Metamaterials are artificially structured materials designed to control and manipulate physical phenomena such as light and other electromagnetic waves, sound waves and seismic waves in unconventional ways, resulting in exotic behavior that’s not found in nature. This class of micro- and nano-structured artificial media are predicted to be able to protect …
Read More »Yearly Archives: 2022
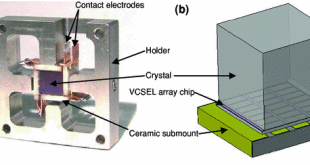
Vertical-cavity surface-emitting lasers (VCSEL& VECSEL) arrays enable data communication to lidar and military infrared imaging
The illumination source employs different technologies, ranging from lamps to semiconductor light emitting diodes (LEDs) or lasers. The lamp, while straight-forward, is broad-band, bulky, and generally inefficient. The main wavelengths of interest for illumination are around 808nm, 976m, 1064nm, and 1550nm. The 808nm region offers the best responsivity for …
Read More »Europe and US launch Quantum testbeds and Quantum loop to catchup China in Quantum Communications Race
The race to conquer the quantum domain is among the most fiercely competitive in today’s world of technology. One important quantum technology is Quantum key distribution (QKD), that establishes highly secure keys between distant parties by using single photons to transmit each bit of the key. Quantum cryptography is unbreakable …
Read More »DARPA SDCPS & JARVIS developing AI assisted design of Military Cyber Physical Systems
Cyber physical systems (CPS) are instrumental to current and future Department of Defense (DoD) mission needs – unmanned vehicles, weapon systems, and mission platforms are all examples of military-relevant CPS. These systems and platforms integrate cyber and physical subsystems, and the enormous complexity of the resulting CPS has made their …
Read More »DOD developing hardened Military GPS receivers or User Equipment (MGUE) to mitigate the threat of GPS Jamming and Navigation Warfare
Systems like GPS, Russia’s GLONASS, China’s BeiDou, and Europe’s Galileo systems are Global Satellite Navigation Systems (GNSS) that provides real-time positioning, navigation and timing (PNT) data. The worldwide Global Positioning System (GPS), created in the late 1980s, has evolved to become an essential part of life for nearly every person on …
Read More »DARPA SBIR for 3D printing of safe and edible food products converted from waste
With nutritional status being central to success in battle, food technology has long been considered an enabler for military operations. Food technology has been instrumental in ensuring that troops remain “fit to fight”. 3D printing technology for food continues to advance. The 3D printing technology will be fundamental to …
Read More »DARPA Quantum Apertures (QA) developing employing Rydberg atoms for military electronic warfare, radar, and communications.
The world, say many experts, is on the verge of a second quantum revolution. Many scientists believe that quantum will enjoy its first real commercial success in sensing. That’s because sensing can take advantage of the very characteristic that makes building a quantum computer so difficult: the extraordinary sensitivity of …
Read More »Electronic Components Market
An electronic components is a physical entity in an electronic device that is used to affect the electronic field. Electronic components are categorized into two types i.e. active components and passive components. Active electronic components are used to produce energy in the form of voltage, whereas passive electronic components are used …
Read More »Artificial Intelligence for Early Warning Intelligence and effective response for CBRN threats
The threats of chemical, biological, radiological, nuclear and explosive (CBRNE) hazards continue to advance. CBRN weapons are some of the most indiscriminate and deadly weapons in existence today, with capability to affect large population in wide geographical area and in short time. The release of Chemical, Biological, Radiological and Nuclear …
Read More »Neural and tensor holography enables realistic 3D holographic images in virtual and augmented reality headsets
Virtual reality headsets have gained tremendous popularity. However, one common problem tends to occur— the headsets can make users feel sick. Nausea can be experienced because users’ eyes are being tricked into seeing a 3D scene, when, in fact, they are staring at a 2D fixed-distance display. One possible solution …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis