In the ever-evolving landscape of modern technology, Radio Frequency Identification (RFID) has emerged as a game-changing solution for seamless and efficient product-tracking networks and military asset management. With the ability to revolutionize supply chains, logistics, and security systems, RFID is driving a paradigm shift in how smart products and military assets are monitored and tracked. In this blog, we explore the transformative power of RFID technology and its applications in large product-tracking networks and military asset tracking.
Understanding RFID Technology:
Most retail items we buy have a UPC bar code printed on them which serve as product fingerprints made of machine-readable parallel bars that store binary code. These bar codes help manufacturers and retailers keep track of inventory. They also give valuable information about the quantity of products being bought and, to some extent, the consumers buying them. However, these bar codes have the disadvantage of requiring scanning of each bar code on the item. Bar code is also a read-only technology, meaning that it cannot send out any information.
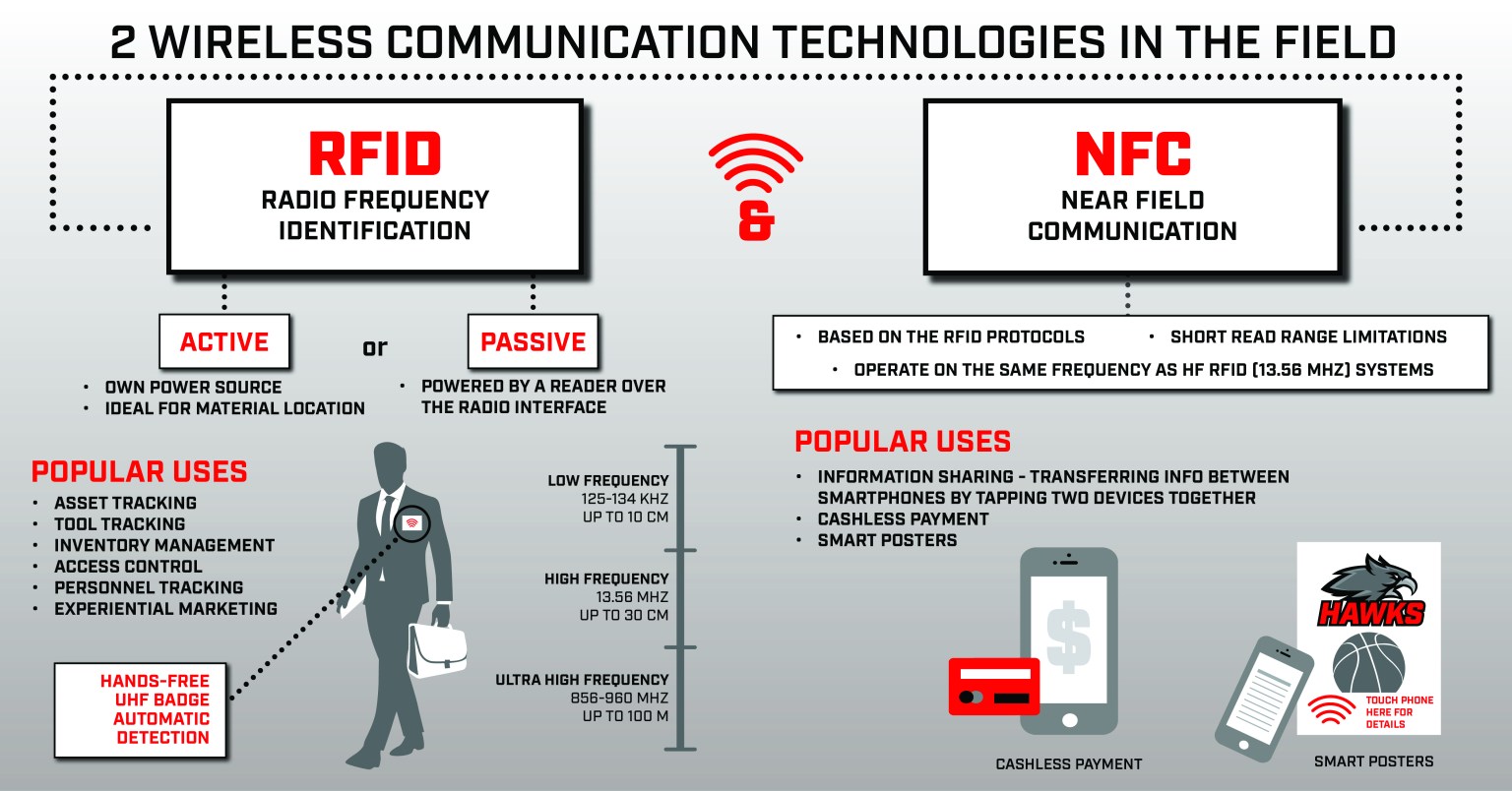
RFID (radio frequency identification) is a form of wireless communication to transfer data. Tagging items with RFID tags allows users to automatically and uniquely identify and track inventory and assets. RFID tags are an improvement over bar codes because the tags have read and write capabilities. Data stored on RFID tags can be changed, updated, and locked. RFID takes auto-ID technology to the next level by allowing tags to be read without a line of sight and, depending on the type of RFID, having a read range between a few centimeters to over 20+ meters.
In addition to retail merchandise, RFID tags have also been added to transportation devices like highway toll passcards and subway passes. Because of their ability to store data so efficiently, RFID tags can tabulate the cost of tolls and fares and deduct the cost electronically from the amount of money that the user places on the card. Rather than waiting to pay a toll at a tollbooth or shelling out coins at a token counter, passengers use RFID chip-embedded passes like debit cards.
For in-depth understanding on RFID technology and applications please visit: RFID: The Future of Tracking and Identification
Advantages of RFID in Large Product-Tracking Networks:
- Enhanced Inventory Management: RFID enables real-time and accurate inventory management, providing businesses with insights into product availability, stock levels, and expiration dates. This ensures efficient supply chain operations and reduces the risk of stockouts or overstocking.
- Optimized Logistics and Distribution: With RFID, the movement of products within a warehouse or distribution center can be automated, streamlining the entire process and minimizing human errors. This results in faster, error-free shipments and improved customer satisfaction.
- Product Authenticity and Anti-Counterfeiting: RFID tags can be embedded with unique identification codes and encrypted data, ensuring product authenticity and helping combat counterfeiting. This is particularly crucial for high-value products or pharmaceuticals.
- Traceability and Recall Management: In the event of a product recall, RFID provides a clear and efficient way to trace the affected products back to their source, enabling quick and targeted recalls, reducing waste, and enhancing consumer safety.
- Supply Chain Visibility: RFID offers end-to-end visibility into the supply chain, allowing businesses to track products from manufacturing to distribution, ensuring transparency and accountability throughout the process.
Empowering Military Asset Tracking:
RFID has come a long way from its first application of identifying airplanes as friend or foe in World War II. Not only does the technology continue to improve year over year, but the cost of implementing and using an RFID system continues to decrease, making RFID more cost-effective and efficient.
RFID technology has also found extensive use in military asset tracking, revolutionizing the management of critical military equipment and enhancing overall security and efficiency.
- Improved Asset Visibility: With RFID, military personnel can efficiently track and locate assets such as weapons, vehicles, and sensitive equipment in real-time. This significantly reduces the time and effort spent on manual inventory checks.
- Enhanced Security: RFID technology offers secure and tamper-proof asset identification, ensuring that only authorized personnel can access specific assets. This strengthens security measures and mitigates the risk of unauthorized access or theft.
- Maintenance and Lifecycle Management: RFID can be utilized to monitor the maintenance status and lifecycle of military assets, ensuring timely servicing and replacement. This extends the lifespan of assets and reduces maintenance costs.
- Mission Readiness and Deployment: RFID aids in streamlining mission planning and deployment by providing accurate data on asset availability and readiness. This enables military forces to respond quickly and effectively to dynamic operational requirements.
Technology
RFID is a contactless technology that uses radio frequency waves to identify and track objects or assets remotely. The system comprises three key components: RFID tags, RFID readers, and a central database or cloud-based system. RFID tags, equipped with a microchip and an antenna, are attached to products or assets. These tags emit radio signals containing unique identification information when they come within the range of RFID readers. The readers, strategically placed at various checkpoints, capture the signals, and the data is transmitted to the central database for real-time monitoring and analysis.
