In our information society, the synthesis, distribution, and processing of radio and microwave signals are ubiquitous in wireless networks, telecommunications, and radars. The current tendency is to use carriers in higher frequency bands, especially with looming bandwidth bottlenecks due to demands for e.g. 5G and the “Internet of Things.” “Microwave …
Read More »TimeLine Layout
September, 2021
-
26 September
Metal 3D Printing
Additive manufacturing (AM), broadly known as 3D printing, is transforming how products are designed, produced, and serviced. AM enables on-demand production without dedicated equipment or tooling, unlocks digital design tools, and offers breakthrough performance and unparalleled flexibility across industries. Metal 3D printing is considered the apex of all 3D …
Read More » -
26 September
Militaries develop AI and machine learning enabled cognitive communications, Intelligence gathering and electronic warfare systems
Electronic warfare (EW) is one of the crucial aspects of modern warfare. EW receivers are passive systems that receive emission from various platforms that operate in the relative vicinity. The received signals are typically analyzed to obtain valuable information about characteristics and intentions of various elements that are presented in …
Read More » -
26 September
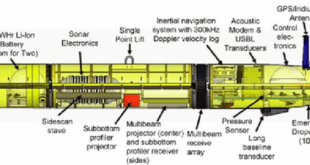
Autonomous underwater vehicle (AUV) technologies for surveillance, and anti-submarine warfare missions
An autonomous underwater vehicle (AUV) is a robot that travels underwater without requiring input from an operator. AUVs constitute part of a larger group of undersea systems known as unmanned underwater vehicles, a classification that includes non-autonomous remotely operated underwater vehicles (ROVs) – controlled and powered from the surface by …
Read More » -
25 September
Hybrid marine propulsion system technology for smart ships
Marine propulsion is the mechanism or system used to generate thrust to move a ship or boat across water. At present, 90% of the sea-going naval ship are diesel-powered. To achieve the safe upper limit for global warming of 1.5 degrees Celsius, ‘all ships designed and built today must operate in …
Read More » -
24 September
Emerging Indian ocean geopolitics heading for Quad (US, India , Australia & Japan ) Vs Quad (Russia, China, Pakistan and Iran )
The IOR is the region around the Indian Ocean. It includes the 22 member nations of the Indian Ocean Rim Association (IORA), along with other countries such as Myanmar in Southeast Asia, Pakistan, and Djibouti in East Africa. The People’s Liberation Army Navy (PLAN) fleet is increasingly designed for oceanic …
Read More » -
22 September
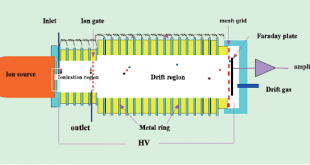
Ion Mobility Spectrometry and Its Applications in Detection of Chemical Warfare Agents
The threat of weapons of mass destruction (WMDs), such as chemical warfare agents (CWAs) and toxic industrial chemicals, is of great concern worldwide. This menace makes it necessary to detect the presence of such weapons in both military and civil environs. Toxic chemicals are used in large quantities by industry, …
Read More » -
21 September
DARPA MACH & HEAT developing rugged high temperature materials RF radome & IR window for hypersonic vehicles
The era of hypersonic flight had arrived. Countries are developing future hypersonic Spaceplanes , enabling intercontinental travel at very high speeds, that could cut the journey times from the UK to Australia from the current duration of around 20 hours to as little as two hours. They shall also provide …
Read More » -
20 September
fire control system
A fire-control system (sometimes called FCS) is a number of components working together, usually a gun data computer, a director, and radar, which is designed to assist a ranged weapon system in targeting, tracking, and hitting its target. It performs the same task as a human gunner firing a weapon, …
Read More » -
19 September
Homeland security threats and Counter Terror & Public Safety Technology Market
Today’s terrorist landscape is more fluid and complex than ever influenced by economic and social conditions that breed extremism and the threat landscape is less predictable. The Countries face an increasingly complex terrorist landscape, populated by a diverse array of actors employing new technologies and tactics across physical and cyber …
Read More »
 International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis