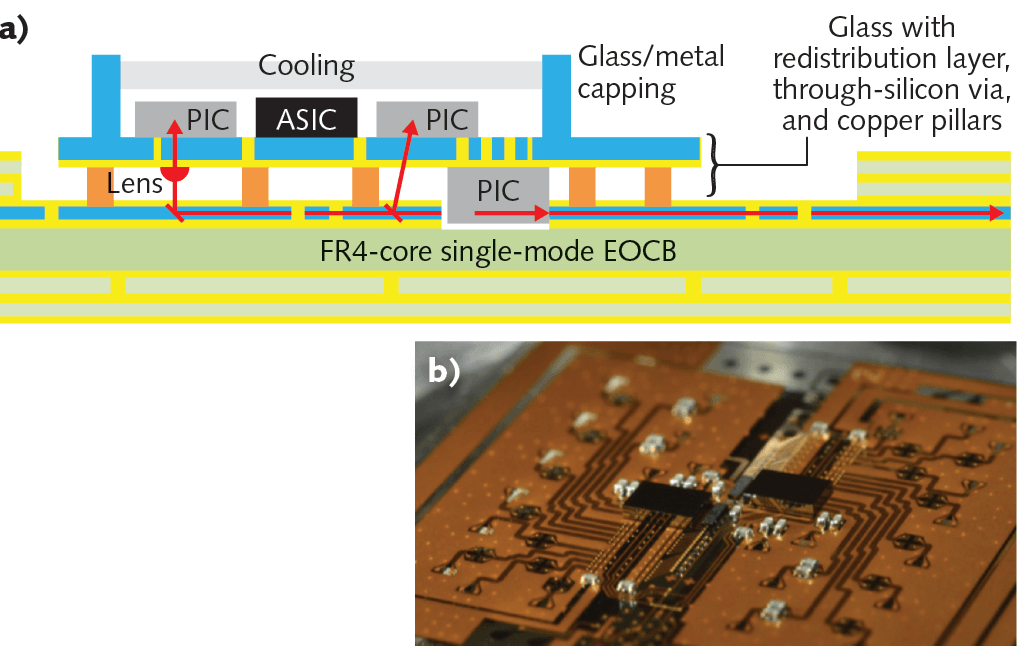
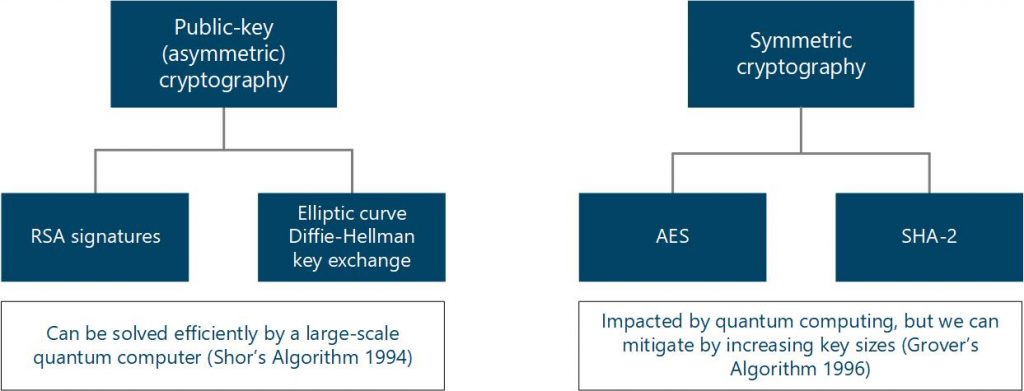
Quantum Entanglement advances enables Quantum Computers, high-speed ultra secure communications, high precision Quantum Sensors and Imaging

The extraordinary promise of quantum technology—depend on quantum “entanglement,” in which the physical states of two or more objects such as atoms, photons or ions become so inextricably connected that the state of one particle can instantly influence the state…