The earliest RFID tags were Inductively coupled RFID tags comprised of complex systems of metal coils, antennae, and glass and were powered by a magnetic field generated by the RFID reader. Then Capacitively coupled tags were introduced which used conductive carbon ink instead of metal coils to transmit data. The ink was printed on paper labels and scanned by readers. These were meant to be disposable tags that could be applied to less expensive merchandise and made as universal as bar codes. Both of these RFID tags aren’t used as commonly today because they are expensive and bulky.
Newer innovations in the RFID industry include active, semi-active and passive RFID tags. An active RFID tag has its own power source, often a battery. A passive RFID tag receives its power from the reading antenna, whose electromagnetic wave induces a current in the RFID tag’s antenna. There are also semi-passive RFID tags, meaning a battery runs the circuitry while communication is powered by the RFID reader.
RFID (Radio Frequency Identification) systems use Backscattering, a form of wireless transmission, which is based on modulated reflection of external RF signals. Whereas conventional radios generate their own signals, backscatter radios transmit data by making tiny changes to reflected signals. Instead, they simply reflect a radio signal transmitted by an interrogator and modulate the reflection by controlling their own reflection coefficient.
Since the source of the RF signal is external, such transmission does not require an ‘active’ radio transceiver, allowing devices to function in an extremely low power regime (under 10 𝜇𝑊). The power needed to operate the transmitter can be harvested from the external RF signal itself, and thus it is possible for such devices to be batteryless.
Every RFID system consists of three components: a scanning antenna, a transceiver and a transponder. When the scanning antenna and transceiver are combined, they are referred to as an RFID reader or interrogator. There are two types of RFID readers — fixed readers and mobile readers. The RFID reader is a network-connected device that can be portable or permanently attached. It uses radio waves to transmit signals that activate the tag. Once activated, the tag sends a wave back to the antenna, where it is translated into data.
The transponder is in the RFID tag itself. These tags can store up to 2 kilobytes of data and are composed of a microchip, antenna and, in the case of active and semi-passive tags, a battery. Low-power, embedded non-volatile memory plays an important role in every RFID system. Tags can be read-only or read-write, where data can be added by the reader or existing data overwritten. RFID tags typically hold less than 2,000 KB of data, including a unique identifier/serial number.
Data stored within an RFID tag’s microchip waits to be read. The tag’s antenna receives electromagnetic energy from an RFID reader’s antenna. Using power from its internal battery or power harvested from the reader’s electromagnetic field, the tag sends radio waves back to the reader. The part of an RFID tag that encodes identifying information is called the RFID inlay. The reader picks up the tag’s radio waves and interprets the frequencies as meaningful data.
The read range for RFID tags varies based on factors including type of tag, type of reader, RFID frequency, and interference in the surrounding environment or from other RFID tags and readers. Active RFID tags have a longer read range than passive RFID tags due to the stronger power source. Passive RFID tags rely entirely on the reader as their power source. These tags are read up to 20 feet (six meters) away, and they have lower production costs, meaning that they can be applied to less expensive merchandise.
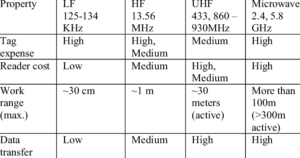
There are three main types of RFID systems: low frequency (LF), high frequency (HF) and ultra-high frequency (UHF). Microwave RFID is also available. Frequencies vary greatly by country and region.
Future trends
When the RFID industry is able to lower the price of tags, it will lead to a ubiquitous network of smart packages that track every phase of the supply chain. Store shelves will be full of smart-labeled products that can be tracked from purchase to trash can. The shelves themselves will communicate wirelessly with the network. The tags will be just one component of this large product-tracking network.
MIT’s Auto-ID Center is working on an Electronic Product Code (EPC) identifier that could replace the UPC. Every smart label could contain 96 bits of information, including the product manufacturer, product name and a 40-bit serial number. Using this system, a smart label would communicate with a network called the Object Naming Service. This database would retrieve information about a product and then direct information to the manufacturer’s computers.
The information stored on the smart labels would be written in a Product Markup Language (PML), which is based on the eXtensible Markup Language (XML). PML would allow all computers to communicate with any computer system similar to the way that Web servers read Hyper Text Markup Language (HTML), the common language used to create Web pages.
The United States retail market is on the cusp of embracing a major implementation of RFID technology through payment systems that use Near Field Communication. These are the credit cards of the future. NFC technology is promising because it presents the next evolution of convenient payment with an added layer of security. Some credit cards have NFC chips embedded in them and can be tapped against NFC payment terminals instead of swiped, which eliminates the possibility that someone could skim your data via the magnetic strip. Near Field Communication devices can read passive RFID tags and extract the information stored in them. NFC and RFID technologies have huge futures ahead of them in the retail world, but security remains a common concern.
Military Applications
The U.S. military is increasingly relying on RFID technology to ensure critical equipment and supplies are in the right place at the right time, as well as to help ensure the security of valuable or sensitive materials and equipment. In addition, RFID tags and readers are also used to secure military supplies en route.
For the DoD, the benefits include: Improved asset tracking, Replacement of manual procedures, Improved labor productivity, Improved acceptance and receipt; and Automated acceptance and receipt
RFID readers are at warehouse doors and other receiving points in Hawaii naval installations. The Navy has not only made each RFID tag transaction information visible to its customers, but they have implemented interfaces between RFID technology and naval distribution systems. The successful progress of these improvements has led to analysis regarding whether RFID on vessels for onboard supply processes can be safely used within the Navy’s hazards of electromagnetic radiation to ordnance (HERO). If so, detailed asset tracking and visibility will be possible for shipboard supply.
Momentum for RFID built within the Air Force after a 2018 case in which a machine gun disappeared from the 91st Security Forces Group, which guards an installation that houses nuclear-tipped missiles. Authorities recovered the weapon, but the incident reverberated across the service.
Passive RFID tags are used for managing materials related to nuclear weapons. Each item requires two-person identification and documentation, and passive RFID is helping with these intensive item management inventory requirements. For example, inventory of an entire warehouse can now be completed in minutes with the use of handheld terminals. Items are tracked when they are moved from one area to another, one building to another, or one installation to another. Automatic alerts provide notifications when items do not arrive by their expected delivery time.
Army using passive RFID to track parachute processing from warehousing, inventory, packing, shipping, jumping and recovery. Implemented in the early 2000s, this has helped eliminate manual methods that are error-prone, labor-intensive and vulnerable to malicious tampering.
Breakthrough Enables Battery-free Smart Tag Technology
Researchers at the University of California, San Diego article have developed a new technology that can turn smartphones into RFID (Radio Frequency Identification) readers. The new technology developed by the UC San Diego researchers involves using the sensors and antennas built into smartphones to detect and read RFID tags. This allows smartphones to be used as low-cost, portable RFID readers, opening up new possibilities for a wide range of applications.
The technology works by using the smartphone’s existing NFC (Near Field Communication) capability to detect RFID signals. The researchers developed a new algorithm that enables the smartphone to detect and read RFID tags from a distance of several meters, rather than the typical distance of a few centimeters for NFC.
The custom chip, which is roughly the size of a grain of sand and costs only a few pennies to manufacture, needs so little power that it can be entirely powered by LTE signals, a technique called RF energy harvesting. The chip turns Bluetooth transmissions into WiFi signals, which can in turn be detected by a smartphone with that specific software update.
The work harnesses breakthroughs in backscatter communication, which uses signals already generated by your smartphone and re-directs them back in a format your phone can understand. Effectively, this technique uses 1000 less power than state of the art to generate WiFi signals These advances have enabled very low-power communication between components of the Internet of Things and hardware such as WiFi or Bluetooth transceivers, for applications such as on-body sensors or asset trackers.
Currently, state of the art backscatter modulation requires two external devices: one to transmit and one to receive and read the signals. This conference paper presents the first backscatter integrated circuit that can enable wireless communication and battery-less operation coming from a single mobile device.
“This approach enables a robust, low-cost and scalable way to provide power and enable communications in an RFID-like manner, while using smartphones as the devices that both read and power the signals,” said Patrick Mercier, one of the paper’s senior authors and a professor in the Department of Electrical and Computer Engineering at the University of California San Diego.
According to the researchers, the technology could be used in a variety of settings, such as in retail stores to track inventory, in healthcare to monitor medical equipment, and in transportation to track goods and vehicles. It could also be used by consumers to track personal items, such as luggage or keys.
Overall, this technology has the potential to significantly increase the accessibility and utility of RFID technology, making it more accessible and cost-effective for a wide range of applications.
Vulnerabilities
Like most products, RFID tags and readers can be reverse engineered to Steal Information and/or Gain Access. However, it would take a lot of knowledge about the protocols and features to be successful. Hackers would take apart the chip in order to find out how it works in order to receive the data from the IC.
According to leading experts1, power analysis attacks can be mounted on RFID systems by monitoring the power consumption levels of RFID tags to Steal Information and/or Gain Access. Researchers stumbled upon this hacking technique when studying the power emission levels in smart cards, especially in the difference in power levels between a correct passcode and an incorrect passcode.
A man-in-the-middle attack happens during the transmission of a signal. Like eavesdropping, the hacker listens for communication between a tag and reader and then intercepts and manipulates the information. The hacker diverts the original signal and then sends false data while pretending to be a normal component in the RFID system.
They are also vulnerable to cloning and spoofing which are usually done back to back. Cloning is duplicating data from a pre-existing tag, and spoofing is then using the cloned tag to gain access to a secured area or item. Because the hacker has to know the data on the tag to clone it, this type of attack is mainly seen in access or asset management operations.
According to some sources, RFID tags currently do not have enough memory capacity to store a virus; but in the future, viruses could be a serious threat to an RFID system. A virus programmed on an RFID tag by an unknown source could cripple an RFID system when the tagged item is read at a facility. When read, the virus would transfer from tag to reader and then to a company’s network and software – bringing down connected computers, RFID components, and networks.
When embedded in military guns, RFID tags can trim hours off time-intensive tasks, such as weapon counts and distribution. Outside the armory, however, the same silent, invisible signals that help automate inventory checks could become an unwanted tracking beacon.
Which is why a spokesman for the Department of Defense said its policymakers oppose embedding tags in firearms except in limited, very specific cases, such as guns that are used only at a firing range — not in combat or to guard bases. “It would pose a significant operations security risk in the field, allowing an adversary to easily identify DOD personnel operating locations and potentially even their identity,” Pentagon spokesman Lt. Col. Uriah Orland told AP.
The field tests showed how tags inside weapons can be quickly copied, giving would-be thieves in gun rooms and armories a new advantage. And, more crucially, that even low-tech enemies could identify U.S. troops at distances far greater than advertised by contractors who install the systems.
The military systems can also face Denial of Service attacks from adversaries, resulting in RFID system failure.. These attacks are usually physical attacks like jamming the system with noise interference, blocking radio signals, or even removing or disabling RFID tags.
RFID Threats and Security
Radio Frequency Identification (RFID) technology is widely used for tracking and identifying items in various industries, including retail, logistics, and healthcare. However, traditional RFID tags face significant security threats, such as counterfeiting and tampering. A common vulnerability is that counterfeiters can peel off RFID tags from genuine items and reattach them to fake products, undermining the integrity of supply chains and product authenticity.
MIT’s Innovative Solution
To address these vulnerabilities, MIT researchers have developed a new type of cryptographic ID tag that leverages terahertz waves, creating an antitampering solution that is both small and cost-effective while ensuring high security.
Key Features:
- Antitampering Mechanism: The ID tag includes microscopic metal particles mixed into the adhesive. When exposed to terahertz waves, these particles form a unique pattern on the item’s surface, similar to a fingerprint. This pattern is destroyed if the tag is removed and reattached, ensuring the item’s authenticity remains intact.
- Technology and Detection: The tag, measuring approximately 4 square millimeters, is detected using terahertz waves. A machine-learning model identifies tampering by comparing glue pattern fingerprints with over 99% accuracy.
- Cost and Size Benefits: The tag is inexpensive to produce, making it suitable for large-scale supply chains. Its tiny size allows it to be attached to items too small for traditional RFIDs, such as specific medical devices.
- Security and Authentication: Vendors can take an initial reading of the tag and store the data in the cloud for future verification. This system is highly secure because the unique pattern formed by the metal particles in the glue is impossible to duplicate once the tag is tampered with.
- Broader Implications: This technology demonstrates the potential of the terahertz spectrum beyond broadband wireless, showing applications in ID, security, and authentication.
Professor Ruonan Han and graduate student Eunseok Lee led the research, highlighting the tag’s potential to enhance security in various fields by ensuring that items remain tamper-proof throughout their lifecycle. Han emphasized that the application of terahertz waves could significantly extend beyond current uses, opening up new possibilities in secure identification and authentication.
By addressing the common vulnerabilities of traditional RFID tags, MIT’s terahertz-based ID tags offer a promising solution for industries requiring reliable and tamper-proof identification technologies.
RFID Market
The Market for RFID Tags was valued at US$ 12,345.2 Million in 2022, and it is anticipated to have grown to US$ 31,803.3 Million by the end of 2033. The market for RFID tags is estimated to
evaluate to US$ 13,271.1 Million in 2023 and is estimate to grow at a CAGR of 9.1% from 2023 to
2033.
The RFID (Radio Frequency Identification) tags market is a rapidly growing industry that is driven by the increasing demand for automated data collection, tracking, and inventory management in various industries such as retail, healthcare, transportation, logistics, and manufacturing.
The key drivers fueling the growth of this market include growing market competitiveness leading to availability of cost-effective RFID solutions, high returns on investment, and increasing regulations and government initiatives for various industries.
The RFID tags consisted 20% of the global RFID market. The tag segment of the RFID market, by product is projected to grow at a higher CAGR during the forecast period. Tags are the most widely used components in the RFID market. These devices are attached to several industrial and commercial assets, including manufacturing equipment and other industrial machinery, industrial materials, products, retail products, inventory, logistic containers, labels on products and groups of products, IV pumps, ECGs, and wheelchairs. The large-scale use of tags and ease of use for tracing any kind of asset is the major reason for the adoption of RFID tags. This could drive the demand for RFID tags in years ahead
The passive tags segment of RFID tag market, by tag type, is expected to register higher CAGR during forecast period. Passive tags do not require an external power source. These are inexpensive and smaller, and easier to manufacture than active tags. Passive RFID tags have various applications and are commonly used to track goods in pharmaceuticals, retail, supply chain, enterprise, and other industries. Zebra Technologies, Avery Dennison, Alien Technology, Omni-ID, HID Global, Honeywell, and Mozix are some of the leading providers of passive RFID tags. With the increasing penetration of passive tags as RAIN RFID frequency, the market for these tags is expected to grow at the highest CAGR during the forecast period.
UHF tags can be classified into 2 types on the basis of frequency range: passive tags and active tags. UHF passive RFID tags offer the longest read range and highest reading speed among all passive tags. These tags have a frequency range of 860–960 MHz. UHF passive tags can be read from an average distance of about 5–6 meters; larger UHF passive tags can read more than 30 meters in ideal conditions. UHF active tags have 2 major operating frequencies: 433 MHz and 2.45 GHz. These tags have the longest read range among all tags, i.e., around 150 meters. These tags are largely used for applications such as asset tracking, asset counting, inventory management, supply chain management, vehicle tagging, and manufacturing equipment and product part tagging. Due to rising adoption of UHF tags in these applications, the market for UHF tags is high and is expected to be the same during the forecast period.
The logistics and supply chain application to hold largest share of RFID tag market during the forecast period
The dominance of this segment is due to the high adoption of tracking systems by logistics organizations to track and monitor their cargo in transit through air, road, or marine. RFID solutions help industries optimize their supply chain by better managing warehouse inventory, tracking shipments, and streamlining the best route for the supply chain. Supply chain companies are facing major issues in ensuring that the right product is delivered at the right location at the right time. Such companies are deploying RFID tags on containers and freight systems to have real-time visibility of the cargo. The involvement of governments in the global supply chain has led to the use of RFID tags on freight to locate and track them for secure transport. These activities are expected to drive the growth of the RFID tag market for logistics and supply chain application.
Americas is projected to hold largest share of RFID tag market
The RFID tags market in North America held 25.9% which is the uppermost market share in the
worldwide landscape in 2022 and is projected to retain its position within the forecast period.
The high adoption of RFID systems in the US is a major factor that has led to the prominent position of the Americas in the RFID market. Retail, manufacturing, transportation, logistics and supply chain, animal tracking, healthcare, defense, and IT asset tracking are the major applications for the RFID tag market in the US as well as throughout the Americas. The use of RFID is high in supply chain monitoring for tracking assets in real time. Various hospitals in the US are using RFID tags for applications such as equipment tracking, patient monitoring, and other tracking tasks. These developments are expected to drive the growth of the RFID tag market in the region.
The demand for RFID tags in the Europe region it held around 20.5% of the market in 2022.
India’s increasing regulations are likely to boost the RFID tags market in the country. The Indian
government has been implementing several regulations and initiatives in recent years to promote the use of RFID technology in various sectors.
For example, in 2020, the Indian government announced the National RFID Program, which aims to provide a unique identification number to every livestock and fish in the country using RFID tags. This program is expected to help improve the management and monitoring of livestock and fish, as well as prevent diseases and enhance food safety.
In addition, the Indian government has also mandated the use of RFID tags in toll plazas across the country to improve traffic management and reduce congestion. This initiative has been successful in reducing travel time and increasing the efficiency of toll collection. The increasing adoption of RFID technology by various industries, the RFID tags market in India is expected to grow significantly in the coming years. The Indian market will grow with CAGR of 12.6% over the forecasted period.
Avery Dennison (US), Zebra Technologies (US), Honeywell (US), NXP Semiconductors (Netherlands), Impinj (US), HID Global (US), GAO RFID (Canada), Identiv (US), Invengo (China), and Nedap (Netherlands) are the key players in the global RFID market. These players are increasingly undertaking strategies such as product launches and development, expansions, partnerships, collaborations, and acquisitions to increase their market share
Market Developments
In August 2021, HID Global has announced that it has acquired Omni-ID, a top producer of RFID tags and industrial internet of things hardware components for uses such as passive and active tagging, tracking, monitoring. The acquisition strengthens HID’s position in China and India and extends its market dominance in RFID technology
In July 2022, The Zebra Technologies Corporation has announced that BE Switch craft has
adopted Zebra’s radio frequency identification (RFID) solution to obtain real-time insight into
its financial data and manufacturing process to help it better meet the expectations of its
customers.
In November 2022, Impinj, Inc. has announced the new Impinj M780 and M781 RAIN RFID tag
chips, Impinj M700 series’ first expanded memory chips. These brand-new tag chips are
intended to support businesses that control product shelf life, cut waste, and adhere to rules in
the medical, food, and industrial manufacturing sectors.
In March 2023, Smart Spaces has collaborated with HID to add an employee documentation to
Apple Wallet and providing a safest and easiest way for workforce to enter buildings.
Employees and staff in the building can now easily and securely enter offices with a tap of their
iPhone or Apple Watch by adding their employee badge to Apple Wallet.
Overcoming Challenges and Looking Ahead:
While RFID has proven to be a transformative technology, there are still challenges to address, such as tag readability in certain environments and ensuring data security. However, ongoing research and innovation are continuously improving RFID systems, making them more robust and secure.
Looking ahead, the future of RFID holds immense promise. As technology advances, we can expect even more sophisticated RFID solutions that will drive further efficiency, transparency, and security in large product-tracking networks and military asset management. From supply chain optimization to safeguarding critical military assets, RFID is poised to play a vital role in shaping the future of smart product tracking and military logistics. As businesses and military forces worldwide embrace the potential of RFID, we can anticipate a world of connected efficiency and enhanced security, propelling us into a new era of intelligent tracking and management systems.
References and Resources also include:
https://www.marketsandmarkets.com/PressReleases/radio-frequency-identification.asp
https://electronics.howstuffworks.com/gadgets/high-tech-gadgets/rfid.htm