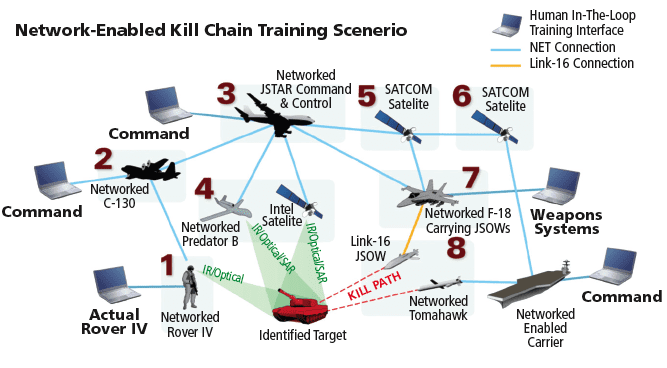
As the 21st Century battlefield becomes increasingly complex and asymmetrical, military forces are striving to harness network technology to gain an operational advantage, by transforming traditional linear command structures and linking sensors, unmanned vehicles, command posts and ground troops to achieve decision superiority for full spectrum dominance.
IDST Pro Access Required
This analysis is part of IDST premium intelligence.
Subscribe to Continue ReadingAlready a member? Log in