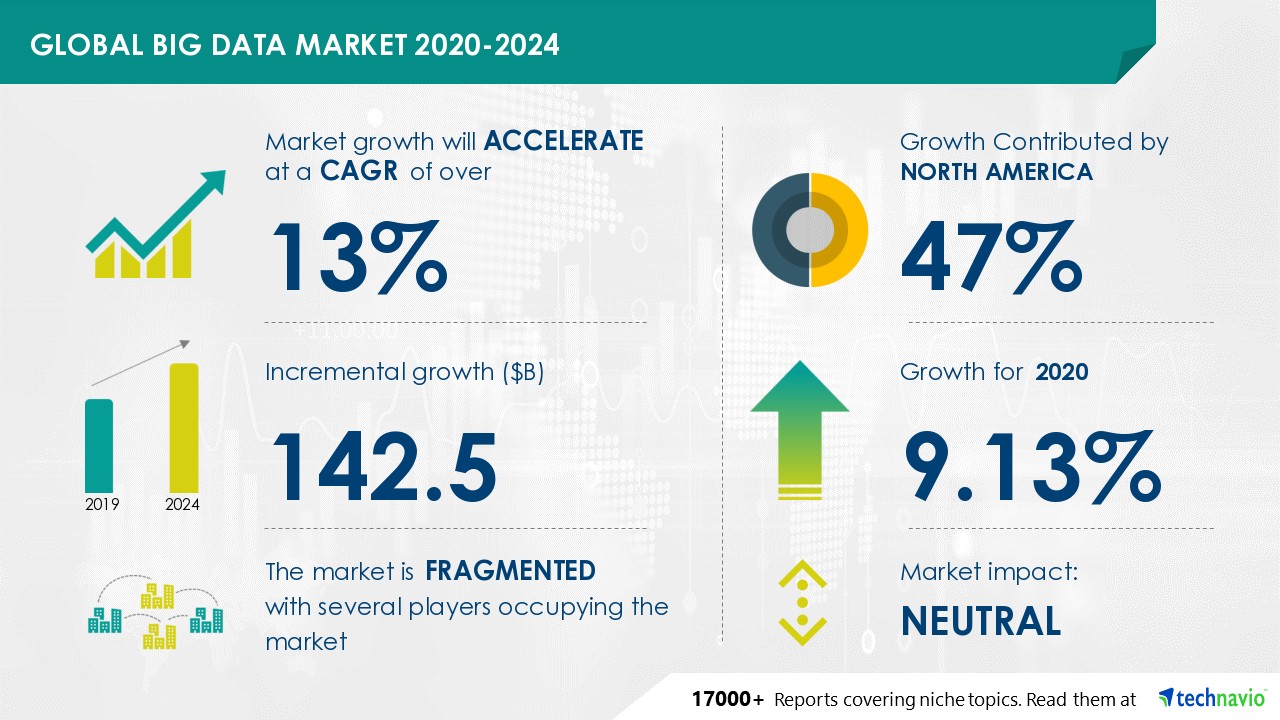
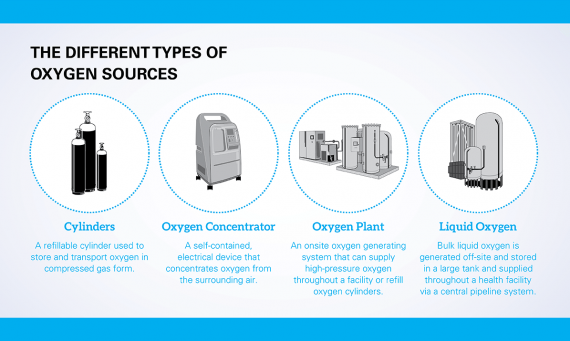
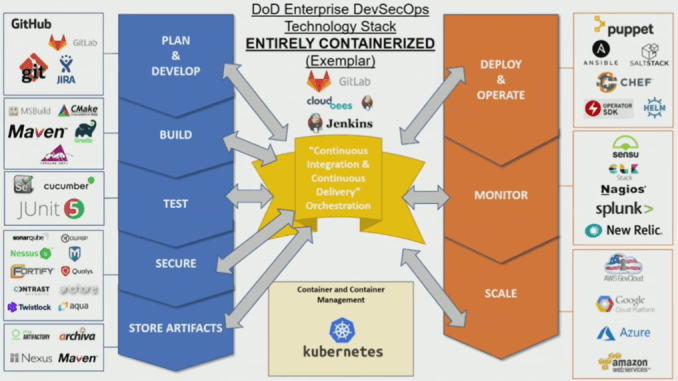
DARPA RACER-Sim will employ simulation tools to accelerate development of military autonomous ground vehicles for the battlefield

Modelling is the process of representing a model (e.g., physical, mathematical, or logical representation of a system, entity, phenomenon, or process) which includes its construction and working. This model is similar to a real system, which helps the analyst predict…...