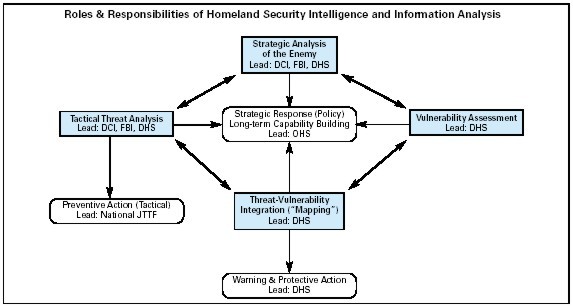
Introduction In an ever-changing world, security concerns have become paramount, with terrorism posing a significant threat to global stability and peace. To safeguard our future, we must adopt proactive measures to prevent acts of terror rather than simply reacting to their consequences. Early warning systems and advanced technologies have emerged as powerful tools in the…