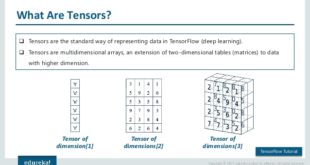
In mathematics, a tensor is an algebraic object that describes a linear mapping from one set of algebraic objects to another. According to Ars Technica, “Basically, a tensor is a matrix of equations, instead of a matrix of pure numbers. Tensor mathematics is the manipulation of these equation matrices as …
Read More »Recent Posts
Nanogenerators or Nanotechnology enabled Energy harvesting technologies could soon power Smartphones, IoT sensors, biomedical implants and reduce the soldier’s load
Energy harvesting is the process of collecting low-level ambient energy and converting it into electrical energy to be used as a power source for miniaturized autonomous devices. Examples of this can be seen in structural health monitoring, smart packaging solutions, communication systems, transportation, air and aerospace vehicles, structural biology, robotics, …
Read More »Soldiers employing human Energy harvesting technologies including Backpack, knee kinetic and Heel-strike to power devices on the battlefield
The vision for the future soldier is to be combat effective and also highly mobile, adaptive, networked, sustainable with total battle space situation awareness and information assurance. Therefore, he is equipped with night- vision goggles, radios, smartphones, GPS, infrared sights, a laptop as well as batteries to power them. Some …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis