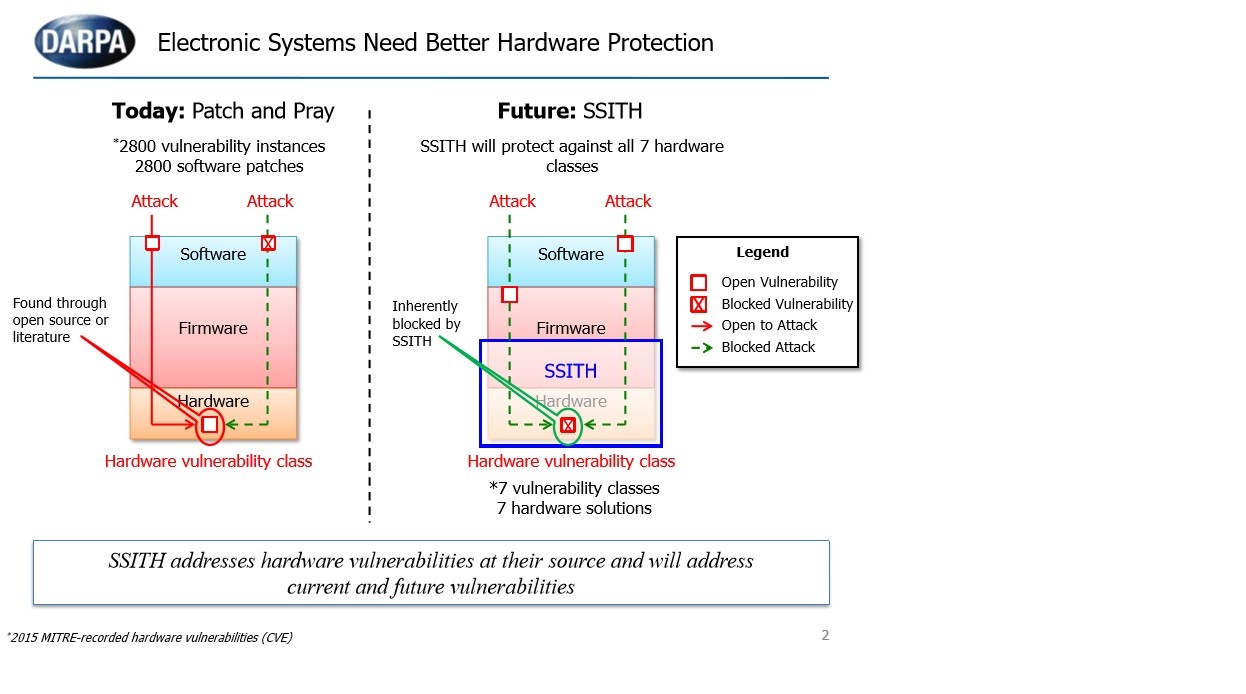
As 5G and IoT proliferation sweep across the planet, businesses and consumers are benefiting greatly from increased connectivity. However, this connectivity is also introducing greater risks and security concerns than ever before. As the Military and civilian technological systems, from fighter aircraft to networked household appliances, are becoming ever more dependent upon software systems, they are also becoming more vulnerable to hackers and electronic intruders. Electronic system security has become an increasingly critical area of concern for the DoD and the broader U.S. population. Attacks might include exploitable software bugs, the most common vulnerability, or hardware leaks, physical attacks, logical attacks, and remote and localized attacks.
IDST Pro Access Required
This analysis is part of IDST premium intelligence.
Subscribe to Continue ReadingAlready a member? Log in