With the age of quantum computing drawing ever-closer, traditional encryption methods are at risk. While brute force attacks can take months to break through security, quantum attacks can use more advanced techniques to break standard public key cryptography in a much shorter timeframe.
Quantum cryptography is an emerging technology in which two parties may simultaneously generate shared, secret cryptographic key material using the transmission of quantum states of light. A unique aspect of quantum cryptography is that Heisenberg’s uncertainty principle ensures that if Eve attempts to intercept and measure Alice’s quantum transmissions, her activities must produce an irreversible change in the quantum states that are retransmitted to Bob. These changes will introduce an anomalously high error rate in the transmissions between Alice and Bob, allowing them to detect the attempted eavesdropping.
QKD provides a method of provably secure communication. Many QKD systems, including commercial systems, have been developed during the last 30 years, and important elements such as secret key rates and maximum transmission have continuously improved. QKD is suitable for use in any key distribution application that has high security requirements including financial transactions, electoral communications, law enforcement, government, and military applications.
However there is an increasing understanding that the security of a QKD system relies not only on theoretical security proofs, but also on how closely the physical system matches the theoretical models and prevents attacks due to discrepancies. These side channel or hacking attacks exploit physical devices which do not necessarily behave precisely as the theory expects. As such there is a need for QKD systems to be demonstrated to provide security both in the theoretical and physical implementation.
Researchers have proposed secure protocols such as Device Independent (DI) QKD and Measurement Device Independent (MDI) QKD. Measurement-Device Independent Quantum Key Distribution (QKD) promises secure digital communication, ultimately worldwide, that cannot be broken – not even by a quantum computer. Quantum technology research group QuTech and Dutch bank ABN AMRO have announced a partnership to develop Measurement-Device Independent Quantum Key Distribution (MDI-QKD) and will use it to address the security challenges posed by super-powerful quantum computers, first apply it to the banking industry. TU Delft, TNO, and ABN AMRO have said they will be demonstrating a secure, quantum-based data connection at the end of next year ( 2020).
However researchers have also found that quantum communication protocols cannot guarantee security alone, but will always have to be supported by additional technical countermeasures against laser damage.
Discrete Variable QKD System
The discrete variable (DV) approach to QKD has been extensively studied, and most of the testbeds and available commercial devices are of this kind. The underlying idea is that since it is well-known that in quantum mechanical systems any measurement perturbs the system, this feature can be exploited to understand if someone is trying to steal data from the channel.
BB84 is an example of discrete variable quantum key distribution (DV-QKD), where a finite number of polarization bases are used to encode bits. The sender (Alice) generates a random bit (i.e.,either a “0” or a “1”) and encodes it in one of two different bases, over a given physical parameter of a photon (typically, polarization). The first basis is used to encode “0” bits and the second base for “1” bits. Since the receiver (Bob) does not know the sender’s basis selection, he measures (after propagation in an optical fiber link) the polarization of the incoming photons by randomly using one of the two possible bases.
If he uses the same base as the sender, he will measure the correct bit value; conversely, if he chooses the wrong base, the result of the measurement will give the correct result only with 50% probability. After a long sequence of photons has been exchanged, Alice and Bob compare the bases they have employed to encode and measure each photon, respectively, by communicating via a classical channel. They keep only the bits generated and detected with a matched base, which are said to constitute the sifted keys. In an ideal system without noise, imperfections, and disturbances, the sifted keys are identical and can be used as a private key.

Typically, the two polarization bases used by the sender are selected by a polarizer and are rotated 45◦ about each other. They are called rectilinear (0◦ , 90◦ ) and diagonal (45◦ , 135◦ ) bases. At the receiver, a polarization beam splitter (PBS) transforms the polarization encoding into a spatial encoding, so that the photons can be detected using two separate photon avalanche photodetectors (SPAD).
Starting from the BB84 protocol, many variants of QKD protocols have been proposed over the years, but the basic concept has remained the same. In 1991, the E91 protocols were proposed. This system is similar to BB84 but it uses entangled photons to guarantee the security of the communication, relying on the no-cloning theorem proven by Wooters in 1992. E91 still uses the polarization to encode information and the same BB84 mechanism to statistically detect an eavesdropper. Entangled photon pairs are distributed among communicating partners, which choose a measurement basis; if two partners choose the same basis, the measured bit will be equal, otherwise the bit is discarded.
Continuous Variable Systems
DV-QKD systems require ad-hoc devices to operate, such as single-photon detectors and single-photon sources. This is a major obstacle to industrialization due to small production volumes (at least during the initial phases of introduction on the market_ and the need to setup a dedicated supply chain. Moreover, the efficient generation, detection, and manipulation of individual photons require cryogenic refrigerated devices. One decade later than the introduction of DV systems, an alternative approach to QKD was proposed. It is named the continuous variable (CV) approach, since photon parameters assuming continuous values are used.
Quantum Security and Practical Vulnerability Issues
QKD protocols are known to be unconditionally secure because their security is independent of the amount of information and the computational power of the attacker. However, this statement is true for an ideal system. In practice, as is shown in, several assumptions have to be satisfied for the system to be considered unconditionally secure.
For example, due to its limited bit rate, QKD is often used in conjunction with classical encryption methods, making the actual security dependent on the technological level of the adversary at the time of the key exchange. Another example of a technological issue is the possible information leakage caused by light emitted by avalanche photodiodes during the breakdown. Moreover, QKD may be vulnerable to beam splitter and trojan horse attacks due to the non-ideality of photon sources and backscattered light, respectively, requiring proper design countermeasures.
Current QKD systems cannot meet the theoretical security of the original QKD protocol, leading to security issues with the systems, called ‘quantum hacking,’ with much work with these issues being done at the Quantum hacking lab, led by Dr. Vadim Makarov. The most critical vulnerability is that current technology and hardware does not meet the conditions specified in the QKD protocol. These hardware ‘non-idealities’ include on-demand single photon emitters, lossless photonic channels between sender and receiver, perfect photonic detectors, and perfect alignment of bases throughout the system, says Jeffrey Morris who serves as the Sergeant Major of the Army Cyber Institute.
In the classical communication systems, the security-critical parts can be physically separated from the communication channel, thus making them isolated from physical access and alteration by the eavesdropper. However, the front-end of a quantum communication system is essentially an analog optical system connected to the channel, and easily accessible by an eavesdropper. The latter may shoot a high-power laser from the communication channel to damage a security-critical component of the system, rendering the system insecure.
Researchers at the Massachusetts Institute of Technology (MIT) have taken advantage of a phenomenon known as “photon entanglement,” wherein a single photon has two interdependent states. By measuring one state they were able to accurately forecast the other state and decode a photon cipher without alerting the receiving photon detector that it been hacked.
The network could also be subjected to false alarms, due to certain conditions photon detector might have failed to register the initial arrival of a photon, leading users to assume they’re being hacked when, in fact, nothing adverse has occurred.
Other issues with current QKD systems are their slow key generation rate and limited range. The “unconditionally secure” system needs one bit of key for each bit of data, but current QKD systems generate key material far too slowly for this form of encryption.
It is also possible to jam quantum network by blinding a photon detector with a strong pulse, that could present an opportunity to hack photons the user is not aware are arriving. Researchers have experimentally demonstrated a class of attacks based on laser damage , capable of creating new security loopholes on-demand. They performed laser damage on two completely different widely used implementations: a commercial fiber-optic system for QKD and coin-tossing with phase-encoded qubits and a freespace system for QKD with polarization-encoded qubits.
Thus In practice, quantum networks has its vulnerabilities which researchers need to address before it can be claimed that they hack proof. As QKD-based systems get more and more deployed, testing those systems becomes more and more important.
In both systems, the damage opens up a new side-channel, which can compromise the security of QKD. “While we have demonstrated c.w. thermal laser damage on the timescale of seconds, short-pulsed laser radiation may induce different damage mechanisms. Furthermore, systems can be attacked in both powered and unpowered state (e.g., during an outage or maintenance).
Hacker proof QKD systems
A consistent research effort has been devoted to the necessity of achieving unconditional security in practice and to engineering the known protocols for this purpose. For example, single-photon sources implemented by attenuating standalone lasers (a usual choice, due to practical feasibility issues) are vulnerable to a kind of attack called photon number splitting (PNS). Such non-ideal sources may emit multiple photons instead of exactly one, and these may be used to split the additional photons and extrapolate information without affecting the photons exchanged by “Alice” and “Bob”. A solution aimed at solving source imperfections in BB84 was proposed by Hwang , where additional states, called decoy states, are properly designed to be different in power in respect to the data photons and are randomly substituted into the data to understand if someone is sniffing the channel. An unconditional security proof of decoy-state QKD is shown in .
Decoy states were exploited by Gisin et al. in 2004 to obtain a specific protocol, called the coherent one-way (COW) protocol. Instead of using ideal single-photon sources, which are hard and costly to realize and require cryogenic temperatures, this protocol uses a continuous wave laser as the source, such as the ones used in optical telecom systems. This laser is attenuated to obtain quasi single-photon transmission. Since the optical generation of photons is a statistical process, the number of actual generated photons will be either zero, one, or several photons. The bits are encoded into the arrival times of consecutive pulses, where an empty state followed by a coherent state represents a “0” bit, while the opposite order represents a “1” bit. The decoy states used to prevent PNS attacks are instead represented by consecutive coherent states. This protocol was tested over more than 300 kms.
Quantum key distribution with hacking countermeasures and long term field trial in 2017
Researchers from Toshiba Japan and Quantum ICT Laboratory, have designed a QKD system providing a more resilient target against possible hacking attacks including Trojan horse, detector blinding, phase randomisation and photon number splitting attacks. The QKD system was installed into a 45 km link of a metropolitan telecom network for a 2.5 month period, during which time the system operated continuously and distributed 1.33 Tbits of secure key data with a stable secure key rate over 200 kbit/s. In addition security is demonstrated against coherent attacks that are more general than the collective class of attacks usually considered.
The system is based around the well-known decoy state BB84 protocol and uses phase encoded optical pulses with sub single photon intensities to transmit the quantum information. The QKD system implements an automated initialisation and alignment routine which enables key distribution to begin operating within several minutes of a cold start, with no user input or adjustment required.
The system additionally implements component monitoring for both security and reliability, as well as refined stabilisation subsystems to provide consistent operation under harsh operating conditions such as those experienced during transmission through aerial fibre cables. A web browser based graphical user interface is also implemented to allow for user friendly control and monitoring of the system and all security and component subsystems. The system operates at a 1 GHz transmission clock rate, with photon detection using self differenced19 InGaAs/InP avalanche photodiodes (APDs).
Optical countermeasures consisting of attenuators (A), isolators (I) and spectral filters (F) are placed after the interferometer to provide a quantitatively analysed resistance to the Trojan-horse attack. In outline a bound is placed on how much light an eavesdropper can input before fibre damage occurs, and based on the characterised system reflectivity this places a bound on the reflected light intensity. This can then be used in a modified security proof to remove any information gained by the eavesdropper in this way. Approximately 170 dB of isolation is provided by the optical countermeasures.
The transmitter’s laser diode temperature and output power is continuously monitored to ensure it is in the correct operating regime, and the system output power is constantly monitored and kept stable using the automated variable optical attenuator (A).
To provide an initial guard against potential APD blinding attacks the input optical power is monitored at the receiver. In addition the APD module’s temperature is also continuously monitored for any anomalies, which will further constrain possible hacking attacks. The receiver unit is protected from Trojan horse attacks against the phase modulator through the internal fibre length and the propagation delay it introduces combined with the GHz modulation clock rate. This removes the possibility for Eve to receive any reflected light from the phase modulator before the modulated photon has been detected by Bob due to the photon time of flight.
Measurement Device Independent (MDI) QKD
One possible way to remove side-channel information is to reduce the theory assumptions on a QKD implementation. This is exemplified in Device Independent (DI) QKD, which can provide an information theoretic secure key even if the physical quantum devices used in the protocol are not trusted to behave as expected. “While progress in the theory has been underway, laboratory experimental demonstrations remain a challenge due to amongst other things the requirement for a loophole free Bell test. Even with experimental progress the secret key rate is anticipated to be extremely low, on the order of 10−10 bits per pulse, and only possible over very limited distance,” write Dixon and others.
A more feasible proposal is Measurement Device Independent (MDI) QKD where the detector units are untrusted but the transmitters must be trusted as in standard QKD. MDI-QKD can remove all of the detector based side-channel attacks but still remains vulnerable to source based attacks.
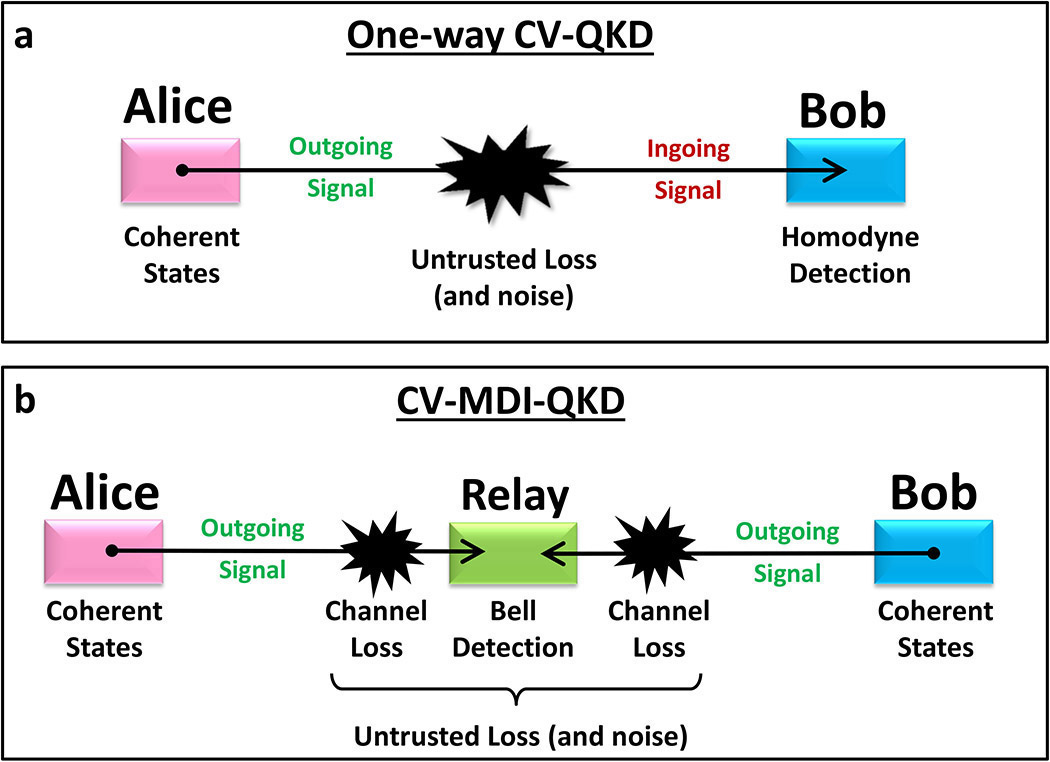
It has been experimentally demonstrated in several recent papers, including outside of the laboratory in a field trial environment. However there remain challenges, including the difficulty of synchronising and interfering two phase randomised independent sources separated by large distances, especially at the clock rates used by modern conventional QKD systems. “This typically limits the secure key rate to values much lower than conventional QKD in practical scenarios, despite a recent laboratory proof of principle demonstration of high bit rate MDI-QKD. Additionally MDI-QKD uses a three party configuration, which is not as straightforward to integrate into existing communication infrastructure,” write Dixon and others.
Similarly, there is no guarantee that the measurement-device-independent and fully-device-independent QKD implementations cannot be altered by laser damage (potentially breaking the assumptions of a trusted source in the former and the absence of information-leakage channels in the latter). Any alteration of characteristics might compromise the security either directly by leading to an attack, or indirectly by shifting some parameter in the security proof so it would no longer apply.
Countermeasures to the laser-damage attack may include a passive optical power limiter, a single-use ‘fuse’ that permanently breaks the optical connection if a certain power is exceeded, or battery-powered active monitoring supplemented with wavelength filtering. Another promising technique is “hardware self-characterization,” which sort of just means that some additional system is in place to monitor the key-generation device physically.However to protect from an arbitrary damage it must monitor a potentially large number of hardware parameters. Any countermeasure must be tested in all possible illumination regimes.
Secure and Cost effective quantum moves a step closer with MDI-QKD system
Canadian and US researchers have taken an important step towards enabling quantum networks to be cost-effective and truly secure from attack. The experiments, by the team from the University of Calgary, the California Institute of Technology and the National Institute of Standards and Technology, Colorado, prove the viability of a measurement-device-independent quantum key distribution (QKD) system, based on readily available hardware.
The team’s results, published in the journal Quantum Science and Technology, shows how they employed cost-effective and commercially available hardware such as distributed feedback (DFB) lasers and field-programmable gate arrays (FPGA) electronics, which enable time-bin qubit preparation and time-tagging, and active feedback systems that allow for compensation of time-varying properties of photons after transmission through deployed fibre.
The first author Raju Valivarthi said: “Quantum hacking over the past decade has also shown, however, that the specifications of components and devices used in actual QKD systems never perfectly agree with the theoretical description used in security proofs, which can compromise the security of real QKD systems. For instance, so-called ‘blinding attacks’ exploit vulnerabilities of single photon detectors (SPDs) to open a side-channel, via which an eavesdropper can gain full information about the (assumed-to-be) secure key. Making practical QKD systems secure against all such attacks is a challenging task.”
Senior author Dr. Qiang Zhou said: “Our MDI-QKD system includes four parts: qubit preparation module, Bell state measurement (BSM) module, control module, and time-tagging module, which allows key generation from qubits in randomly prepared states. It is worth to note that our control module in the demonstration is further improved to control the polarisation and arrival-time of photons travelling from Alice and Bob to Charlie, which ensures their indistinguishability at the moment of the BSM.”
Group leader Professor Wolfgang Tittel said: “Our experimental demonstration paves the way for MDI-QKD-based star-type quantum networks with kbps secret key rates spanning geographical distances of more than 100km.”
In august 2020, Researchers demonstrate long-distance QKD with measurement-device-independent protocol
In an important step toward practical implementation of secure quantum-based communication, researchers have demonstrated secure measurement-device-independent quantum key distribution (MDI-QKD) transmission over a record-breaking 170 kilometers. QKD can offer impenetrable encryption by using the quantum properties of light to generate secure random keys between users for encrypting and decrypting online data. The measurement-device-independent QKD protocol is among the most secure and practical because it is immune to attacks directed at the detection devices that measure the quantum properties of individual photons.
Although QKD has been demonstrated over relatively long distances, it has been difficult to accomplish this with high transmission rates while maintaining security. To overcome this challenge, Wang developed a new MDI-QKD transmission protocol that uses photons with three characterized quantum states to encode data.
The standard MDI-QKD protocol can resist all potential detection loopholes; unfortunately, it still assumes perfect state preparation that can be a great challenge in practice. To protect against state-preparation imperfections, some countermeasures have been put forward. Yin et al. proposed a method called MDI-QKD with uncharacterized sources by incorporating mismatched-basis data that are normally discarded from the calculation of phase-error rate. Based on Yin and other people’s work, the research team developed a practical scheme, where not only an improved phase estimation method, but also a simple three-state scheme is implemented to obtain substantially enhanced performance compared with other uncharacterized-source or loss-tolerant MDI-QKD schemes.
Using a state-of-the-art experimental setup for encoding and detection, the researchers showed that the new QKD approach could transmit keys over longer distances and at higher rates (10-7 /pulse key rate) than other similar measurement-device-independent QKD protocols. Theoretical calculations showed that secure transmission could be possible over distances up to 200 kilometers. The present work can be further developed by incorporating either the highly efficient decoy-state method or the new proposed twin-field QKD protocols.
Singapore researchers developing chip-based quantum crypto devices to enhance network encryption, reported in June 2020
A team of engineers and researchers are working to tap quantum cryptography technology to enhance network encryption tools, so these can be ready to mitigate security risks when quantum computing becomes mainstream. ST Engineering and National University of Singapore (NUS) will use “measurement-device-independent” quantum key distribution (MDI QKD) technology in their efforts to to build cybersecurity defence against increasingly sophisticated threats.
Supported under National Research Foundation’s Quantum Engineering Programme, the partnership aims to make advanced quantum cryptography accessible to the wider industry and drive the advancement of a technology that can lead to a new class of “quantum-resilient encryptors”, the partners said in a joint statement Friday.
They added these encryptors provided a highly scalable and cost-effective tool that could be deployed with minimal disruption to existing digital infrastructure. “This addresses the current limitations in the market [where] products are designed for point-to-point communication and are not scalable,” they said. “This will also accommodate a larger number of users and benefit numerous applications, from financial services institutions, to government agencies, and hospitals.”
ST Engineering’s president of cybersecurity systems group, Goh Eng Choon, said: “The threat landscape is evolving very rapidly and we must be prepared for challenges to come in the post-quantum computing era. While QKD technology can be used to secure digital communications, it can also be used to mitigate future quantum computers being used to exploit and maliciously target weak links and disrupt the global encryption ecosystem.
“This research into quantum cryptography and the co-development of the industry’s first solution will allow us to explore the potential of this technology, further strengthen our arsenal of advanced cybersecurity solutions, and gain a foothold in the QKD market,” Goh said. NUS currently is working with nanoelectronics institute companies to jointly develop new chip-based quantum crypto devices, which can be applied to the new MDI-QKD technology and broader quantum cryptography technology due to their smaller device footprint and lower cost.
NUS’ assistant professor Charles Lim Ci Wen, who leads the joint project with ST Engineering, said: “As quantum computing becomes more prevalent worldwide, information security threats will also become more advanced. This collaboration, which leverages MDI-QKD, will lead to quantum-resilient encryptors that are not only secure against channel attacks, but also against detection side-channel attacks.” Lim added that the partnership would explore how chip-based quantum devices could be integrated into commercial network encryption equipment, hence, reducing the cost of QKD technology.
References and Resources also include:
 International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis



