Introduction
In an increasingly digital world, mission-critical systems are the backbone of our modern infrastructure. From healthcare and transportation to defense and space exploration, these systems ensure that vital operations run smoothly and securely. In today’s digital age, software is the backbone of mission-critical systems. Whether it’s healthcare, transportation, defense, or space exploration, these systems rely on intricate lines of code to function seamlessly.
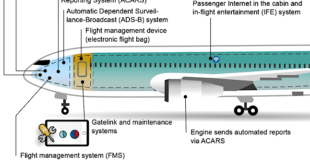
The Air Force vision document Global Horizons traces the percentage of capability in air systems reliant on software through generations of aircraft. By the mid-1970s, when theF-16 went into production, software accounted for about 40percent of capability. A generation later, the F-22 relied on software for 80 percent of capability. Software may contribute 90 percent of capability for today’s premier fighter, the F-35.In addition, millions of lines of software are required to supportF-35 Lighting II ground functions. Software’s critical role in delivering capability is driving commercial aircraft makers toseek a new development paradigm.
However, as the world becomes increasingly reliant on software-driven systems and components, the risk of software errors and cyberattacks on mission-critical systems is on the rise. The consequences of such incidents can be catastrophic, affecting safety, security, and national interests.
To address these concerns, the Department of Defense (DOD) has placed a strong emphasis on Software Assurance, aiming to ensure high-quality, safe, secure, and reliable software for mission-critical applications. This article explores the critical importance of Software Assurance and its role in assuring high-quality, safe, secure, and reliable software for mission-critical applications. From historical accidents to modern-day challenges, we delve into the significance of Software Assurance in safeguarding our most critical systems.
The Threat of Software Errors
Software errors, commonly known as “bugs,” can have far-reaching consequences. In healthcare, a software glitch can lead to incorrect patient data, jeopardizing lives. In transportation, a software malfunction in autonomous vehicles can result in accidents. In defense, software errors can compromise the security and effectiveness of military operations. Even in space exploration, a single software error can lead to mission failure.
One of the most infamous cases highlighting the importance of software quality is the Therac-25 incidents between 1985 and 1987. Six known accidents involving this medical device resulted in massive overdoses, leading to fatalities and severe injuries. The root causes included errors in the control program, excessive trust in software, and a lack of hardware safety measures.
- Astra LV0008 Rocket 3 mission failure (February 2022): The Astra LV0008 Rocket 3 mission failed due to two software errors. The first error caused the fairing to deploy incorrectly, and the second error caused the upper stage engine to lose thrust vector control.
- Russia’s Nauka module failure (July 2022): Russia’s Nauka module docked with the International Space Station in July 2022, but it began firing its thrusters shortly after docking, causing the space station to lose attitude control. The failure was caused by a software glitch that caused the module to think it was drifting away from the space station.
- Phobos 1 mission failure (September 1988): The Phobos 1 spacecraft was launched in 1988 to study the Martian moons Phobos and Deimos. However, the spacecraft lost contact with Earth in September 1988. The failure was caused by a software error that caused the spacecraft to execute a test routine that shut down its attitude thrusters.
- A 2.6 billion rouble ($A58 million) Russian weather satellite and nearly 20 micro-satellites from other nations were lost following a failed launch of the Meteor-M from Russia’s new cosmodrome in the far east on November 28. And in another blow to the Russian space industry, communications with a Russian-built communications satellite for Angola, the African nation’s first space vehicle, were lost following its launch in Dec 2017.
- In October 2018, Lion Air Flight 610 crashed just minutes after taking off from Jakarta, Indonesia. It was the first fatal accident involving a 737 Max. 189 people died. On March 10 2019, Ethiopian Airlines Flight 302, involving the same Max jet model, also crashed minutes after takeoff, killing all 157 people on board. In both accidents, the automated Maneuvering Characteristics Augmentation System, or MCAS, pushed the planes’ noses down while the pilots struggled to regain control. The Max has larger engines, which alter the planes aerodynamics and make it more likely to stall in some flight conditions. Boeing developed an automatic system, known as MCAS, that pushes the plane’s nose down in some circumstances in order to stabilize the aircraft. Boeing said in May 2019 that it has finished the development of a software fix to its troubled 737 Max. The plane maker said in a statement it has flown the aircraft with the updated software on 207 flights for more than 360 hours. The company has said its fix will feed MCAS with data from two, rather than just one, sensor, making the plane less susceptible to a crash because of bad data. It will also make the system less potent, which is expected to prevent the steep dives seen in the two crashes, and provide additional training materials.
Cybersecurity Challenges
Beyond software errors, cyberattacks pose a grave threat to mission-critical systems. As cybercriminals become more sophisticated, they can infiltrate and disrupt essential services, causing chaos and compromising national security. Nation-states, terrorists, criminals, and rogue developers can exploit vulnerabilities remotely, posing serious risks to these systems. Cyberattacks can result in data breaches, system shutdowns, and even unauthorized access to sensitive military information. The Department of Defense (DOD) recognizes this growing concern and is taking steps to address it.
DOD’s Emphasis on Software Assurance
Software is important for the DoD because it promotes lower cost and improved agility in deploying and reconfiguring systems. One result is reflected in the DoD’s ability to now program systems that were once fixed-function to meet changing mission needs. Sensor networks, field programmable gate arrays, software-defined networking, software-defined radios, and embedded controllers represent a few of these now-programmable areas.
“Another result is that software enables the interconnectivity that is central to accomplishing system-of-systems configurations. Systems of systems support network-centricity, aiding DoD mission goals for information superiority. “
The DOD has prioritized Software Assurance to ensure high-quality software that meets stringent safety, security, and reliability standards. The term “Software Assurance” encompasses a comprehensive approach to ensuring software quality, safety, security, and reliability. It involves rigorous testing, code reviews, vulnerability assessments, and continuous monitoring to identify and mitigate software-related risks.
DOD defines Software Assurance as the level of confidence that software functions as intended and is free of vulnerabilities, either intentionally or unintentionally designed or inserted as part of the software throughout the lifecycle. Failures in software assurance can be of particularly high consequence for defense systems due to their growing roles in protecting human lives, in war fighting, and in safeguarding national assets.
The software assurance process is the planned and systematic set of activities that ensure conformance of software life cycle processes and products to requirements, standards, and procedures.
System Security Engineering (SSE)
Software Assurance is a vital objective for the Department of Defense (DoD) as it strives to establish software assurance as a recognized discipline within its system engineering framework. This initiative transcends traditional boundaries, encompassing diverse domains and impacting not only security but also software development, testing, deployment, and operational practices. SSE Software Assurance offers an array of tools and techniques that bolster cybersecurity, guide software design, enhance development methodologies, optimize testing procedures, and mitigate supply chain risks. Recognized as an increasingly critical facet of the industry, it demands cooperative research, active participation, innovative solutions, and robust engagement across sectors. Nevertheless, it comes with a set of challenges, such as translating systems engineering requirements into practical SwA contract language, defining effective metrics for security risk evaluation and vulnerability detection, fostering workforce education, ensuring tool scalability and efficiency, and seamlessly integrating SwA capabilities into engineering disciplines. Overcoming these challenges is essential to fortify software assurance practices across the DoD’s extensive system life cycle.
Cybersecurity
Software quality in today’s context extends far beyond traditional metrics and encompasses cybersecurity as an indispensable facet. It’s not just about creating reliable, efficient software; it’s about safeguarding it from adversarial or malicious users who can pose significant threats throughout the software lifecycle. To ensure software quality, cybersecurity considerations must be woven into every stage, starting from the acquisition phase and continuing through design, development, deployment, and ongoing maintenance.
This is especially critical in the backdrop of complex and globally distributed software supply chains that comprise various components, including physical elements, integrated devices, software, prime contractor organizations, subcontractors, and commercial products. The diversity within these supply chains, particularly in terms of varying software quality levels, elevates cybersecurity and mission risks. Additionally, the specter of insider threats, exemplified by incidents like Edward Snowden’s actions and the Target Corporation breach, highlights the potential dangers arising from both malicious and unintentional insiders.
Secure coding practices, rigorous testing, and adherence to international secure coding standards are essential elements of achieving software quality with embedded cybersecurity. By eliminating common vulnerabilities during the software development phase, not only does the software become more secure, but substantial cost reductions can also be realized, as less effort is needed to address and repair vulnerabilities. Advanced testing methodologies, including full-scale penetration testing by internal or external experts, further fortify the cybersecurity posture of software systems.
Achieving assured software quality and resilience against cyber vulnerabilities demands a multifaceted approach embedded in the software development process.
It begins with meticulous project estimation, planning, and control, underpinned by detailed historical data encompassing cost, schedule, and technical performance. Data-driven management and best practices are pivotal, requiring rigorous documentation, institutionalization, and enforcement of software project management and technical development processes. Joe Heil from the Naval Surface Warfare Center Dahlgren Division advocates for ongoing quantitative and qualitative information sharing to address vital execution questions.
Continuous improvement is vital and involves the integration of emerging best practices, encompassing user-centered and model-based system and software engineering, documented traceability between requirements, design, code, and test artifacts, multidisciplinary expert peer reviews, agile development, automated testing, defect tracking, and causal analysis.
Software assurance extends beyond applying security patches; it must be woven into the fabric of development, focusing on resilience against cyber intrusions, secure coding, integrated tools for vulnerability detection and removal, and penetration testing during all testing phases.
Formal risk management processes, encompassing risk identification, communication, and mitigation across cost, schedule, and technical performance dimensions, are imperative. Risks should be methodically documented and addressed via structured risk boards, with clear responsibilities and objective data driving discussions.
Success hinges on a collaborative approach that combines government software engineers’ hands-on involvement in architecting, designing, coding, integrating, and testing complex software components with industry efforts. This teamwork, coupled with data-driven project management and technical execution practices, has yielded high-quality, safe, reliable, and operationally successful software systems developed within budget and schedule constraints, as emphasized by Joe Heil.
Key Initiatives in Software Assurance
Software assurance assures that the software and its related products meet their specified requirements, conform to standards and regulations, are consistent, complete, correct, safe, secure and as reliable as warranted for the system and operating environment, and satisfying customer needs.
Software Assurance involves comprehensive testing, code reviews, vulnerability assessments, and continuous monitoring to identify and mitigate risks throughout the software lifecycle.
- Code Reviews: In-depth code reviews are essential for identifying vulnerabilities and weaknesses before they can be exploited.
- Penetration Testing: Ethical hacking helps identify vulnerabilities and strengthen defenses against cyber threats.
- Secure Coding Practices: Developers are trained to write secure code to reduce the risk of vulnerabilities.
- Continuous Monitoring: Real-time monitoring detects anomalies and vulnerabilities, allowing for immediate corrective action.
The Department of Defense (DoD) has a number of initiatives in place to ensure the software assurance of its mission-critical systems. These initiatives include:
- The DoD Software Assurance Initiative (SAI): The SAI is a comprehensive program that aims to improve the security and reliability of DoD software systems. The SAI includes a number of initiatives, such as the development of secure software development practices, the testing of software for vulnerabilities, and the monitoring of software systems for cyber attacks.
- The DoD Cyber Range: The DoD Cyber Range is a virtual training environment that allows DoD personnel to practice defending against cyber attacks. The Cyber Range includes a variety of scenarios that simulate real-world cyber attacks.
- The DoD Software Assurance Maturity Model (SAMM): The SAMM is a framework that helps organizations to assess their software assurance capabilities. The SAMM includes a set of maturity levels that organizations can strive to achieve.
- The DoD Software Assurance Research Center (SARC): The SARC is a research center that focuses on developing new technologies and techniques for software assurance. The SARC works with universities and industry partners to develop new solutions to the challenges of software assurance.
In addition to these initiatives, the DoD is also working to improve the software assurance of its mission-critical systems by:
- Adopting new technologies: The DoD is adopting new technologies, such as artificial intelligence (AI) and machine learning (ML), to help improve the security and reliability of its software systems.
- Working with industry: The DoD is working with industry to develop new secure software development practices and tools.
- Educating personnel: The DoD is educating its personnel on the importance of software assurance and how to develop and maintain secure software systems.
The Benefits of Software Assurance
- Enhanced Security: Software Assurance strengthens the resilience of mission-critical systems against cyber threats.
- Improved Reliability: Rigorous testing results in more reliable software, reducing the risk of system failures.
- Cost Savings: Preventing software errors before deployment saves resources compared to addressing them later.
- Safety and Trust: Software Assurance ensures the safety of critical systems and maintains public trust.
Conclusion
As mission-critical systems become increasingly software-driven, the risks associated with software errors and cyberattacks cannot be underestimated. The DOD’s commitment to Software Assurance demonstrates its dedication to upholding the highest standards of quality, safety, security, and reliability in mission-critical software. By continually advancing Software Assurance practices, we can mitigate the rising threats to our essential systems, ensuring a safer and more secure future for all.
References and resources also include:
 International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis