Today, majority of organizations and many government departments and agencies have shifted their databases onto the cloud to improve efficiency and productivity of resources as well as bring down costs. Unfortunately, this move has exposed sensitive information to hackers, who have frequently launched cyber-attacks to retrieve and misuse data. The major challenge of cloud service providers has been of ensuring security.
A data center is a facility that stores IT infrastructure, composed of networked computers and storage used to organize, process, and store large amounts of data. For private companies moving to the cloud, data centers reduce the cost of running their own centralized computing networks and servers. Data centers provide services such as data storage, backup and recovery, data management and networking. Because data centers hold sensitive or proprietary information, such as customer data or intellectual property, sites have to be both digitally and physically secured.
Data centers have become attractive, lucrative targets for cyber criminals and nation-states. There are a number of reasons: Financial gain and notoriety; Theft of intellectual property (IP); Theft of private customer data—often used to instigate subsequent attacks (resulting in identity theft, stolen money from bank accounts, credit card fraud, etc.); Financial losses due to operational outages and brand damage;Social and environmental damage (particularly true in the case of nation-state attacks on OT); In the case of nation-states, compromise the national security assets of a geopolitical rival.
For instance, the US-based Center for Strategic & International Studies (CSIS) revealed that in April 2020 hackers from Iran attempted to breach personal files of World Health Organization (WHO) staffers while the world was reeling under the coronavirus pandemic. In February 2020, two Chinese hackers were persecuted by the US Department of Justice for performing cryptocurrency laundering activities for North Korean nationals. Earlier Credit Card Data Breach Affected 1.5 Million Cards. This recent breach of credit card numbers at Global Payments, a processing vendor for Visa, underscores the risks inherent with storing confidential and valuable data.
As digital data continue to flood into data centers via cloud computing, tablets and smart phones, those charged with securing these valuable facilities must assess their risk, including the threat of physical breaches from outside and within. Some industries in particular, such as financial and healthcare, are responsible for mass amounts of highly sensitive data, such as social security numbers, medical records and credit card accounts. Multitenant data centers must also be extremely vigilant in order to protect their customers’ data. The ramifications of allowing a data breach can be devastating to companies of any size. Besides the loss of confidence by business partners or customers that may entrust their data to you, there is often a significant financial fallout. In the Global Payments case, they were dropped by Visa and estimates place the financial loss at more than $100 million.
Data Center Attacks
Attacks are becoming increasingly multi-stage, targeting physical security through cyberattacks that create physical exposure. And with 34% of attacks involving internal players, physical security remains critical. The moral here is that cyber and physical security are complementary parts of a complete security program.
Distributed denial of service (DDoS) attacks. In addition to being on the receiving end of DDoS attacks whereby criminals seek to disrupt and disable essential internet services, web servers are being turned into bots to attack other websites and gain access into data center environments. DDoS is a serious problem, with attacks increasing in volume and sophistication in 2018. Research by IDC, as an example, reveals that half of IT security leaders indicate their organizations were a victim of DDoS attacks as many as 10 times in the past year. And these were sustained attacks, with 40 percent lasting over 10 hours.
Web application attacks that leverage vulnerabilities such as SQL injection, cross-site scripting, and cross-site request forgery are employed to break into applications and steal data for profit. With DevOps activities ramping up across most businesses, and many hosted in private cloud environments, the cybersecurity protections for applications must extend from pre-deployment to post-deployment. Research shows DevOps organizations have significant holes: 46 percent are confronting security risks up front, and only half are fixing major vulnerabilities.
DNS infrastructure: attack target and collateral damage. DNS servers can be taken offline very easily, thus keeping thousands of users from accessing the internet. DNS servers can also be used to amplify the impact of a DDoS attack (viz., drown victims with DNS traffic).
Secure sockets layer (SSL)/transport layer security (TLS)-induced security blind spots. Bad actors are turning to SSL/TLS to infiltrate data centers by wrapping and protecting the delivery of malicious payloads and then shielding data exfiltration upon successful intrusion. Many firewalls are not designed to scale with the additional requirements that SSL inspection requires, and organizations need to evaluate firewall performance capabilities.
Drastic Impact
Data center disruptions can have a dramatic impact on operations, quickly tallying into the hundreds of thousands of dollars. The average cost of a data center outage has increased almost 38 percent—hitting $9,000 per minute. Data center disruptions can have a dramatic impact on operations, quickly tallying into the hundreds of thousands of dollars. And this does not include brand repercussions. The severity of DDoS attacks is likely to continue to rise. Not only are they growing in frequency, but they are increasing in size (with new records set several times in 2018). Further, with fewer and fewer OT systems air-gapped, the attack surface for operational disruption and disablement becomes larger while the operational repercussions become dramatically greater.
The cost of these operational disruptions can spiral very quickly. In 2016, the average cost per minute per data center outage was $8,851 and most outages usually last longer than a minute. In fact, the average total cost of an outage is $740,000 which would translate to an average of one hour and twenty minutes of downtime. Data breaches are just as problematic for data centers. Data breaches equate to an average of $150 per record. On average, a data breach costs a company over $8 million in the U.S. which has increased slightly from 2018 and is more than twice the global average.
Data center security
Data center security refers to the physical practices and virtual technologies used to protect a data center from external threats and attacks. It includes the array of technologies and practices used to protect a facility’s physical infrastructure and network systems from external and internal threats. On a very basic level, data center security is all about restricting and managing access. Only authorized personnel should be able to access critical infrastructure and IT systems. Data center security includes both the “things” put in place to accomplish that goal (such as locked access points, surveillance systems, or security personnel) and the “controls” that manage them (such as security policies, access lists, or rules for handling data).
Today’s data centers are far more complex than a warehouse space filled with servers. They are often designed from the ground up with security best practices in mind. Every element of a data center’s physical security should be implemented with other elements in mind so that they form an interlocking network of security measures, each one enhancing the eectiveness of the others. However, no amount of physical security will provide much protection without a holistic security policy to manage it all. Protocols and procedures for common and unusual contingencies need to be in place to provide data center personnel with clear guidelines for how data center operations should be carried out.
Many IT companies are beginning to form DevSecOps, or Development, Security and Operations teams. These are teams built on the idea that everyone is responsible for security and share the common goal of “safely distributing security decisions at speed and scale to those who hold the highest level of context without sacrificing the safety required.” If things like securing points of entry are considered from a piece of software’s initial build, then loopholes to gain access to the device and ultimately the data centers’ storage of the devices’ information can be remedied before they are ever a concern.
Brute force and weak authentication. Applications employ authentication to verify user identity. Single-factor authentication (such as username and password only) is weak and criminals can use brute force to hack credentials. As covered above, data centers must employ multi-factor authentication to ensure bad actors are unable to bypass authentication controls.
Integrate operational technology (OT) and informational technology (IT). Traditionally, OT and IT have been siloed as separate organizational functions. Operations kept the data centers running while IT managed business applications from the office. However, with technology rapidly changing and the convergence of physical and cyber, it’s critical that OT and IT teams work hand-in-hand to prevent and combat security threats.
These controls need to be developed in advance and regularly tested to ensure that everyone knows how (and why) to keep the facility secure from potential threats. By implementing a “Zero Trust” security philosophy, data centers can greatly reduce the risk of unauthorized access because everyone is subjected to the same high level of scrutiny and must verify their identity and reason for accessing assets at every turn. Like any other data center policy, these processes should be audited regularly to ensure their eectiveness.
Data centers must be diligent to ensure physical and cyber systems are protected in a unified way, and that their convergence does not create additional risks. Further, data centers will begin to see advanced technologies such as artificial intelligence (AI) and machine learning (ML) deployed to pinpoint anomalies in both physical and cyber security and to enact real-time controls and remediation processes.
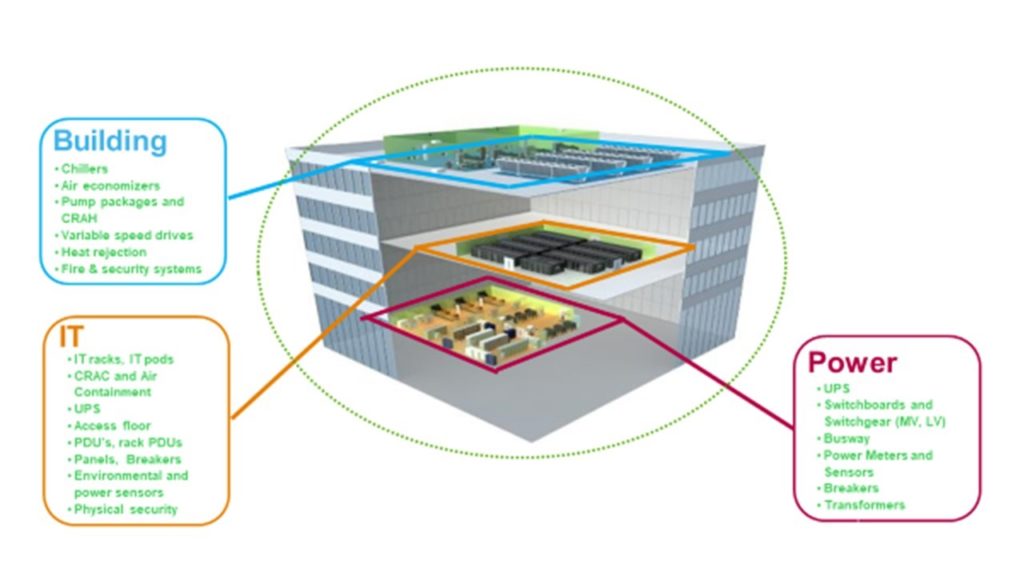
Physical Security
It is important for your data center to be prepared for the unexpected. Any number of things could go wrong such as utility failure, cooling system equipment failure, fire, air quality issues and natural disasters. Manipulation of heating and ventilation controls (HVAC) could result in critical infrastructure systems being shut down or compromised. Physical cameras could be hacked and commandeered to disguise a robbery or unauthorized entry into a secure location. That is why building out a redundant design for your data center is crucial.
Nowdays, Data centers are monitored and managed through a network of hundreds or even thousands of sensors used for real-time telemetry—heating and cooling, maintenance alerts, physical security, and much more. Yet, in addition to introducing new opportunities for enhanced operational efficiencies and greater visibility and control, digital transformation (DX) presents new challenges.
A data center building’s most obvious security characteristics are related to design and layout. The building itself may be designed as a single-purpose or multipurpose unit, the latter of which operates as a shared space and may house businesses unrelated to the data center. A data center building is usually built away from major roads in order to establish buffer zones made up of a combination of landscaping and crash-proof barriers.
However, the need to focus on controlled access, meaning designated workers should be able to access only the areas, systems, and applications to which they should have access, remains the foundational concept of ensuring the confidentiality, integrity and availability of data wherever it resides and regardless of how it is used.
Access into a data center facility is fairly limited. Most do not have exterior windows and relatively few entry points. Security guards inside the building monitor for suspicious activity using footage from surveillance cameras installed along the outside perimeter. Visitors may use two-factor authentication to enter the building, including scanning personal identity verification (PIV) cards and entering a personal passcode. Employee badge readers and biometric systems, such as fingerprint readers, iris scanners and facial recognition, may also be used to permit entry.
AI and ML provide the means to monitor physical security devices such as doors and cameras, pinpointing anomalies, sending real-time alerts to data center personnel, and even acting as a digital system to immediately combat threats without human intervention.
Software Security
Hacking, malware and spyware are the obvious threats to data stored in a data center. A security information and event management tool (SIEM) offers a real-time view of a data center’s security posture. A SIEM helps provide visibility and control into everything from access and alarm systems and sensors on the perimeter fence.Creating secure zones in the network is one way to layer security into the data center. Administrators can split networks into three zones: a test area with a great deal of flexibility, development zone with a slightly more stringent environment, and a production zone with only approved production equipment.
Before applications and code are deployed, certain tools may be used to scan them for vulnerabilities that can be easily exploited, and then provide metrics and remediation capabilities. Code may be run through a scanner to check for buffer overflows or other vulnerabilities. With the rise of cloud computing, visibility into data flows is a necessity, since there could be malware hiding inside of otherwise legitimate traffic.
Data centers need to ensure that their cyber and physical security is seamlessly integrated. Physical systems and devices must reside on secure networks and behind firewalls. This helps protect them from malicious attacks, while providing seamless incident response capabilities in the event of an intrusion.
Other security strategies that data center leaders should have in place include:
Data governance—at rest and in transit, across and between multiple cloud environments. Most enterprises are experiencing 40-50% annual growth in unstructured data. To protect this information, whether on-premises or the cloud, organizations need to implement data governance policies in control—for moving data across and between different environments and between applications.
Cloud transparency and controls. For public clouds, organizations need to ensure they have the right governance policies and controls in place. These are important. Gartner predicts that 60 percent of enterprises with cloud governance will experience 33 percent fewer security incidents.
Security integration. 83 percent of IT leaders cite organizational complexities as putting them most at risk. Only 48% have security policies in place to manage data access amongst employees and third parties. A new, integrated security framework is needed. Traditional security architectures are fragmented, and it is difficult to share information across and between the different elements. This includes new data center attack surface areas such as DevOps and the cloud for full transparency and centralized controls.
Protecting the edge of network. 5G increases the ease and speed at which devices attach to the network as well as the amount of data that can be accessed and moved. IoT poses substantial risk (as these devices cannot be managed via traditional security models), and lateral intrusions can impact data center security. Software-defined wide area networks (SD-WAN) leverage 5G as an additional bandwidth channel, which bypasses traditional data center security controls. This increases risk that can back-funnel into the data center via lateral movement.
Threat intelligence: artificial intelligence and machine learning. 85% of organizations indicate threat intelligence is critical to a strong security posture. But only 42% believe they are very effective in using threat intelligence. Part of the problem is lack of in-house expertise (50%). To keep pace with security threats that are using artificial intelligence (AI) and machine learning (ML) and are polymorphic and multi-vector, cybersecurity leaders must employ ML and AI capabilities themselves, or switch to tools that have AI/ML enhanced capabilities. This enables them to reduce the attack surface for prevention, detection, and remediation.
Edge security
Many traditional physical devices now represent threats to cyber security. Things like ID cards, biometrics, HVAC, laptops, smartphones, and USBs are all cyber security threats since they are now IP-enabled. In fact, IoT devices experience an average of 5,200 attacks per month.
Protecting the edge of network. 5G increases the ease and speed at which devices attach to the network as well as the amount of data that can be accessed and moved. IoT poses substantial risk (as these devices cannot be managed via traditional security models), and lateral intrusions can impact data center security. Software-defined wide area networks (SD-WAN) leverage 5G as an additional bandwidth channel, which bypasses traditional data center security controls. This increases risk that can back-funnel into the data center via lateral movement.
Google cloud platform security
Design for security is pervasive, throughout the infrastructure, the GCP and Google services run-on. Let’s talk about a few ways Google works to keep customers’ data safe, starting at the bottom and working up. Both the server boards and the networking equipment in Google data centers are custom designed by Google. Google also designs custom chips, including a hardware security chip called Titan that’s currently being deployed on both servers and peripherals.
Google server machines use cryptographic signatures to make sure they are booting the correct software. Google designs and builds its own data centers which incorporate multiple layers of physical security protections. Access to these data centers is limited to only a very small fraction of Google employees, not including me.
Google’s infrastructure provides cryptographic privacy and integrity for remote procedure called data-on-the-network, which is how Google services communicate with each other. The infrastructure automatically encrypts our PC traffic in transit between data centers.
Google Central Identity Service, which usually manifests to end users as the Google log-in page, goes beyond asking for a simple username and password. It also intelligently challenges users for additional information based on risk factors such as whether they have logged in from the same device or a similar location in the past. Users can also use second factors when signing in, including devices based on the universal second factor U2F open standard. Here’s mine.
Most applications at Google access physical storage indirectly via storage services and encryption is built into those services. Google also enables hardware encryption support in hard drives and SSDs. That’s how Google achieves encryption at rest of customer data. Google services that want to make themselves available on the Internet register themselves with an infrastructure service called the Google Front End, which checks incoming network connections for correct certificates and best practices.
The GFE also additionally, applies protections against denial of service attacks. The sheer scale of its infrastructure, enables Google to simply absorb many denial of service attacks, even behind the GFEs. Google also has multi-tier, multi-layer denial of service protections that further reduce the risk of any denial of service impact.
Inside Google’s infrastructure, machine intelligence and rules warn of possible incidents. Google conducts Red Team exercises, simulated attacks to improve the effectiveness of its responses. Google aggressively limits and actively monitors the activities of employees who have been granted administrative access to the infrastructure. To guard against phishing attacks against Google employees, employee accounts including mine require use of U2F compatible security keys. I don’t forget my keys as much as I used to. To help ensure that code is as secure as possible Google stores its source code centrally and requires two-party review of new code. Google also gives its developers libraries that keep them from introducing certain classes of security bugs. Externally, Google also runs a vulnerability rewards program, where we pay anyone who is able to discover and inform us of bugs in our infrastructure or applications.
References and Resources also include: