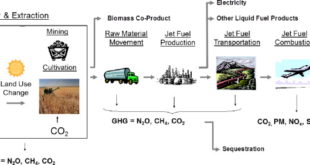
Global aviation fuel market was valued at US$178.560 billion in 2019 and is expected to grow at a CAGR of 6.00% to reach a total market size of US$253.261 billion in 2025. Booming travel and tourism industry is one of the major drivers of global aviation fuel market. According to …
Read More »TimeLine Layout
April, 2021
-
19 April
Continuing interest of Space agencies and Militaries to exploit Zero-Point Energy for applications like propulsion and for generating electric power.
Zero-point energy is the energy that remains when all other energy is removed from a system. Zero-point energy is the lowest energy that a given quantum mechanical system can have (i.e., the ground state of the system). In quantum field theory, it refers to the energy of the vacuum (i.e., …
Read More » -
18 April
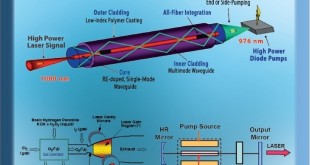
Militaries developing scalable hundreds of Kilowatts to Megawatts High Power Laser technologies for air and missile defense
The Laser Directed Energy Weapons (DEWs) offer a transformational ‘game changer’ to counter asymmetric and disruptive threats, while facing increasingly sophisticated traditional challenges. Laser technology provides major advantages for military applications over kinetic weapons due to High precision and rapid on-target effect, precise and scalable effects, avoidance of collateral damage …
Read More » -
18 April
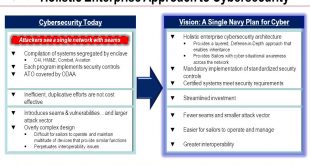
Navies developing cyber security measures and cyber defense technologies to counter growing cyber threats
Ships are increasingly using systems that rely on digitization, integration, and automation. Offensive actors understand the naval reliance on communications, ISR, and visualization technologies, and perceive them as vulnerable to disruption and exploitation. In 2016, the Baltic and International Maritime Council (BIMCO) in their “Guidelines on Cyber Security Onboard Ships,” warned about the …
Read More » -
17 April
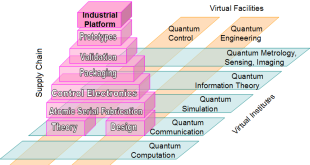
Quantum engineering established at leading universities world-wide to realize quantum hardware of quantum computers, cryptography and sensors
Traditionally, quantum science has been a domain of fundamental research explored mostly by physicists. At the current state of the art the basic properties of the systems considered for realizing quantum hardware are understood at a great level of detail. Now, it becomes increasingly more important to develop quantum systems which …
Read More » -
17 April
Flexible displays enable lighter-weight, lower-power, more-rugged smartphones , soldiers wearable and vehicle applications
With the flat panel display having already been widely used more than 40 years, there have been many desired changes in the display technology, focusing on developing a lighter, thinner product that was easier to carry and store. A flexible display or rollable display is an electronic visual display which …
Read More » -
15 April
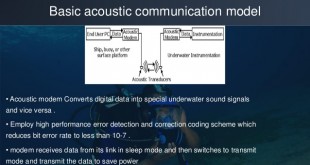
Underwater Acoustic Wave (UWAC) Communication technologies including Acoustic Modems enable Unmanned Underwater Vehicles (UUWs) missions
Approximately 70% of the Earth’s surface is covered by water, yet almost 95% of the underwater world remains unexplored. Nearly 4000 robots are swimming up and down in the world’s oceans, which allow scientists to measure and understand ocean dynamics, like the directions and speeds of currents, as well as …
Read More » -
15 April
Fuel cells technologies enabling less expensive, durable, eco friendly power on-demand for transportation and military systems
Since the Industrial Revolution, the environmental impacts of energy have posed a concern. Recently, this has driven researchers to search for viable options for clean and renewable energy sources. Due to its affordability and environmental friendliness, hydrogen is a feasible alternative to fossil fuels for energy applications. However, due to its …
Read More » -
13 April
Heterogeneous computing architecture for emerging digital warfare
The world of high-performance computing is particularly challenging, as new flavors of sophisticated sensors, complex cameras, and the requirements of Advanced computations, which include Software-Defined Radio, cryptography, and other types of arithmetic-intensive algorithms. Recent developments in artificial intelligence (AI) and growing demands imposed by both the enterprise and military sectors …
Read More » -
11 April
Multi-factor authentication has become essential to protect accounts in commercial and military
The traditional, not so secure way to log in to your bank account: enter your username and that familiar password you probably use for most of your online accounts. Then, you’re in. You can go about your business. If you’re one of the 54% of consumers who, according to TeleSign, …
Read More »
 International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis