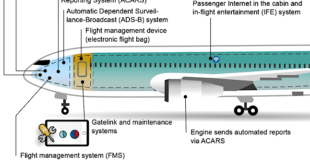
Cyberspace is understood as the fifth domain of warfare equally critical to military operations as land, sea, air, and space. Success of military operations in the physical domains is increasingly dependent on the availability of, and access to, cyberspace. The armed forces are reliant on cyberspace both as a user and as a domain to achieve defence and security missions. Modern defense platforms are at increasing risk of cyber-attack from sophisticated adversaries. These platforms do not currently provide the situational awareness necessary to identify when they are under cyber-attack, nor to detect that a constituent subsystem may be in a compromised state.
Our growing dependency on cyberspace has greatly increased the need for situation awareness—essentially, understanding your environment and accurately predicting and responding to potential problems that might occur. The systems and networks that operate in cyberspace have vulnerabilities that present significant risks to both individual organizations and national security. By anticipating what might happen to these systems, leaders can develop effective countermeasures to protect their critical missions.
Effective command and control requires a fundamental awareness of what’s occurring across the affected domain. With this awareness, negative situations can be recognized and managed as they occur. The concepts for doing this are rapidly evolving, and many U.S. government organizations are working to establish disciplined processes, enabling technologies, and management organization
EDA’s Cyber Situation Awareness Package (CySAP) project aims to integrate a group of technologies into a single platform to provide situation perception, understanding and future projection. It will provide military commanders with a cyber decision-support analysis tool to manage risks and cyber threats during the planning and execution phases of an operation. It will also enable headquarters’ staff to better visualise and interpret the threat landscape, as presented by the Security Operation Centre (SOC).
Cyber Situation Awareness
Cyber security situation refers to the global security status of the monitored network, the cyber-attacks suffered in a certain time window, and the effect to the total objective of network security. Generally, the security situational information consists of two aspects, the time dimension and the space dimension. To deal with the increased information security threats in large scale networks, many kinds of security devices have been used. These devices produce lots of security events. It is very difficult to obtain the security state of the whole network precisely when overwhelmed with excessive warning information. To address this problem, the concept of situational awareness is introduced into cyber security systems.
Endsley defined situational awareness as the perception of the elements in the environment within an amount of time and space, the comprehension of their meaning and the projection of their status in the near future . Endsley delineated situation awareness in three layers, namely, Perception, Comprehension and Projection. From a systemic point of view, situational awareness is applying appropriate mechanisms of assessment, evaluation, and inference, and so forth to generate understanding of the situation and dynamics of the situation.
The main idea of situational awareness in cyber domain is to analyze the surroundings in cyber infrastructure and to create certain events and visualizations for the purpose of efficient and fast decision-making. In simple words, CSSA can be described as the situational awareness applied for cyber security in a cyber infrastructure.
Currently, we’re focused squarely on building a tactical level of cyber situation awareness. This tactical understanding of events, or situations, in cyberspace is critical. However, senior leadership also needs higher levels of awareness so they can understand the impact of a situation on their organization’s ability to execute its operations.
To achieve cyber situation awareness at the operational level, the lower level details must be summarized and put into the perspective of the organization’s mission or business. It’s not a matter of simply aggregating all the tactical-level information available. Instead, status information must be correlated to the context of the mission or business, thus exposing the real impact to its operations. For example, what does it mean to the processing of Medicare reimbursement requests when 50 percent of the web servers are down due to a piece of computer malware?
At the strategic level, it’s important to be able to look well beyond simple incident data to identify threat actors, recognize trends in their activities, and expose their malicious objectives. This level of awareness is fundamental to engaging sophisticated adversaries in cyberspace and building effective plans to defend one’s organization, operations, and strategic objectives.
Cyber Situation Awareness Requirements
Cyber infrastructure is a term used broadly to describe computer based networked environments. A typical cyber infrastructure in practice would be an enterprise environment which normally comprises a collection of physical and virtualized infrastructures and both internal corporate network and the external internet. Cyber infrastructure may be divided as system infrastructures and information assets. System infrastructures refer to physical and hardware infrastructures, as well as software infrastructures, including operating systems, virtualization systems, database management systems, middleware, applications, and services.
Embodying the generic concept of situational awareness with the cyber security contexts, CSSA would have the following layers. Perception involves evidence gathering of the situations in the cyber infrastructure. . Each organizational unit has applications running on its own clients and servers and network devices such as intrusion detection/protection system (IDS/IPS), firewall, etc. information collected across organizational units is sent to a cyber security operation center.Perception is to get the knowledge of the elements in the networked environment such as alerts reported by intrusion detection systems, firewall logs, scan reports, as well as the time they occurred. This produces classified information with meaningful representations that offers the foundation for comprehension, projection and resolution.
The data pre-processing mainly involves cleansing, normalization and collation. Data cleansing may include duplicate elimination, data calibration and filtering of the raw data from security sensors, such as IDS, firewall, network and system log records, SIEM, and NetFlow, etc.
Pre-processing may include cleansing (e.g., duplicate elimination, data calibration, filtering/validation, etc.), normalization, collation, etc. Data validation mechanism is adopted to determine whether there is a successful attack. By comparing the conditions and the system configuration (e.g., OS version, services running, etc.) necessary for a successful attack, non-impact attack alert could simply be removed.
Finally, the security data will be normalized into a uniform format so as to be usable in the later stages of CSSA. Data fusion is one of the advanced stages in the upstream, which may be carried out according to Dempster-Sharer evidence theory.
CSSA at the downstream is concerned with the general processes of event processing and correlation analysis of various types of alert events from security sensors, sequential pattern mining and pattern analysis, and context inference and situational assessment and projection, and situational visualization.
For sequential pattern mining and pattern analysis, first, attack patterns are acquired through interactive knowledge discovery by applying frequent pattern mining algorithm, which helps discover the knowledge hidden in an event sequence. Then, the discovered frequent patterns and sequential patterns are transformed to the correlation rules of alert events. Finally, cyber security situation graph is dynamically generated
Comprehension involves the analysis of the evidences to deduce the exact threat level, type of attack and associated or interdependent risks. Comprehension utilizes a set of relevant techniques and procedures to analyze, synthesize, correlate and aggregate pieces of evidence data perceived in the cyber infrastructure.
Projection involves predictive valuation to address future incidents and resolution to mitigate the network situations. Projection is the ability to make future prediction or forecast based on the knowledge extracted from the dynamics of the network elements and comprehension of the situation.
Finally, projection into the future is enabled by using the representation of cyber infrastructure model in combination with semantic models. Semantic meaning of data and inference capabilities on the cyber infrastructure components and assets can be established based on context management, cyber infrastructure ontology and cyber security ontology.
Army gets prototype for cyber visualization tool
The U.S. Army now has a prototype for a new tool that allows commanders to visualize and understand the cyber terrain within their environment. Just as commanders must understand the obstacles and forces — friendly or otherwise — in their battlespace to make informed decisions, so too must they understand their cyber terrain, which they are currently unable to do from the command post.
The system, ordered in a $21 million contract in April with Research Innovation Inc., will allow the cyber and electromagnetic activities staff section to better visualize and plan cyber operations, which to date has been a heavily manual process. This is different than tools for the cyber mission force that feed up to U.S. Cyber Command and conduct remote operations on behalf of combatant commanders or in defense of the nation. This tool is specifically for ground-based brigade commanders to assess their terrain and risk in cyberspace as well as on the electromagnetic spectrum.
The goal is that the end user won’t see the actual Cyber SU product and will be able to work in their native environment on CPCE and see a cyber overlay of critical information in support of their mission,” said John Keenan, chief engineer for cyber with Product Manager Mission Command. “There’s a lot of work being done on the back end to make that happen, but from a user experience it doesn’t feel like we just threw another application at them.”
The official prototype was delivered to Program Executive Office Command, Control and Communications-Tactical following several user tests, an Aug. 2020 Army release said.The Senate, in a recent provision accompanying the annual defense policy bill, is looking to minimize funding for the program, arguing the effort is redundant when compared to another program under development for Cyber Command and the joint cyber force called Project IKE. However, IKE is designed to help visualize and plan cyber operations as opposed to aid understanding and decision-making of brigade commanders on the ground.
Soldiers from the 915th Cyber Warfare Battalion provided feedback for the first time on the Cyber SU prototype. Created in 2019, the battalion will consist of 12 teams that support brigade combat teams or other tactical formations, helping to plan tactical cyber operations for commanders in theater and unilaterally conduct missions in coordination with forces in the field. They conducted a three-day event on Fort Gordon, Georgia, at the end of June at the Cyber Battle Laboratory with remote participation from various personnel evaluating the software and providing feedback on how support the cyber and electromagnetic activities staff section and the commander.
For additional testing, Cyber SU will participate in Cyber Quest 2020, an annual technology experimentation at Fort Gordon that allows the Army to test technologies and concepts from industry to help solve anticipated problems. During the experiment, soldiers in a brigade operations center will use the system to perform a mission, allowing personnel on the cyber and electromagnetic activities staff section to use it in the decision-making process. Feedback from the event will help inform engineering release development operations with 3rd Brigade, 101st Airborne Division in October for continued development of the system, the Army said.
Cyber SU is slated to reach initial operational capability in fiscal 2022. Delivery will begin on Tactical Server Infrastructure hardware along with the latest CPCE software baseline. “Cyber Quest and follow-on DevOps with 3/101st in operational environments will prove out Cyber SU as a single [common operating picture] supporting commanders’ tactical decisions,” said Lt. Col. Scott Shaffer, product manager for Mission Command Cyber.
References and Resources also include:
https://www.c4isrnet.com/cyber/2020/08/14/army-gets-prototype-for-cyber-visualization-tool/
 International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis