The accelerating pace of digitalisation, fuelled by the COVID-19 pandemic, has led to a record-breaking year for cybercrime with ransomware attacks rising 151 per cent in 2021, and an average of 270 cyberattacks per organisation being faced, a new study showed in Jan 2022.
The World Economic Forum’s ‘Global Cybersecurity Outlook 2022’, released during its online Davos Agenda summit, further said that each successful cyber breach cost a company USD 3.6 million (nearly ₹ 27 crore) last year, while the average share price of the hacked company underperformed NASDAQ by nearly 3 per cent even six months after the event in case of the breach becoming public.
Some 92 per cent of business executives surveyed agree that cyber resilience is integrated into enterprise risk-management strategies, but only 55 per cent of cyber leaders surveyed agreed. This gap between leaders can leave firms vulnerable to attacks as a direct result of incongruous security priorities and policies, the report said.
Even after a threat is detected, the WEF survey conducted in collaboration with Accenture, found that nearly two-thirds would find it challenging to respond to a cybersecurity incident due to the shortage of skills within their team.
According to many security experts, it’s a matter of “when” and not “if” your company will experience a serious cybersecurity incident. Any organization with digital assets (computers, servers, cloud workloads, data, etc.) has the potential to experience a cyber-attack or data breach. Unfortunately, most organizations don’t realize they’ve experienced a data breach until it’s too late.
Cybersecurity incident response plan
An incident response plan is your best chance at defending your organization from suffering the effects of a data breach. The time to plan and prepare your response to security incidents–whatever they may be–is long before they ever happen.
Creating a cybersecurity incident response plan helps you prepare for the inevitable and equip your IT security team to respond before, during, and after a cyber attack. A cybersecurity incident response plan (or IR plan) is a set of instructions designed to help companies prepare for, detect, respond to, and recover from network security incidents. Most IR plans are technology-centric and address issues like malware detection, data theft and service outages. However, any significant cyber attack can affect an organization across functions in multiple ways, so the plan should also encompass areas such as HR, finance, customer service, employee communications, legal, insurance, public relations, regulators, suppliers, partners, local authorities and other outside entities.
There are industry standard incident response frameworks from organizations such as NIST and SANS that provide general guidelines on how to respond to an active incident. Your organization’s IR plan, however, should be much more specific and actionable—detailing who should do what, and when.
Ideally, your security incident response plan should be leveraged on an ongoing basis — a living document — driving recurring detection and response activities (threat hunting, cyber incident investigations, incident response, and remediation/recovery). By performing ongoing detection and incident response activities, you can improve IT and security hygiene and better protect your organization from unknown threats, hidden attackers, and potentially prevent a data breach.
As cyber threats grow in number and sophistication, building a security team dedicated to incident response is a necessity. In many organizations, a computer security incident response team (CSIRT) has become essential to deal with the growing number and increasing sophistication of cyber threats.
An incident response plan should be set up to address a suspected data breach in a series of phases. Within each phase, there are specific areas of need that should be considered. The incident response phases are: Preparation, Identification, Containment, Eradication, Recovery, and Lessons Learned
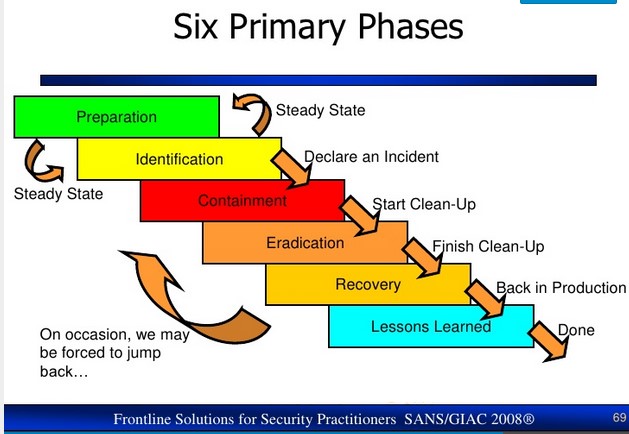
Preparation
Preparation is the first phase of incident response planning and arguably the most crucial in protecting your business and digital assets. During the preparation stage you’ll document, outline, and explain your IR team’s roles and responsibilities, including establishing the underlying security policy which will guide the development of your IR plan.
- Determine the exact location, sensitivity and relative value of all information in your organization that needs to be protected.
- Gauge whether you currently have sufficient IT resources to respond to an attack or whether third-party support would be required.
Gain executive buy-in so the plan has full approval from the top of the organization. - Assign roles and responsibilities for all relevant stakeholders, including IT, HR, internal communications, customer support, legal, PR and advisors.
- Establish a chain of command that includes both IT and corporate leaders. Who is the incident commander? Who launches the incident response plan? Who has “stop work” authority, such as the emergency shut down of company websites?
- Map the incident response workflow among different stakeholders. When is HR involved? When is legal involved? When is the media alerted? When are outside authorities involved?
- Gather and update 24/7/365 contact information (email, text, VOIP, etc.) for all incident response team members, their backups, and managers. Establish alternative channels of communication if regular channels are compromised or unavailable.
- Identify cybersecurity regulatory requirements for the organization across all functions and develop guidance on how to interact with law enforcement and other governmental authorities in the event of an incident.
- Develop and maintain a list of preferred technology vendors for forensics, hardware replacement, and related services that might be needed before, during or after an incident.
- Establish procedures for IT teams to receive clear, actionable alerts of all detected malware. Specific explanations can help team members avoid dismissing the alert as a false positive.
- Store privileged credentials, including passwords and SSH keys, in a secure, centralized vault.
- Automatically rotate privileged credentials, isolate privileged account sessions for temporary employees, and regularly scan for orphan accounts of former employees that might still provide unauthorized access.
- Request employees to report suspicious emails and activities that might compromise network security.
- Ensure that you have a clean system ready to restore, perhaps involving a complete reimage of a system or a full restore from a clean backup.
- Establish a comprehensive and integrated communications plan to inform both internal and external audiences on incidents in a rapid, accurate and consistent fashion.
Detection & Analysis
The detection phase of security incident response and IR planning involves monitoring, detecting, alerting, and reporting on security events. This includes identifying known, unknown, and suspect threats—those that appear malicious in nature, but not enough data is available at the time of discovery to make a determination either way.
When a lead, threat, or security incident is detected, your incident response team should immediately (if not automatically with the help of cyber incident response software) collect and document additional info—forensic evidence, artifacts, and code samples—to determine the severity, type, and danger of the incident, and store that data for use in prosecuting the attacker(s) at a later point in time.
- Develop a proactive detection strategy based on tools that can automatically scan your physical and virtual hosts, systems, and servers for any vulnerable applications, identities, or accounts.
- Consider traditional solutions such as Endpoint Detection and Response (EDR) platforms, Next-gen antivirus (NGAV) software, or User/Entity Behavior Analytics (UEBA/UBA) tools to detect malware.
- Also consider deep analysis and forensics-based capabilities that can assess the health of an endpoint by validating what is running in memory at a given point in time.
- Conduct compromise assessments to verify whether a network has been breached and quickly identify the presence of known or zero day malware and persistent threats active or dormant — that have evaded your existing cybersecurity defenses.
Response
Responding to security incidents can take several forms. Incident response actions may include triaging alerts from your endpoint security tools to determine which threats are real and/or the priority in which to address security incidents. Incident response activities can also include containing and neutralizing the threat(s)—isolating, shutting down, or otherwise “disconnecting” infected systems from your network to prevent the spread of the cyber attack. Additionally, incident response operations include eliminating the threat (malicious files, hidden backdoors, and artifacts) which led to the security incident.
- Immediately contain systems, networks, data stores and devices to minimize the breadth of the incident and isolate it from causing wide-spread damage.
- Determine if any sensitive data has been stolen or corrupted and, if so, what the potential risk might be to your business.
- Eradicate infected files and, if necessary, replace hardware.
- Keep a comprehensive log of the incident and response, including the time, data, location and extent of damage from the attack. Was it internal, external, a system alert, or one of the methods described previously? Who discovered it, and how was the incident reported?
- List all the sources and times that the incident has passed through. At which stage did the security team get involved?
- Preserve all the artifacts and details of the breach for further analysis of origin, impact, and intentions.
- Prepare and release public statements as soon as possible, describe as accurately as possible the nature of the breach, root causes, the extent of the attack, steps toward remediation, and an outline of future updates.
- Update any firewalls and network security to capture evidence that can be used later for forensics.
- Engage the legal team and examine compliance and risks to see if the incident impacts any regulations.
- Contact law enforcement if applicable since the incident may also impact other organizations. Additional intelligence on the incident may help eradicate, identify the scope, or assist with attribution.
Recovery and Follow-up
Post-incident activities (Recovery and Follow-up actions) include eradication of the security risk, reviewing and reporting on what happened, updating your threat intelligence with new information about what’s good and what’s bad, updating your IR plan with lessons learned from the security incident, and certifying then re-certifying your environment is in fact clear of the threat(s) via a post-incident cybersecurity compromise assessment or security and IT risk assessment.
Recovery
- Eradicate the security risk to ensure the attacker cannot regain access. This includes patching systems, closing network access and resetting passwords of compromised accounts.
- During the eradication step, create a root cause identification to help determine the attack path used so that security controls can be improved to prevent similar attacks in the future.
- Perform an enterprisewide vulnerability analysis to determine whether any other vulnerabilities may exist.
- Restore the systems to pre-incident state. Check for data loss and verify that systems integrity, availability and confidentiality has been regained and that the business is back to normal operations.
- Continue to gather logs, memory dumps, audits, network traffic statistics and disk images. Without proper evidence gathering, digital forensics is limited so a follow-up investigation will not occur.
Follow-up
- Complete an incident response report and include all areas of the business that were affected by the incident.
- Determine whether management was satisfied with the response and whether the organization needs to invest further in people, training or technology to help improve its security posture.
- Share lessons learned. What went well, what didn’t and how can procedures be improved in the future?
- Review, test and update the cybersecurity incident response plan on a regular basis, perhaps annually if possible.
- Conduct a compromise assessment or other security scans on a regular basis to ensure the health of systems, networks and devices.
- Update incident response plans after a department restructure or other major transition.
- Keep all stakeholders informed about the latest trends and new types of data breaches that are happening. Promote the message that “security is everyone’s job.”