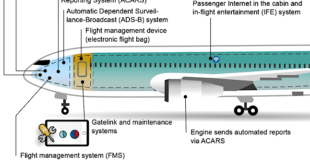
Cyberspace is essential to all Air Force (AF) missions. It is a domain in which, from which, and through which AF missions are performed. Actions in cyberspace can have digital, kinetic, and human effects. Increasingly, the cyberspace domain is contested and/or denied. Yet our ability to address opportunities and threats is constrained by time, treasure, and talent. There is increasing concern that U.S. Air Force systems containing information technology are vulnerable to intelligence exploitation and offensive attack through cyberspace.
DoD officials have been raising the alarm about the need to invest in cyber capabilities, not least because of developments being made by Russia, China, Iran, and other entities. Evidence of the threats have included Russia’s attacks on U.S. infrastructure, its meddling in U.S. elections, and the variety of cyber attacks employed in a hybrid warfare campaign against Ukraine. And, it’s not just Russia. The Chinese are also guilty of cyber espionage campaigns against U.S. government and business institutions.
Keeping up with the competition in cyberspace means getting new technologies, products and capabilities developed, tested, and into the field before anybody else. This requires an R&D and acquisition approach that runs counter to the traditional method of weapons procurement.
Cyber Vision 2025 provides the Air Force vision and blueprint for cyber S&T spanning cyberspace, air, space, command and control, intelligence, and mission support. Cyber Vision focuses on S&T in the near (FY12-15), mid (FY16-20), and far (FY21-25) term, delineating
where the Air Force should lead, follow, or watch.
Cyber Vision 2025 finds that our missions are at risk from malicious insiders, insecure supply chains, and increasingly sophisticated adversaries as well as growing (often cyber) systems interdependencies. Fortunately, cyberspace S&T can provide assurance, resilience, affordability, and empowerment. However, this requires integration across authorities and domains, shaping of doctrine, policy, people, and RDT&E processes, and intelligent partnering
Agile Cyber Technology (ACT )-2 ups the ante from the original ACT contract, which totaled $300 million to six companies. While the original contract was a full-and-open competition, whose awardees included large companies such as CACI and L-3 Services. ACT 2 became a small business set-aside contract, although three of its awardees–Assured Information Security, Global InfoTek and Radiance–also were part of the original program. AFRL received 22 bids for the ACT 2 contract.
ACT 2
ACT 2 was a five-year, $950 million dollar ceiling, indefinite-delivery/indefinite-quantity (IDIQ) contract vehicle to research, develop, and integrate cyber solutions to address emerging requirements for the Air Force and its mission partners. Under ACT 2, the companies were contracted to conduct rapid development, design, prototyping, demonstration, scenario development, experimentation and evaluation, integration, testing, technical installation, and transition of cyber technologies.
These technology focus areas include: cyber threat avoidance and cyber defense; full spectrum cyber operations; cyber network exploitation; cyber situational and mission awareness; cyber infrastructure; cyber command and control; information network modeling, simulation, and war-gaming; and cyber mission assurance.
“A review of the previous market research under ACT and ACT 2 in addition to the ongoing market research throughout the current contract has provided adequate justification for ACT 3 to be a total [small business set-aside],” the notice stated. An initial draft request for proposals is expected to be posted in early August. The notice has stated that that contractors would need top-security clearances.
ACT 2 Awards
The Air Force has awarded five small businesses contracts that could top out at $950 million for the rapid development of new cyber capabilities. This contract continues an effort by the service, and the Department of Defense overall, to keep up with potential adversaries in the fast-changing cyber domain.
The five-year, Indefinite Delivery, Indefinite Quantity contract, which has a shared ceiling, was awarded under the Air Force’s Agile Cyber Technology 2 program. The companies will work with the Air Force Research Laboratory–AFRL–on the rapid research and development, prototyping, demonstration, evaluation, and transition of new cyber capabilities.
The five companies on the contracts are:
- Global InfoTek
- Radiance Technologies
- Assured Information Security
- CNF Technologies
- Invictus International Consulting
CNF Awarded US Air Force Agile Cyber Technology 2 Contract
In April 2018, CNF Technologies announced the award of the Air Force Research Laboratory (AFRL) Agile Cyber Technology 2 (ACT 2) contract, a multiple-award Indefinite-Delivery/Indefinite-Quantity (IDIQ) contract servicing Cybersecurity customers across the United States Department of Defense and Intelligence Community.
ACT 3
The U.S. Air Force has announced the third iteration of its Agile Cyber Technology (ACT) contract vehicle at an approximate value of $1 billion, open to small businesses, FedScoop reported in July 2020. “In order to receive from Industry the most novel and innovative approaches to solving user needs, it is anticipated that 4 to 6 Prime contractors are necessary under ACT 3,” the notice said. “Large Businesses are still encouraged to partner with SB.”
The Air Force Research Lab (AFRL) recently published a pre-solicitation notice for the ACT 3 contract, noting that it will expedite cybersecurity research and development. Under ACT 3, AFRL has requested a variety of technologies to enhance federal cybersecurity capabilities, including cyber threat avoidance, full-spectrum cyber operations, network exploitation and situational and mission awareness technologies. Contractor my deliver solutions in the form of hardware, software, technical documentation and technical reports.
The ACT 3 program will emphasize enabling technologies for user requirements; prototype technologies for evaluation in an operational environment; and ways for the Air Force to buy limited product quantities necessary for operational introduction. Technical requirements will encompass rapid development, design, prototyping, demonstration, scenario development, experimentation and evaluation, integration, testing, technical installation, initial operations and cyber technologies.
The Air Force will also contract technology to help it achieve mission success are cyber command and control, wargaming and cyber infrastructure.
US Air Force seeks research to boost operational technology’s cybersecurity in July 2020
A U.S. Air Force cyber systems unit is asking industry to research and develop operational technology solutions for missions in cyberspace. The Air Force Life Cycle Management Center’s Cryptologic and Cyber Systems Division posted a request for information online July 21 seeking “system development lifecycle support and/or component technology research and development for a wide range of OT [operational technology] in support of on-going and emerging cyberspace operations.”
Responses are intended to help the service plan for a related acquisition and contracting strategy.
The Air Force noted that operational technology encompasses a wide variety of systems, including industrial control systems, supervisory control and data acquisition systems, the industrial Internet of Things, wired and wireless telematics, and the IT tech on which cyber operations rely.
The notice stated that responses should include a statement of available capabilities that relate to operational technology cyber solutions to support defensive and/or offensive cyber operations. Specifically, the notice stated emphasis should be placed on three areas:
- Engineering analysis and vulnerability research of operational technology relevant to specific user requirements.
- Design, exploitation, development, testing, delivery and integration of operational technology cyber solutions in the context of the user’s operational environment.
- Provision of a mechanism for user acquisition of limited product quantities.
- The Defense Department has placed increasing importance on the need for operational technology cybersecurity, especially for defensive purposes, after preceding with a focus on IT.
This year, U.S. Cyber Command’s keystone training exercise that took place in June focused on the defense of an air base’s critical infrastructure to include industrial control systems, the power grid, air traffic control radars and electronic access control systems. The attacks came in the form of malware that targeted devices responsible for fuel and power.
 International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis