The life sciences now interface broadly with information technology (IT) through its industrial applications in health care, agriculture, manufacturing, automation, artificial intelligence, and synthetic biology. The information moves between living and cyber systems in a two-way flow.
Global public health crises create conditions of extreme fragility where dual-use technologies can be harnessed to increase insecurity. As mentioned by the UN Secretary-General In his address to the Security Council, “The weaknesses and lack of preparedness exposed at the time of pandemic provide a window onto how a bioterrorist attack might unfold – and may increase its risks. Non-state groups could gain access to virulent strains that could pose similar devastation to societies around the globe.”
The current pandemic provides states and terrorist groups with a real-time window into societies’ strengths and weaknesses in emergency situations. The past months have shown how a biological threat could break down hospitals and food supply chains, shatter citizens’ trust in critical information and public institutions, and bring social unrest, disinformation, even violence. Additionally, malicious actors’ capacity to access cloud-labs could automate the design of pathogens with multidrug resistance or reproduce a strain similar to COVID-19. Both could be easily spread in public spaces using drone technologies.

These converging security risks have corrosive implications for every country, but particularly those that have poor and outdated medical, biotech and cyber-infrastructure or who don’t have the capacity to protect their vulnerable populations from the weaponization of pandemic and technological threats.
Conflict-affected states, when facing converging security threats, suffer crises unprecedented in magnitude, mortality and scope. These states are less able to prepare for low-probability, high-impact events at a time of public health emergency, and will be less resilient should one materialize. In a country where critical infrastructure is already failing, for instance, a cyberattack on medical facilities or connected electrical grid could be devastating. Even in wealthy countries cybercriminals have targeted hospitals and digital networks during the COVID-19 crisis, scaling up social engineering strategies to prey on people at a vulnerable time.
Cyberbiosecurity threats and Vulnerabilities
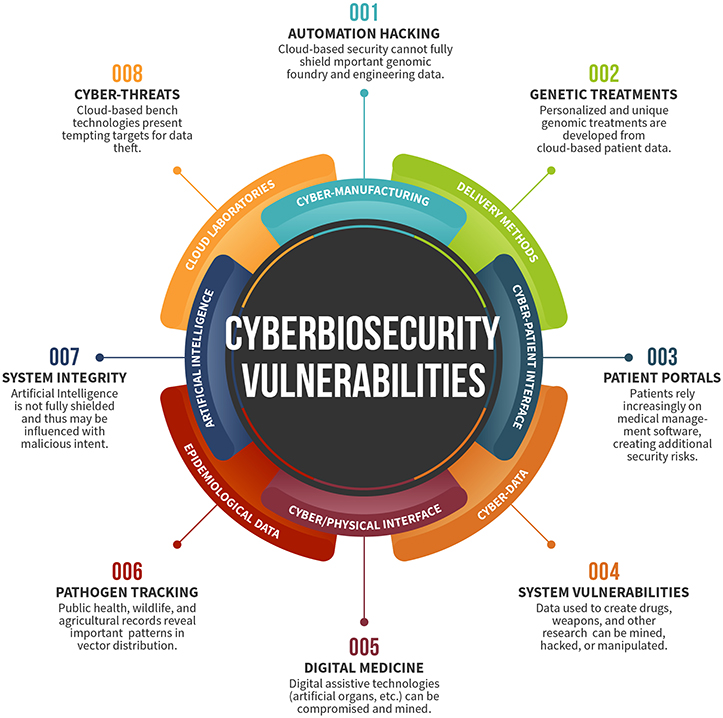
As the information and handling mechanisms for biological materials have become increasingly digitized, many market sectors are now vulnerable to threats at the digital interface. This growing landscape will be addressed by cyberbiosecurity, the emerging field at the convergence of both the life sciences and IT disciplines.
Cyberbiosecurity threats are becoming increasingly important as technological progress continues to accelerate in fields such as artificial intelligence, automation, and synthetic biology. Moreover, not only is the pace of progress in these fields accelerating, but they are also becoming increasingly integrated, leading to a growing overlap that is generating new security vulnerabilities.
Fundamental decisions related to human health are being handled computationally. While doctors are ultimately charged with most final decisions, precision medicine fundamentally relies on pipelines that from extraction, to sequencing, to variant-calling, to genotype determination, never leave a computational environment. These systems must be secure. As sequencing replacing more straightforward human-driven medical and genetic tests, it is critical that these pipelines are not open to manipulation.
Some of the risks identified are the theft, elimination or ransom of data, algorithms, or software with a direct or indirect impact on R&D or commercial operations. The modification of data, algorithms, or software with a direct or indirect impact on research and development or commercial operations. The loss of intellectual property or commercial advantage by data, algorithms, or software being available to competitors.
A 2019 hearing of the commission, titled ‘Cyberbio convergence: characterising the multiplicative threat’, raised issues such as the vulnerability of pathogen and biomanufacturing systems, biological risk mitigation, and the vulnerability of intellectual property in the national and global bioeconomy.
Artificial Intelligence
Industry interest in artificial intelligence (AI) has experienced a resurgence in recent years due to increased computing power, advancing applications of neural networks, and an emergence of new machine and deep learning techniques across the biology sector. Biotechnology companies are successfully utilizing these developments for drug design and development, genomics, evolutionary biology , protein folding, and more.
This rapid and evolving interest in the landscape of new AI technologies has led to emerging threat domains related to information privacy and storage, ownership over biological and genetic data, and applications of powerful technologies (Pauwels, 2018). These issues are not new, as bioinformatics and digitization have created a potential target; however, the popularization of AI has refreshed these concerns in the modern zeitgeist.
Finally, core bioinformatic operations, from imaging, to sequence assembly and alignment, to
protein folding have benefited from higher accuracy and higher throughput, by implementing deep learning. These methods benefit from large datasets and can often exceed the performance of state of the art in algorithmic development. However, deep learning approaches are typically and notably resistant to audit and interpretation. It is also difficult to scrutinize imported models prior to their use. This makes them particularly prone to adversarial manipulation and presents in internal security threat to users.
In 2018, a malicious attack was designed to hack hospital CT scans, generating false lung tumours that conformed to a patient’s unique anatomy, leading to a misdiagnosis rate in excess of 90%. Furthermore, researchers at Harvard University tested adversarial attacks against algorithms used to diagnose skin cancer images, demonstrating that such attacks required only modifying a few pixels in the original biopsy picture to corrupt a diagnosis. These examples are just a sampling of how AI can automate the manipulation of medical datasets, expanding a cyberattack’s impact through health and biotech industries. Those attacks exist in an era of hybrid security risks where pandemic threats converge with the weaponization of powerful dual-use technologies.
There is a renewed opportunity for life science and cybersecurity professionals to design and implement frameworks to facilitate responsible application of AI techniques to biology.
Automation
The convergence of robotics, machine learning, and artificial intelligence has paved the way for automated approaches to biology, manufacturing, software development, accounting, and more. Improved biological engineering techniques and robotics have converged to result in rapid prototyping and higher yields. Laboratories are increasingly using robots to improve throughput and free up the hands of laboratorians around the world (McGee, 2014; Szesterniak, 2014).
As robots are increasingly connected to networks and other electronic systems, new cyberbiosecurity concerns unique to automated laboratory environments are beginning to emerge. Virtual environments allow access to infrastructure within the physical world; this creates a vulnerability that would permit unauthorized remote access to an automated biological manufacturing system. As automation increases within the life sciences, so too will potential vulnerabilities to threat.
For example hackers could Manipulate bio-manufacturing or automated systems to create risks. There is also Potential for the disabling or disruption of important systems or infrastructure leading to disruption of commercial operations or impeding good manufacturing practices;
Synthetic Biology
The term “synthetic biology” is widely used to describe activities carried out by scientists in a variety of disciplines, from bioengineering, chemistry, biochemistry, and materials science to cellular and molecular biology. Today, engineers, biologists, technologists, and citizen scientists have turned this field into a true discipline. Systems engineering techniques are being applied to organisms to design genetic circuits, novel molecules, and commodities such as fuels, electricity, feed, and renewable materials. Simultaneously, the design-build-test approach traditionally used in product development is rapidly emerging in organism engineering.
Similarly, fundamental operations in synthetic biology, from sample intake and sample tracking
through device orchestration, through testing, validation and verification that are increasingly being automated. There are fundamental economic, quality and safety drivers that motivate this growing field toward automation. Concrete problems that emerge in synthetic biology as humans move out of the loop and major portions of the bioeconomy become reliant on automated systems.
Advancements in synthetic biology will have a significant impact on cyberbiosecurity as laboratory automation techniques become more widespread and the traditional cost barrier for scale-up of production is lowered. Similarly, the convergence of robotics, microfluidics, cell-free systems design and synthetic metabolic engineering stands to create new cyberbiosecurity risks and unique threat domains. As these fields further develop and converge, revealed vulnerabilities will offer new opportunity for exploitation.
Digitization of Traditional Technology
The expanding digitization of the biological sciences places greater value on the data generated, information extrapolated and knowledge gained. Failing to protect data will affect a company or country’s ability to position itself optimally in the forthcoming fourth industrial revolution. Further, more reliance on automation, distribution, and outsourcing in biotechnology makes its infrastructure a target. The equipment and service providers that drive physical research and development are also all connected online.
This is enhancing the risk of Cyberattacks on vaccine manufacturing supply chains, hospitals and digital stores of genomic data. Failing to protect these resources from intrusion increases the risk of accidental or deliberate harm, for example by the loss of control over biological products. Robust cybersecurity measures are therefore critical for both securing the data generated by the biotechnology sector as well as securing key infrastructure.
Manufacturing
While the risks relating to accessing private biomedical data and the theft of valuable data from an intellectual property standpoint are well-known and recognized, the biosecurity implications of cyber intrusions relating to biotechnology infrastructure remain largely unknown in commercial biotechnology facilities.
Science and technology-reliant organizations are becoming more complex and networked throughout facilities, supply chains, logistics, and transport mechanisms. Distributed manufacturing employs decentralized production networks linked by information technology; as more connections between traditionally isolated systems are developed, more security controls must be considered in order to mitigate risks and reduce vulnerabilities. The production processes and assemblies of biologics and other materials can also be distributed and carried out asynchronously at geographically different locations, allowing response to potential threats to be developed in situ.
In addition to facilitation of distributed manufacturing techniques for traditional life sciences operations, recent advances in cell-free metabolic engineering technologies allow for higher throughput in production environments. This has resulted in improved biological techniques for rapid prototyping and higher yields. Cell-free biological systems are being used to develop commodities such as fuels, electricity, feed, and renewable materials (Rollin et al., 2013). As the convergence of dichotomous technical disciplines (e.g., automation and cellular biology) continues to expand rapidly, it is increasingly important that the fields of cybersecurity and biosecurity converge to address inherent digital and biological concerns.
Biomedical Sciences
Cybersecurity and health security converge with increasing digitization of health data. Regulatory mechanisms are in place to address concerns regarding privacy and confidentiality of medical and billing information; however, this extends beyond the cyber-patient interface in the context of electronic medical records. Patient treatment management—including potential drug interactions, protocols, and sensitivities specific to the patient—is increasingly digitized.
Personalized medicine diagnostics and therapeutics are rapidly expanding, and much of the information associated with these interventions is maintained digitally. Biomedical data breaches are not without historic precedent: in 2014, data breaches of three major health systems resulted in unauthorized access to millions of patient records, including clinical data (Kozminski, 2015).
These breaches provided the perpetrators valuable clinical data, which could be used internally or sold for monetary gain. In addition to facilitating illicit data collection, disruption of digitally-programmed diagnostic testing systems or therapeutic targeting fields could result in ineffective treatment. Medical devices are also an area of interest in cyberbiosecurity, as many potential exploits could be leveraged through direct and indirect interfaces with the patient and manufacturer (Khera, 2017).
Agriculture
Throughout much of the world, food and beverage safety and security is a high priority. Concomitantly, the economics, societal robustness, and security implications of agriculture, foodstuffs and beverages are massive. Extensive quality measures are in place to prevent and mitigate threats from manifesting; outbreak and contamination detection and response systems react when problems are noticed. Packaging and labeling methodology have also been improved.
However, agriculture and consumables in many countries rely on cyber-enabled systems for many aspects of farm management, production-to-consumption, raw materials to finished product, and logistics (Security Security DoH., 2018). The health and security of this dimension of agriculture and food systems is unclear from a cyberbiosecurity perspective. We reason that vulnerable critical links and nodes exist throughout this highly complex global and national ecosystem; attention to cyberbiosecurity measures is warranted and would be considerably beneficial.
Cyberbiosecurity
The combination of medical data-manipulation and cyberattacks on bio-manufacturing could have drastic economic consequences and lethal outcomes for populations. Yet the most enduring harm would be on citizens’ trust – trust in public health institutions, emergency data-systems, laboratories, hospitals and critical infrastructures.
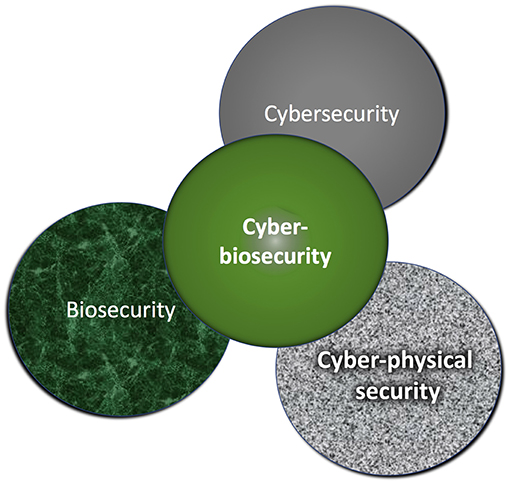
Cybersecurity encompasses the protection of computer systems from theft and damage to their hardware, software, or information, as well as from disruption or misdirection of the services they provide. Biosecurity involves securing valuable biological material from misuse or harm. The new discipline of cyberbiosecurity has been created to bring together disparate communities to identify and address a complex ecosystem of security vulnerabilities at the interface of the life sciences, information systems, biosecurity, and cybersecurity (Murch et al., 2018; Peccoud et al., 2018); it serves as a lens for observation that relies on disciplinary integration.
Cyberbiosecurity cuts across disciplines; impacting fields from laboratory science, to human and animal health, agriculture, and environmental health and ranging from protection to management and remediation. Technology integration is the new norm, with novel technology improvements and simple digitization bringing easy access to old systems, such as medical records. As technical disciplines develop at an exponential pace and their convergence accelerates, it is becoming increasingly clear that the fields of cybersecurity and biosecurity must also converge in order to address inherent digital and biological concerns. Further, technological convergence meets the decreasing cost for access at the Do It Yourself (DIY)/community biology space.
The objective of cyberbiosecurity has been described as addressing “the potential for or actual malicious destruction, misuse, or exploitation of valuable information, processes, and material at the interface of the life sciences and digital worlds”. Cyberbiosecurity is part of a system of measures that collectively aim to “Safeguard the Bioeconomy”, an objective described by the National Academies of Sciences, Engineering and Medicine of the United States
Today arbitrary synthetic DNA can be ordered online and delivered within several days. In order to regulate both intentional and unintentional generation of dangerous substances, most synthetic gene providers screen DNA orders. A weakness in the Screening Framework Guidance for Providers of Synthetic Double-Stranded DNA allows screening protocols based on this guidance to be circumvented using a generic obfuscation procedure inspired by early malware obfuscation techniques.
Furthermore, accessibility and automation of the synthetic gene engineering workflow, combined with insufficient cybersecurity controls, allow malware to interfere with biological processes within the victim’s lab, closing the loop with the possibility of an exploit written into a DNA molecule. One type of cyberbiological attack, under which unwitting biologists may be tricked into generating dangerous substances within their labs.
Genetic Barcodes Can Ensure Authentic DNA Fingerprints reported in May 2020
Engineers at Duke University and the New York University’s Tandon School of Engineering have demonstrated a method for ensuring that an increasingly popular method of genetic identification called “DNA fingerprinting” remains secure against inadvertent mistakes or malicious attacks in the field. The technique relies on introducing genetic “barcodes” to DNA samples as they are collected and securely sending information crucial to identifying these barcodes to technicians in the laboratory. The system shows one way to guarantee that a sample taken in the field, transported to a lab and processed for genetic identification is genuine.
The results appear online on May 14 in the journal IEEE Transactions on Information Forensics and Security. “If you think about conventional encryption techniques, like security for a smartphone, there’s usually a passcode that only one person knows,” said Mohamed Ibrahim, a system-on-chip design engineer at Intel Corporation and recent Duke electrical and computer engineering PhD graduate. “Our idea is to inject non-harmful material into genetic samples immediately when they are collected in the field that act as a similar password. This would ensure that the samples are authentic when they reach the processing stage.”
DNA fingerprinting is a method of identifying a specific person, organism or disease based on only a small amount of genetic material. While about 99.9 percent of the DNA between two unrelated humans is the same, that still leaves around three million base pairs that are different. And within that potentially identifying dataset, certain short segments of DNA sequences are much more likely than others to vary in composition from person to person.
Rather than sequencing a person’s entire genome, which still costs more than $1,000 a pop, scientists can target a handful of these short sequences for identification. In DNA fingerprinting, a technique called polymerase chain reaction (PCR) replicates the genetic sequences at these sites repeatedly so that they can easily be read. Based on the specific combinations of nucleic acids at these various sites, genetic samples can be matched to their sources. While it may seem like data from hundreds of these sites would be needed to make a definitive match, they vary so much from person to person that the Federal Bureau of Investigations currently recommends that only 13 are necessary.
As the popularity of this technique and the PCR technology underlying it increases, multiple companies are in a race to simplify the process and create cheaper solutions. And as these devices become smaller, more complex and more automated, it may create more opportunities to attack the process. Recent studies suggest that these opportunities raise unprecedented security concerns, creating a whole new category of potential weaknesses that has been dubbed “cyberbiosecurity threats.”
“Researchers have identified a diverse array of cyberbiosecurity threats over the past few years,” said Krishnendu Chakrabarty, the John Cocke Distinguished Professor of Electrical and Computer Engineering at Duke. “Our main goal is to become a part of the community trying to address these threats by focusing on one of the most vulnerable time periods, which is before a sample even gets to the lab.”
DNA test that reveals the presence or absence of the genetic barcode added to a DNA sample after being taken in the field. The first set of columns has no barcodes because no primers were used. The second set of columns display the barcodes the laboratory technicians are looking for. The third set of columns matches the second set, indicating a sample is authentic, while the fourth set of columns does not match, indicating something has gone awry with the samples.
In their new paper, Chakrabarty, Ibrahim, Tung-Che Liang, a current doctoral student in Chakrabarty’s laboratory, Ramesh Karri, professor of electrical and computer engineering at NYU Tandon, and Kristin Scott, adjunct assistant professor of molecular genetics and microbiology at Duke, demonstrate the usefulness of a genetic barcode to ensure samples taken in the field are not swapped or otherwise tampered with on their way to the laboratory. Relying on the genetic PCR expertise of Scott and working out of her laboratory, the researchers first added two short stretches of synthetic DNA to genetic samples bound for DNA fingerprinting. Because they are synthetic, they can be made in almost any combination of the four available DNA base pairs imaginable. And at 280 and 190 base pairs each, the chances of correctly guessing the genetic combination is vanishingly small.
“We analyzed the conditions an adversary needs to satisfy to undermine the barcoding system,” said Karri, who is a co-founder and co-chair of the NYU Center for Cyber Security. “These conditions are related to the physical characteristics of the molecular barcode. By linking these conditions back to how barcodes are generated and the expansiveness of the search space, we show that the probability that an adversary can discover the barcode is negligibly low.” Meanwhile, the primers needed to amplify each barcode are sent securely to the technicians in the laboratory. For a PCR machine to repeatedly copy a specific segment of DNA, it first must know how that sequence starts and ends. Primers provide that information, and without it, an attacker would have no chance of amplifying the correct barcodes.
Once the technicians finish an initial PCR run with the samples and primers provided, the two barcodes appear as peaks or lines in the resulting genetic data, depending on the method being used to identify them. To make sure the samples are authentic and not tampered with, the technicians must simply make sure these two barcodes appear as expected. “When the right primers are used to unlock a barcode, you should get a positive result,” said Ibrahim. “If you don’t, then that means that the sample is not genuine. Some sort of switching or alteration has occurred.”
While this system currently relies on information being transmitted securely to the laboratory, the researchers say there are ways that the genetic barcodes could be streamlined into the technology. For example, the barcodes could be correlated in some way to the samples being sent, and technicians could look up the correct primers to use from a database. With the proper hardware, the idea could also conceivably be translated into the chips running the DNA analysis themselves. “This work is an excellent example of multiple disciplines coming together to develop new solutions to existing real-world problems,” said Scott. This research was supported by the Army Research Office (W911NF-17-1-0320) and the National Science Foundation (CNS-183362).
Conclusion
The convergence of recent advances in the life sciences with regard to traditional cybersecurity threats has led to the recognition and identification of vulnerabilities, known as cyberbiosecurity threats.
The survey funded by Biosecure Ltd.was carried out online from October-November 2017. Key findings of the survey showed that cyber-biosecurity risks were considered to be difficult to characterize due to variations in types of threats, targets and potential impacts, and compounded by a notable variation between the level of sophistication or maturity of mitigation and response measures. Further research is therefore necessary bringing together the different communities focusing on these issues to develop a common language, better define the threats and discuss potential ways forward in addressing risks.
A panel of government, private sector and technology leaders could be convened to conduct combined foresight analyses across technological domains, including AI, cyber- and biosecurity. With an aim toward understanding the convergence of high-impact biological events with dual-use technologies, this group could define a shared approach to prevention and mitigation, recommends weforum.
Foresight efforts should include cooperation with states affected by conflict. Experts in conflict prevention should partner with private sector actors and civil society to better tailor prevention strategies to the specific threats and ethical needs of vulnerable communities. Such efforts have already begun to emerge. For instance, start-ups and innovators at the UN and the Alan Turing Institute already collaborate to use AI for crowd-sourcing and forecasting emerging security risks.
Such “inclusive foresight” could equip countries and agencies with the tools to articulate scenarios from which risk prioritisation can emerge, particularly for conflict zones and develop responsible approaches to leverage emerging technologies for prevention.
References and Resources also include:
https://www.frontiersin.org/articles/10.3389/fbioe.2019.00099/full
https://www.weforum.org/agenda/2020/06/prevent-cyber-bio-security-threats-covid19-governance/
 International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis